The .sVn virus is the newest iteration of the Jaff ransomware family. The malware encrypts user data and renames it with the .sVn extension. To learn more about it and how to remove existing infections, restore your computer and protect yourself, continue reading our detailed removal instructions.
Manual Removal Guide
Recover .sVn Virus Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How Does .sVn Virus Infiltrate the System?
The captured .sNv virus samples target mainly English-speaking users across the world. The analyzed Jaff ransomware criminal servers that are associated with this iteration are hosted in the United States of America and Canada among other countries. They may relay the data over to other computers and server mainly as gateways according to some scenarios.
The primary way of infecting computer users with the .sVn virus is by using a large-scale email spam campaign. It is coordinated by the hackers behind the updated strain of the Jaff ransomware.
The current .sVn virus campaign is powered by a botnet attack using compromised email servers and automatically generated identities based on predefined templates.
The emails themselves contain random subject titles such as “Message from KM_C301” or “Invoice 1040” with no body contents. The .sVn virus is contained in a file attachment that bears a random name with the .zip attachment. Some of the simpler anti-virus cannot detect malware found in archives. This makes it possible for the .sVn virus to remain undetected and infect computers once the payload file is extracted and executed.
Other infection methods include the use of browser hijackers to reditect the victims to third-party hacker-controlled sites. They modify important settings like the default home page, search engine and new tabs page and endanger their privacy by downloading data such as any stored cookies, passwords, account credentials, history, bookmarks and etc. The hijackers are a popular tool for distributing various types of viruses, especially ransomware like this one.
The criminals rely on the fact that the .sVn virus can be bundled in various payloads including software installers and office documents. The hackers include scripts that install the malware when the victims interact with them.
Computer criminals can opt to launch direct attacks against hackers using automated software. This is done by looking for outdated applications and exploiting the discovered weaknesses. This is why we recommend that all users update all installed software as soon as an update is released.
Related: BlueHowl Virus, Amnesia2 Virus
Infection Flow of .sVn Virus
Security experts detected a new ransomware that belongs to the Jaff malware family. The .sVn virus has been detected in an ongoing attack campaign against users worldwide.
This new Jaff ransomware version follows the same behavior patterns. Upon infection with the .sVn virus the core engine starts to encrypt a predefined list of file type extensions. It can be customized to reflect the targets, but in most cases viruses like this one seek to encrypt as many of the most popular data as possible: documents, archives, backups, videos, photos, music, databases and etc. They are then marked with the .sVn extension.
The .sVn virus is able to monitor the registry for any user or applications changes that are being done and prevents any manual removal attempt. In addition it is able to relay all network traffic through a hacker-controlled proxy server by manipulating the browser settings. This makes it possible for the hackers to carry out complex identity theft attacks as well as processing any data found on the victim computers.
.sVn virus is able to prevent modifications made by the users or applications to the binary files during the malicious processes.
The experts discovered that the ransomware code is able to retrieve information about the language and regional settings. This may be used in the future to display a ransomware message in the language used by the victims.
During the initial steps the .sVn virus scans the compromised machines and generates a list of all installed applications. It is then sent to the remote attackers via their network servers.
When all data has been processed the wallpaper is changed to a white background showing the ransomware message with black letters. It reads the following:
Your decrypt ID: 0962004742
Files are encrypted! To decrypt flies you need to obtain the private key.
The only copy of the private key, which will allow you to decrypt your files, is located
on a secret server in the Internet.Use this Link: http://rktazuzi7hbln7sy.tor2web.cf
If the link does not work:
1. You must install Tor Browser:
https://www.torproject.org/download/download-easy.html.en…..
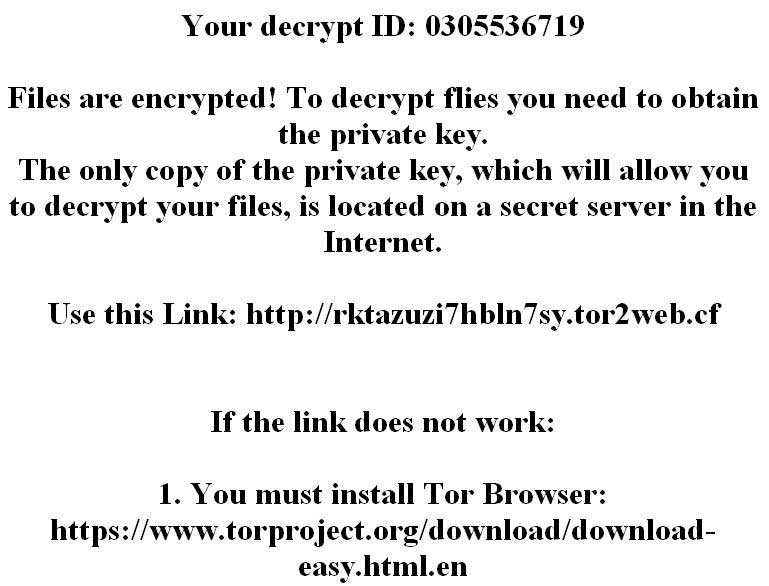
The ransomware note itself is written in a “!!!!README_FOR_SAVE FILES.txt” file. Like previous versions of the Jaff malware family the .sVn virus assigns an unique ID to each compromised machine. It is calculated based on harvested system information that may include private data as well.
To protect itself from detection by several system utilities the .sVn virus automatically deletes log files found in the Windows system directory.
This is a follow-up update of the Jaff ransomware family. As an updated versions there are several things that we must take in account when discussing the dangers of the infection:
- It Contains Updated or Modified Code – The .sVn virus uses the Jaff ransomware code but modifies it so that new features and additions are present. Depending on the sample the victims may find that some software that can remedy an attack with the core threat may not work with this virus. A completely new signature needs to be created that reflects the new changes. This is why we recommend the use of a quality anti-spyware solution.
- The .sVn Virus Has a Distinct Identity – The updated Jaff ransomware strain features a new ransom note and extension, as well as other changes that make it a distinct threat of its own.
- Massive Spread Campaign – The hackers utilize a large-scale attack campaign to infect as many targets as possible.
We suspect that an updated version might contain other components such as a Trojan module. It will allow criminals not only to process valuable information, but also to retrieve files of their choice and control the hacked machines at will.
Remove .sVn Virus and Restore Data
WARNING! Manual removal of .sVn Virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
.sVn Virus – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
-
– Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
-
– Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover .sVn Virus Files
WARNING! All files and objects associated with .sVn Virus should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD .sVn Virus Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
-
– Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



