New distribution campaign of Crysis ransomware has been detected. It implements RDP brute-force attacks to compromise the victim’s system. Targets of the new campaign are the computers of businesses in Australia and New Zealand.
The troublesome CrySiS ransomware was first spotted earlier this year. It can encrypt over 185 file types utilizing a combination of two strong encryption algorithms RSA and AES which makes its decryption almost impossible for now. Furthermore, it modifies the registry entries and enables automatic execution at every startup. All backups, as well as all shadow volume copies, are deleted once CrySiS infects the computer. It has the ability to scan and encrypt files on all drives including removable drives.
Cyber criminals apply different distribution techniques to infect systems with CrySiS cryptovirus. It is reported to be spread mainly through spam emails. It could be hidden in malicious attachments or in presented links to compromised websites.
CrySiS Now Uses RDP Brute-Force Attacks to Infect Systems
Apparently, the development of CrySiS ransomware is in progress. According to a report by the security researchers from Trend Micro now, the threat is spread in another way. The crooks are trying to launch brute-force attacks through unsecured open RDP ports. In case they succeed to guess the exposed computer’s admin password, they install the CrySiS ransomware on the device. Moreover, whenever it is possible they also spread it to other computers on the same network. This could happen either by leaving the malicious payloads of CrySiS ransomware on other connected devices like printers and routers or by brute-force attacks to nearby computers. Thus the crooks may spread the ransomware and infect other users. Eventually, even after the removal of the ransomware from the computer, the attackers could regain the access and re-infect the system. CrySiS is not the first ransomware to use RDP brute-force attack for infection. Another ransomware known to use this technique is DMA Locker.
The newly discovered infection vector of CrySiS ransomware has been spotted in attacks against businesses in Australia and New Zealand.
To mitigate the risk of infection admins who manage the remote desktops are advised to close RDP access if possible, or otherwise change the RDP port to a non-standard port. Regular backups are of utmost importance. Trend Micro specialists also advise:
Updating and strengthening RDP credentials as well as implementing two-factor authentication, account lockout policies and user permission/restriction rules can make them more resistant to brute force attacks. Ensuring that connected devices are securely wiped during cleanups can mitigate the risks of further damage, while utilizing encryption channels can help foil attackers from snooping on remote connections. Keeping the RDP client and server software up-to-date can also prevent potential vulnerabilities in RDPs from being exploited.
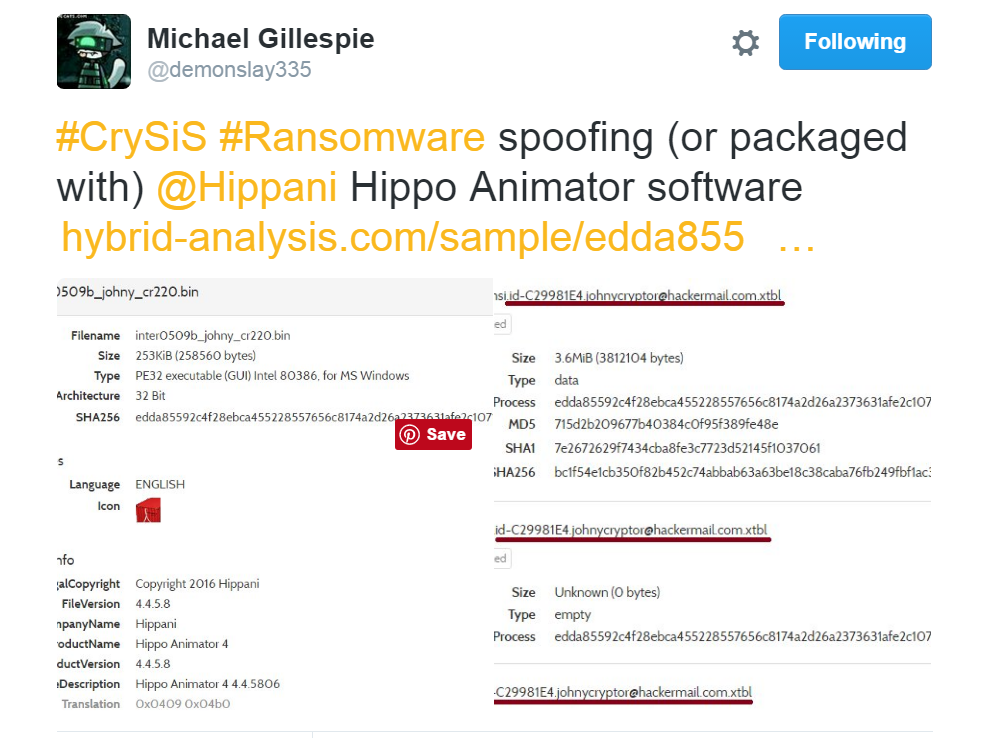
CrySiS Ransomware in Hippo Animator Software
Another interesting information that we came across concerning CrySiS ransomware distribution is that the threat can be packaged with Hippo Animator software. The information originates from a tweet made by the ransomware hunter Michael Gillespie – @demonslay335.