CrySiS belongs to the group of ransomware. It penetrates into the system then creates an executable file, infects the system, encrypts all important data and demands a payment. CrySiS ransomware’s encryption method is a mixture of RSA and AES-128 algorithms. It adds .CrySiS file extension to the encrypted files and changes the desktop wallpaper by setting a ransom note instead.
Now let’s look at the threat in detail and determine what should be done in case of infection.
| Name |
Crysis Ransomware |
| File Extensions |
.CrySiS |
| Ransom |
Varies |
| Solution #1 |
CrySiS ransomware can be removed easily with the help of an anti-malware tool, a program that will clean your computer from the virus, remove any additional cyber-security threats, and protect you in the future. |
|
Solution #2 |
CrySiS Ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
CrySiS may be spread through various distribution methods, the most common infections are through spam email campaigns. |
CrySiS Ransomware Specifics
Once CrySiS ransomware has infiltrated the system an executable file is created. The ransomware may create the executable file at random location and name it with various signs. However, one of CrySiS specific actions is creating a file with name “Skanda.exe” in %LOCALAPPDATA% folder.
This crypto-virus may also modify some values in Windows Registries.
→
HKLM/Software/Microsoft/WindowsNT/CurrentVersion/Winlogon/Shell
HKLM/Software/Microsoft/Windows/CurrentVersion/Run/
Modifications of values in Run folder result in automatic start of the ransomware every time the Windows OS is booted.
Commonly, the files in the following locations are encrypted by CrySiS ransomware:
- %TEMP%
- %WINDIR%\System32
- %localappdata%
- %UserProfile%\Local Settings\Application Data
- %userprofile%\downloads
All files that have one of the mentioned extensions below will be encrypted by CrySiS ransomware once it infects the system.
One of CrySiS ransomware specifics includes adding .CrySiS file extension after the encryption process. Once this happens the data is no longer accessible unless a decryption key is applied. This ransomware is detected to use RSA encryption algorithm and AES-128 at once. RSA encryption algorithm reveals the public encryption key and keeps in secret the decryption key. AES-128 is a symmetric-key algorithm, with the key for encryption and decryption being the same.
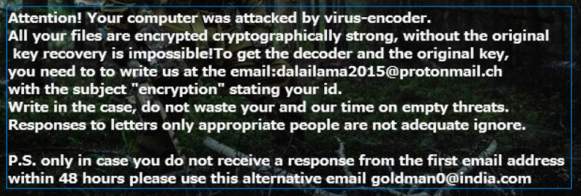
At the next stage of infection the ransomware creates a text file that contains a ransom note. The same text is displayed on an image that replaces the victim’s desktop wallpaper. Here is what the ransom message states:
“Attention! Your computer was attacked by virus-encoder.
All your files are encrypted cryptographically strong, without the original key recover is impossible! To get the decoder and the original key, you need to write us at the email:[email protected] with subject “encryption” stating your id.
Write in the case, do not waste your and our time on empty threats.
Responses to letters only appropriate people are not adequate ignore.
P.S. only in case you do not receive a response from the first email address within 48 hours please use this alternative email [email protected].”
The origin of the ransomware is unknown despite the fact the cyber criminals have provided two different emails for contact in the ransom message. The first mentioned email in the ransom message is registered in the Czech Republic. The second is recorded as a domain in India.
Let’s see how CrySiS ransomware may infect the system.
Spread Methods Of CrySiS Ransomware
CrySiS may be spread through:
- Fake notifications of software updates (Java, Flash Player, Browser’s updates, etc.);
- Malicious links in emails or websites that cause redirects;
- Deceptive or spam emails that contain malicious attachments;
- Social networks;
- File sharing services.
Summary and Removal Of CrySiS Ransomware
If CrySiS ransomware has infected your system, there is no doubt that you should remove it as soon as possible. You could follow the instructions we’ve provided below. The complete removal of Crysis malware from the infected system is a rather tough task especially if you have no experience in dealing with malware problems.
Since malware attacks are increasing and users suffer from daily attacks, we have decided to make a tutorial which will help you delete malware, try and restore files in case they are encoded by crypto-viruses and protect yourself in the future as well.
In case you need further help leave a reply in the comment section and we will try to assist you as soon as possible.
CrySiS Ransomware Master Decryption Keys Released. How to restore .CrySiS Files
The master decryption keys have been released on a popular security forum with a link to the pair combinations that are hosted in a text file hosted on Pastebin. The contents included the C header file which contained the master keys and information on how they can be used.
The very same keys have already been used in a decryption tool developed by Kaspersky Labs. The user who released the information is known as crss7777 and his identity is not known. However the fact that he had in-depth knowledge of the threat and that he had access to the master decryption keys of the CrySiS ransomware has led some security specialists to believe that he may be one of the developers of the dangerous virus.
After the security analysis the experts concluded that the key pairs were legitimate.

Crysis Ransomware Removal
For a faster solution, you can run a scan with an advanced malware removal tool and delete Crysis completely with a few mouse clicks.
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Crysis Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
-
1) Use present backups
2) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter