Security experts detected new attack campaigns that server the Teerac ransomware to targets worldwide, read our removal guide to protect yourself.
Teerac Ransomware Description
The Teerac ransomware is an old threat which has recently appeared in a wave of new attack campaigns. The strains associated with it were discovered in the summer of 2016 and according to the analysis performed then the ransomware itself does not include any advanced features.
Upon infection it launches its encryption engine which affects the following file type extensions:
- AVI – A popular video format.
- BMP – A bitmap uncompressed raster image file format.
- ICO – Icon image files.
- INF – These files are typically used to store configuration files and various variables used by applications.
- GIF – A popular raster image file format which supports animation.
- MP3 – Popular compressed audio format.
- PNG – An image file format.
- TXT – Plain text files.
- WAV – An uncompressed audio file.
- XML – A markup document.
The following file extensions are file paths are placed in a blacklist and are not affected:
bat, chm, cmd, dll, exe, ini, log, lnk, msi, scr, sys, tmp.
All of the affected files are renamed using the .encrypted extension.
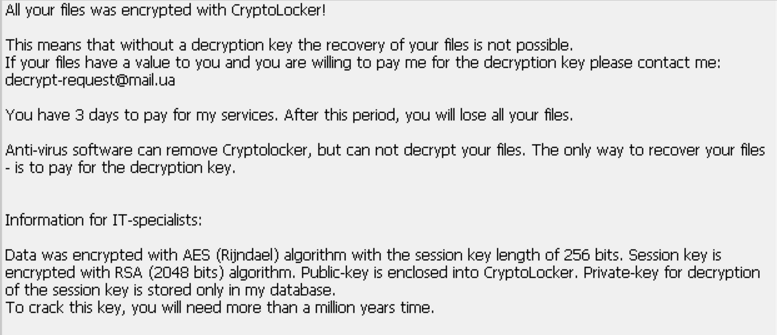
Depending on the configuration of the individual samples the victims are then shown different ransomware notes which portray a CryptoLocker-style message. An example one reads the following:
All your files was encrypted with CryptoLocker!
This means that without a decryption key the recovery of your files is not possible. If your files have a value to you and you are willing to pay me for the decryption key please contact me: decrypt-request@maiLua
You have 3 days to pay for my services After this period, you will lose all your files.
Anti-virus software can remove Cryptolocker, but can not decrypt your files. The only way to recover your files – is to pay for the decryption key.
Information for IT-specialists:
Data was encrypted with AES (Rijndael) algorithm with the session key length of 256 bits. Session key is encrypted with RSA (2048 bits) algorithm. Public-key is enclosed into CryptoLocker. Private-key for decryption of the session key is stored only in my database. To crack this key, you will need more than a million years time.
Depending on the configuration the virus engine may also delete any available Shadow Volume copies which prevent data recovery without the use of a quality anti-malware solution.
There are several different characteristics which are unique to the Teerac ransomware:
- The Ransomware Can Be Dropped By Other Malware – The virus can be delivered via payload droppers or other malware infections which have infiltrated the victim machines.
- Process Manipulation – The virus engine can inject itself into any running system processes or applications.
- System Infiltration – Teerac Ransomware can be dropped to various system locations and its file permissions.
- Registry Entry Modification – The virus engine can change important and application related registry entries.
- Setting Up A Persistent Environment – Various types of system modification can lead to a persistent environment which makes manual removal impossible.
Security experts identified a new version in April 2017 which includes a new module that allows the virus to sends its own emails. It uses a freely hosted service and is able to relay the harvested system information to the attackers. Another occasion on which it can be used is the sending of spam email messages that link to the virus infection via the compromised hosts.
Teerac Ransomware Distribution
One of the primary ways of getting infected with the Teerac ransomware is through the Donoff Payload Dropper which uses phishing email messages. The attack wave uses spam messages that pose as being sent by a legitimate company or institution. The hackers behind the operation have created numerous templates which are mixed and sent to the individual targets with the intent of achieving a infection ratio. The fact that some of them may be customized depending on the chosen company makes it a formidable threat.
The attackers have chosen to use the malicious documents scheme which uses infected files that may be of user interest which are attached to the messages. In most cases they are in the form of rich text files, spreadsheets or databases that contain built-in scripts (macros) which deliver the ransomware upon interaction with them. Like other similar threats the dropper can also be used to drop other malware as well, making a mass infection very possible.
A newly discovered attack wave has been detected which uses infected software installers that deliver the virus to the target hosts. Another strategy is currently being employed. Security analysts spotted an ongoing attack wave that carries the Teerac ransomware by including the virus engine in various software installers. This is a popular tactic which uses legitimate installers for famous and well-known free or trial versions of applications, games and utilities. They can be distributed on various hacker-controlled download sites and portals. In the last few years ransomware infections have surged in popularity when it comes to distributing them on P2P networks like BitTorrent where illegal content is usually found.
Hackers can opt to use various sites created by themselves or hack already existing ones to host the ransomware downloads. The criminals can also create malicious advertising networks which both generate revenue for them and also redirect to the virus. They are frequently used in collaboration with the download portals to trick the user into infecting themselves.
Malicious browser extensions, also known as browser hijackers, are another popular source of Teerac ransomware infections. They can affect the most popular web browsers installed on the victim computers which include Mozilla Firefox, Google Chrome, Microsoft Edge and Internet Explorer. Most of them have a devastating effect on these applications as they perform two very dangerous modifications:
- Settings Modification – The browser hijackers change the default homepage, default new tabs page and default search engine to point to a hacker-controlled site. Such redirects can point to the virus payload directly or to a malicious ad site which can generate revenue for the operators.
- Information Harvesting – Most browser hijackers can extract sensitive information from the compromised devices such as stored account credentials, web history, cookies and settings.
Direct hacker intrusions and exploit kit automated vulnerability testing are another possible source of infection.
Summary of the Teerac Ransomware
| Name |
TeeRac Ransomware |
| File Extensions |
.encrypted |
| Ransom |
Varies |
| Easy Solution |
You can skip all steps and remove TeeRac Ransomware ransomware with the help of an anti-malware tool. |
|
Manual Solution |
TeeRac Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
TeeRac Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely TeeRac Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Teerac Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore Teerac Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



