Privacy protection in the beginning of 2017 is still one of the most controversial aspects of the Internet. Activists and tech giants often engage in allegations against each other when it comes to the users’ interests. As the features of the social networks, mobile applications and computer software get updated all the time with all kinds of innovations, privacy activists find even bigger problems that are facing citizens worldwide. In this short guide, we would like to offer a few tips to better safeguard your privacy when using the Internet.
1. Use Adequate Protection for Your Accounts and Devices

Users are strongly encouraged to protect their online accounts and owned devices with secure measures. In 2017 the most popular method is still the use of passwords – a string of letters, numbers, and symbols that is used with an username associated with an individual. In some situations, additional measures are used such as two-factor authentication – additional measures besides the username and password. Examples include online banking tokens, electronic signatures or other means. Biometric authentication is one of the new methods that are gaining the attention of both the consumers and the criminals.
As passwords remain the most popular method of protecting an account or a device, we would like to remind everyone of the best security policies that ensure maximum protection.
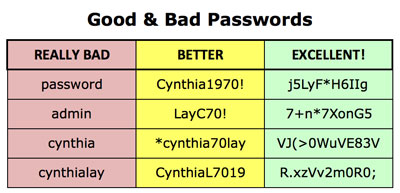
- Use complex passwords – This doesn’t mean just the crafting of a difficult to guess a password with both lower and uppercase combinations of letters, numbers, and symbols, but also avoiding commonly used phrases. Remember the rule “If it is in the dictionary, then its insecure”.
- Change the passwords often – Modification of the password at intervals of 3 to 6 months helps to prevent unauthorized access. In many cases when account leaks are reported on a service, the criminals acquire databases of usernames and passwords. If you have taken the time (only a few seconds) to change your password then you may very well avoid intrusion.
- Don’t store your passwords – Many people choose to write their passwords on paper and leave them in their wallet or bedroom. Such actions compromise all security measures and should never be used. One of the most common reasons for this is the inability of the users to associate the password string with something that could help them remember. If you must use password managers then use special software that enforces strong encryption.
- Crafty passwords are the best – Use techniques such as spelling words backwards, using number for letter substitution, capitalization of seemingly random letters and adding special characters.
2. Find out the Web Knows About You

Yes, Google may be your friend in lots of situations, but it can also act against you. As the number of potential employers scouts out their candidates online, security experts advise everyone to check how their online identity matches up to their real life. The results may even surprise most of the Internet users. Contemporary search engines use complex crawling mechanisms that aim to scan as much as possible. Consequently, comments, mentions, facts, location data and photographs of the users are shared on the Internet without their knowledge.
- Search for your full name or surname on the most famous search engines. Be sure to type it in brackets to show more relevant results.
- You can use search modifiers and additional information like your age, school or hometown. That may bring more insight.
- Use Google Image Search to find out images that are linked to your name. Using the option to search for relevant images may reveal additional sources that contain information about you.
- Don’t underestimate your email address. Searches for it online may reveal your subscription in public mailing list, chat logs and other services.
- Your social media identities often produce top search results. If you find a post that you don’t want to be shared on the search engine remove it from the relevant social media service.
3. Logout When You Are Finished with a Services
Most social media services, email providers, and other websites use some of the tracking options to monitor their users’ behavior. Webmasters use the information to investigate how people interact with the page, what content they view the most and other related information. By logging out of your account you disconnect your identity with the browsing behavior recorded in the website’s log.
This doesn’t automatically stop tracking methods of being used, but at least the webmasters can no longer associate the actions with the account. You can view our guide and stop Google from tracking your browser.
4. Do Not Reveal Personal Information

Most websites and services that require user registration ask for personal information such as personal names, date of birth, location, etc. Do not share your real identity with them, unless you completely trust the website owners with your privacy. Reveal personal information only to companies that you trust – your bank for example.
For sites that you frequently use, but do not wish to disclose much of your identity, use aliases or fake information.
5. Be Careful with Your Social Media

The popular social media are proving to be one of the places where personal information can easily be acquired. Users of Facebook tend not only to post information about the things that they care about, but also photographs, location data, and other revealing data. Take the time to amend your privacy settings to share information only with people you trust. Read our in-depth guide to Facebook Security.



