The xXLecXx Ransomware is a computer virus of unknown origin that encrypts user data and extorts the victims for a ransomware fee, affected computers can be restored by reading our removal guide.
Manual Removal Guide
Recover .xXLecXx Ransomware Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How Does xXLecXx Ransomware Infiltrate the System?
xXLecXx Ransomware samples can be delivered by different means. One of the most common strategies is the creation and coordination of email spam campaigns that feature social engineering tricks. The aim of the hackers is to make the victims infect themselves with the xXLecXx virus by opening file attachments or links inserted in the body content. The messages pose as being sent by a legitimate company or government institution and is usually done by designing templates and inserting graphics and text that resemble the real companies.
The xXLecXx Ransomware payload can also be hosted on hacker-controlled or hacked download sites that may resemble legitimate sources. Based on the infection plan the xXLecXx virus code can be bundled in software installers or documents.
Other methods include direct hacker attacks, browser hijacker deployment and automated software vulnerability attacks.
Related: D2+D Ransomware, Clouded Ransomware
Infection Flow of xXLecXx Ransomware
Security analysts detected a new computer virus of unknown origin called the xXLecXx ransomware. During the initial analysis they found no code obtained from any of the well-known malware families. This means that the hacker or hacker collective behind it programmed it themselves.
It is a basic threat that contains only an encryption engine that is automatically started after the infection has been initiated. At the moment the captured xXLecXx virus samples were found to be in a testing phase. This means that the currently released attack campaign cannot effectively process the user and system data. We suspect that any follow-up updates will remedy the situation and the xXLecXx Ransomware will cause devastating effects on the compromised computers.
Typically viruses like the xXLecXx Ransomware target system and user data based on a predefined list of file type extensions. In the majority of cases this includes the most widely used files: documents, archives, backups, photos, videos, music, configuration files and etc. Depending on the configuration a mark extension can be used to signal the processed data – for example .xXLecXx. The xXLecXx virus can also use other generic extensions such as locked, encrypted and so on.
When the encryption process is complete the xXLecXx Ransomware a lockscreen is instituted on the victim computer. It prohibits ordinary interaction and shows the ransomware message designated by the hacker behind the virus. It reads the following:
Your files are encrypted with xXLecXx Ransomware
Your files have been encrypted by xXLecXx Ransomware.
You cannot access your PC right now. You have 2 options
1. We delete all your files
2. You pay us 150$ USD and we decrypt all your files.
The choice is yours. If you choose option 2, click the button below, (What to Do) and pay us $150 USD and get a decrypt code.
[What to Do]
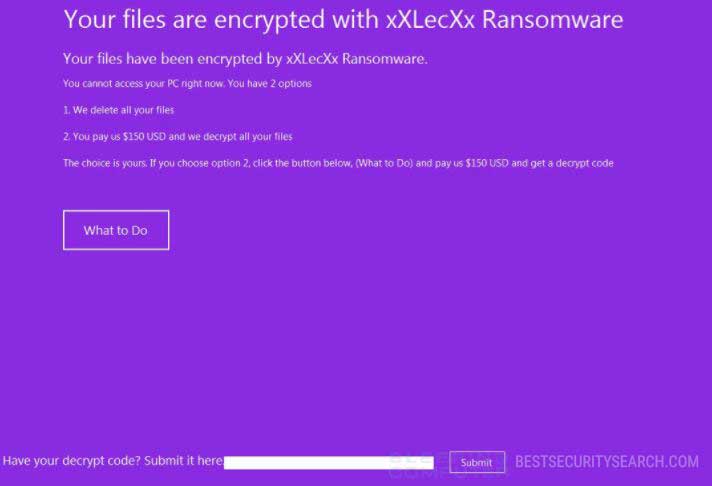
The hackers use a common blackmail strategy by explaining that the victims have been infiltrated by the xXLecXx Ransomware. They request the sum of 150 US Dollars however the criminals have not specified the payment method.
A future update of the xXLecXx virus will probably feature a working encryption process and a new note detailing how the payment is done. We suspect that the hackers are going to insist on using the Bitcoin digital currency as all transactions done with it cannot be traced and remain anonymous. Virtually all malware like the xXLecXx virus use this payment method.
The victims should not pay if they are infected with a virus such as the xXLecXx Ransomware. A quality anti-spyware solution can restore the affected machines and with the use of a professional-grade data recovery product the files can be recovered.
Remove xXLecXx Ransomware and Restore Data
WARNING! Manual removal of xXLecXx Ransomware requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
xXLecXx Ransomware – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
-
– Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
-
– Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover xXLecXx Ransomware Files
WARNING! All files and objects associated with xXLecXx Ransomware should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD xXLecXx Ransomware Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
-
– Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



