The Sage 2.0 virus is a malware that encrypts all user and system files on infected computers. The hackers extort the victims for a ransomware fee that is adjusted dynamically. All affected files are renamed with the .sage extension. Users can effectively remove the virus by:
- Follow our manual removal guide at the bottom of the article, or
- Using a quality virus removal tool.
DOWNLOAD SAGE 2.0 VIRUS REMOVAL TOOL.
Sage 2.0 Ransomware Description
The new Sage 2.0 ransomware is an updated version of the original Sage malware. It uses the same behavior patterns by encrypting target user files and extorting the victims for a big ransomware payment. This iteration of the virus requests the amount of 2000 US Dollars in Bitcoins. If the user does not pay within 7 days of infection this amount is doubled.
Upon infection, the malware modifies the Windows setting by creating a persistent environment for itself. For the purpose Spora 2.0 can create new files and processes that access different Windows libraries and ensure the execution of functions that assist and support the subsequent malicious activities. Thus the ransomware is able to collect information about the system, spawn a lot of processes, modify settings and establish connection with a remote server controlled by the hackers. The ransomware may drop and create its files in essential Windows folders like:
- %APPDATA%
- %Roaming%
- %Local%
- %SystemDrive%
- %TEMP%
- %USERPROFILE%
When that is done, the encryption engine is started. It targets specific user file types and appends the .sage suffix to all affected data. All .sage files remain inaccessible until the unique decryption key is used. Like the previous version, it targets the most commonly used data – multimedia files, backups, documents, configuration files and more. According to present researches the whole list of file types targeted by Sage 2.0 includes:
.rm, .flac, .mp2, .mpa, .aac, .wma, .djv, .pdf, .djvu, .jpeg, .jpg, .bmp, .png, .dat, .mx0, .cd, .pdb, .xqx, .old, .cnt, .rtp, .qss, .qst, .fx0, .fx1, .ipg, .ert, .pic, .img, .cur, .fxr, .slk, .m4u, .mpe, .mov, .wmv, .mpg, .vob, .mpeg, .3g2, .m4v, .avi, .mp4, .flv, .mkv, .3gp, .asf, .m3u, .m3u8, .wav, .mp3, .m4a, .m, .jp2, .lz, .rz, .zipx, .gz, .bz2, .s7z, .tar, .7z, .tgz, .rar, .zip, .arc, .paq, .bak, .set, .back, .std, .vmx, .vmdk, .vdi, .qcow, .ini, .accd, .db, .sqli, .sdf, .mdf, .myd, .frm, .odb, .myi, .dbf, .indb, .mdb, .ibd, .sql, .cgn, .dcr, .fpx, .pcx, .rif, .tga, .wpg, .wi, .wmf, .tif, .xcf, .tiff, .xpm, .nef, .orf, .ra, .bay, .pcd, .dng, .cpp, .xml, .php, .plb, .asc, .lay6, .pp4, .pp5, .ppf, .pat, .sct, .ms11, .lay, .iff, .ptx, .r3d, .raf, .rw2, .rwl, .kdc, .yuv, .sr2, .srf, .dip, .x3f, .mef, .raw, .log, .odg, .uop, .potx, .potm, .pptx, .rss, .pptm, .aaf, .xla, .sxd, .pot, .eps, .as3, .pns, .wpd, .wps, .msg, .pps, .xlam, .xll, .ost, .sti, .sxi, .otp, .odp, .wks, .vcf, .eml, .ott, .odt, .doc, .odm, .ppsm, .xlr, .odc, .xlk, .ppsx, .obi, .ppam, .text, .xltx, .xltm, .xlsx, .xlsm, .xlsb, .cntk, .xlw, .xlt, .xlm, .xlc, .dif, .sxc, .vsd, .ots, .prn, .ods, .hwp, .dotm, .dotx, .docm, .docx, .dot, .cal, .shw, .sldm, .txt, .csv, .mac, .met, .wk3, .wk4, .uot, .rtf, .sldx, .xls, .ppt, .stw, .sxw, .dtd, .docb, .wb2, .mda, .wk1, .sxm, .otg, .oab, .cmd, .bat, .h, .asx, .lua, .pl, .as, .hpp, .clas, .js, .fla, .py, .rb, .jsp, .cs, .c, .jar, .java, .asp, .vb, .vbs, .asm, .pas, .ldf, .tbk, .swf, .brd, .css, .dxf, .dds, .efx, .sch, .dch, .ses, .mml, .fon, .gif, .psd, .html, .ico, .ipe, .dwg, .jng, .cdr, .aep, .aepx, .123, .prel, .prpr, .aet, .fim, .pfb, .ppj, .indd, .mhtm, .cmx, .cpt, .csl, .indl, .dsf, .ds4, .drw, .indt, .qbm, .ptb, .qbi, .qbr, .2012, .des, .v30, .qbo, .stc, .lgb, .qwc, .qbp, .qba, .tlg, .pdd, .per, .lcd, .pct, .prf, .pst, .inx, .plt, .idml, .pmd, .psp, .ttf, .3dm, .ai, .3ds, .ps, .cpx, .str, .cgm, .clk, .cdx, .xhtm, .cdt, .fmv, .aes, .gem, .max, .svg, .mid, .iif, .nd, .2017, .tt20, .qsm, .2015, .2014, .2013, .aif, .qbw, .qbb, .qbx, .qby, .1pa, .ach, .qpd, .gdb, .tax, .qif, .t14, .qdf, .ofx, .qfx, .t13, .ebc, .ebq, .2016, .tax2, .mye, .myox, .ets, .tt14, .epb, .500, .txf, .t15, .t11, .gpc, .qtx, .itf, .tt13, .t10, .qsd, .iban, .ofc, .bc9, .mny, .13t, .qxf, .amj, .m14, ._vc, .tbp, .qbk, .aci, .npc, .qbmb, .ta9, .mem, .seam, .btif, .11t, .efsl, .$ac, .emp, .imp, .fxw, .sbc, .bpw, .mlb, .10t, .fa1, .saf, .trm, .fa2, .pr2, .xeq, .sbd, .fcpa, .ta6, .tdr, .acm, .lin, .dsb, .vyp, .emd, .pr1, .mn2, .bpf, .mws, .h11, .pr3, .gsb, .vnd, .esv, .kd3, .vmb, .qph, .t08, .qel, .m12, .pvc, .q43, .etq, .u12, .hsr, .ati, .mlc, .nni, .cus, .ldr, .ta4, .inv, .omf, .reb, .qdfx, .pg, .coa, .rec, .rda, .ffd, .ml2, .sba, .cfp, .nv2, .tfx, .n43, .let, .tt12, .210, .dac, .slp, .qb20, .saj, .zdb, .tt15, .ssg, .t09, .epa, .qch, .pd6, .rdy, .sic, .ta1, .lmr, .pr5, .op, .sdy, .brw, .t00, .mmw, .bd2, .ac2, .qpb, .tt11, .zix, .ec8, .nv, .lid, .qmtf, .hif, .lld, .quic, .mbsb, .nl2, .qml, .wac, .cf8, .vbpf, .m10, .qix, .t04, .qpg, .quo, .ptdb, .gto, .pr0, .vdf, .q01, .fcr, .gnc, .ldc, .t05, .t06, .tom, .tt10, .qb1, .t01, .rpf, .t02, .tax1, .1pe, .skg, .pls, .t03, .xaa, .dgc, .mnp, .qdt, .mn8, .ptk, .t07, .chg, .#vc, .qfi, .acc, .m11, .kb7, .q09, .esk, .09i, .cpw, .sbf, .mql, .dxi, .kmo, .md, .u11, .oet, .ta8, .efs, .h12, .mne, .ebd, .fef, .ddd, .ess, .qbmd, .afm, .d07, .vyr, .acr, .dtau, .ml9, .bd3, .pcif, .cat, .h10, .ent, .fyc, .p08, .jsd, .zka, .hbk, .mone, .pr4, .qw5, .cdf, .gfi, .cht, .por, .qbz, .ens, .3pe, .pxa, .intu, .trn, .3me, .07g, .jsda, .2011, .fcpr, .qwmo, .t12, .pfx, .p7b, .der, .nap, .p12, .p7c, .crt, .csr, .pem, .gpg, .key, .qpi, .mn5, .exp, .m16, .09t, .00c, .qmt, .cfdi, .u10, .s12, .qme, .int?, .cf9, .ta5, .u08, .mmb, .qnx, .q07, .tb2, .say, .ab4, .pma, .defx, .tkr, .q06, .tpl, .ta2, .qob, .m15, .fca, .eqb, .q00, .mn4, .lhr, .t99, .mn9, .qem, .scd, .mwi, .mrq, .q98, .i2b, .mn6, .q08, .kmy, .bk2, .stm, .mn1, .bc8, .pfd, .bgt, .hts, .tax0, .cb, .resx, .mn7, .08i, .mn3, .ch, .meta, .07i, .rcs, .dtl
Next, the ransomware drops its ransom note in a file called !HELP_SOS.hta on the following location:
%USERPROFILE%\Desktop\!HELP_SOS.hta
The text is then added to the Windows desktop background and all that it reads is:
===== Need help with translation?? Use https://translate.google.com =====
*** ATTENTION! ALL YOUR FILES WERE ENCRYPTED! ***
*** PLEASE READ THIS MESSAGE CAREFULLY ***All your important and critical files as well as databases, images and videos and so on were encrypted by software known as SAGE!
SAGE 2.0 uses military grade elliptic curve cryptography and you have no chances restoring your files without our help!
But if you follow our instructions we guarantee that you can restore all your files quickly and safely!———————————-
To get the instructions open any of this temporary links in your browser:
http://7gie6ffnkrjykggd.er29sl.in/login/*id*
http://7gie6ffnkrjykggd.rzunt3u2.com/login/*id*This links are temporary and will stop working after some time, if you can’t open these links, you can use TOR Browser
The TOR Browser is available on the official website: https://www.torproject.org/Just open this site, click on the “Download Tor” button and follow the installation instructions, then use it to open the following link:
http://7gie6ffnkrjykggd.onion/login/*id*
The ransom note navigates victims to websites where the payment process can be followed. Sage 2.0 ransomware reads information about the supported languages on the infected system. This action is probably performed as a way of the threat to determine which language to choose for its Sage 2.0 User Area payment web page that the victim accesses by following the links in the ransom note. The ransomware samples reveal that the threat is likely to support the following languages:
German, English, Spanish, French, Italian, Dutch, Portuguese, Iranian
And the English version of the Sage 2.0 payment website contains the following message:
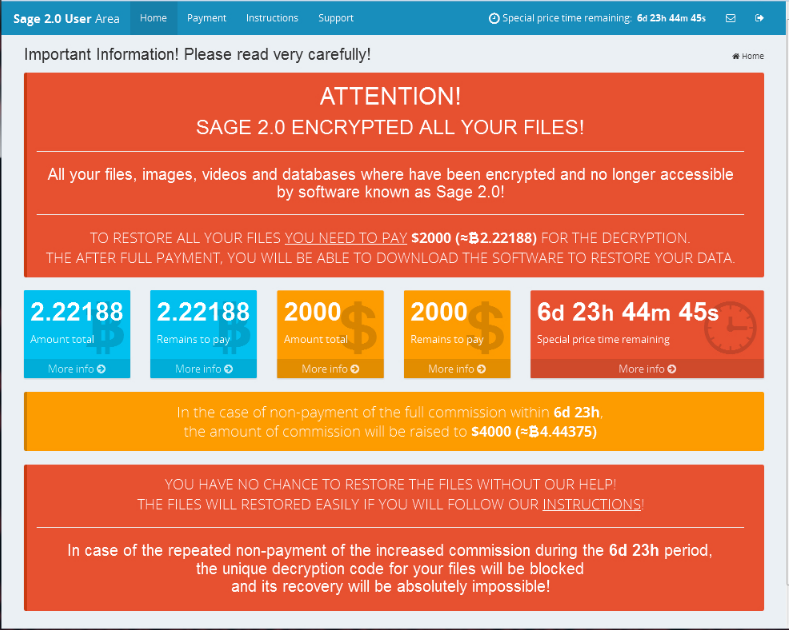
Furthermore, Sage 2.0 runs the command vssadmin.exe delete shadows /all /quiet to remove all shadow volume copies saved on the PC and prevent one of the possible ways for file restore.
The ransomware may also modify and create new values in the following Windows registry keys:
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
- HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\RunOnce
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce
The values in these keys control the processes that start at every system start.
The Sage 2.2 ransomware is the latest iteration of this virus. It uses mainly email spam messages and infected software installers to infect the target computers. The detected bulk messages use phishing tactics to increase the infection ratio. The hackers may opt to use a malicious JavaScript file which can trigger the payload infection or an infected Microsoft Office document with dangerous macros.
The dangerous characteristic of the Sage 2.2 ransomware is the fact that the virus can open a network port on the compromised machines which is used for remote control actions. Depending on the used configuration the strain can drop different types of files – dll’s, executables, image files and etc.
Sage 2.0 Ransomware Distribution
The Sage 2.0 ransomware is primarily distributed using spam email campaigns. The current iteration of the virus was detected in emails that carried no subject lines and no body message contents. The only data that they carry was a zip archive that contains a Microsoft Word document file. If the users open it, they will see a message saying “Document created in an earlier version of Microsoft Office Word. To view this content, please click ‘Enable Editing’ from the yellow bar and then click ‘Enable Content'”.
This engages the macro which downloads the Sage 2.0 ransomware onto the victim computer. In some of the cases, the Word document can be substituted for a .js file as well.
By default, the infected victim will be shown an UAC window which requests for elevated privileges. Until the victim acknowledges the request, the window will continue spawning. In addition, the Sage 2.0 ransomware will also delete all Shadow Volume copies of the infected machine.
Summary of Sage 2.0 Ransomware
| Name |
Sage 2.0 |
| File Extensions |
.sage |
| Ransom |
2000 US Dollars in Bitcoins |
| Solution #1 |
You can skip all steps and remove Sage 2.0 ransomware with the help of an anti-malware tool. |
|
Solution #2 |
Sage 2.0 ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
The Sage 2.0 ransomware is ranked as a persistent ransomware threat. This is a new iteration of the old malware code and we suspect that more strains may be created in the future. As such it is very important to use a trusted anti-spyware utility to remove active infections and be able to protect your computer in the future.
How Can I Prevent Ransomware Like Sage 2.0
The problem of getting Sage 2.0 isn’t limited to this singular case of infection. Ransomware viruses like this are distributed all throughout the Internet. Our initial assessments of the virus were correct, and the best way to prevent further problems with Sage 2.0 is to get an anti-malware tool.
As we said, there are dozens of ways to contract ransomware – in email spam, malicious websites, torrents trackers; you name it. A ransomware infection is much more costly than an anti-malware tool. Even if you don’t pay the ridiculous ransom, it’ll likely cost a lot more in damages.
Sage 2.0 Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Sage 2.0 Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



