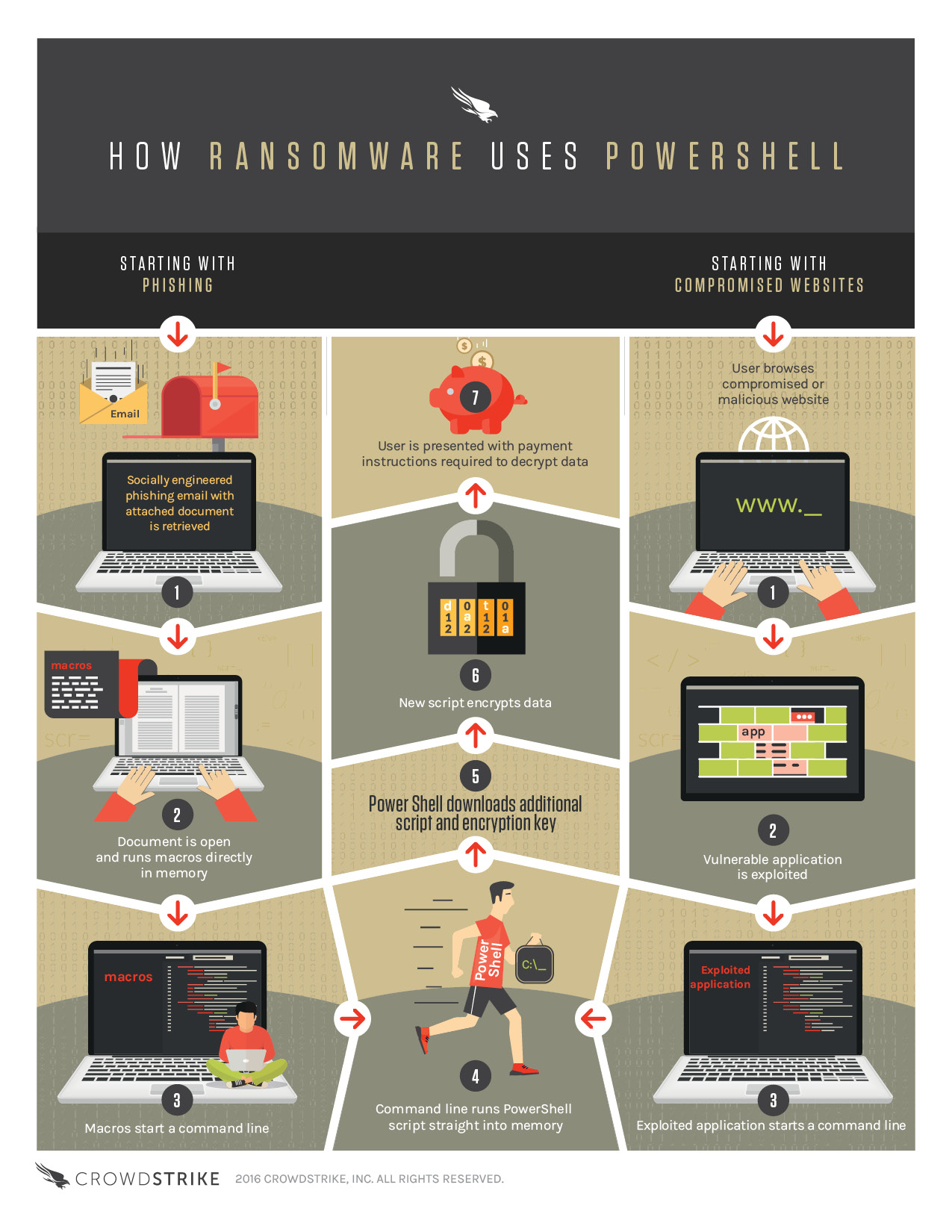
Today we are living in a time when ransomware is a constantly evolving threat. It appears to be one of the biggest threats to both consumers and enterprises. According to FBI, cyber criminals will gain net of around $ 1 billion in 2016. And as security measures are getting better at detecting and blocking ransomware, cyber criminals develop and apply new techniques to make their malware more adept. One of the latest advanced evasion techniques is the “fileless” one. Developed in such manner the ransomware does not write malicious files to the disk, as most ransomware does. Instead, it utilizes PowerShell to perform malicious actions.
How does “fileless” ransomware use PowerShell?
Provided by CrowdStrike