Globe2 a new ransomware virus has just been spotted to be spreading. It is a serious threat that endangers almost all sensitive user data. Once it loads its malicious payloads on the victim’s PC, the files become inaccessible by any program. This is a consequence of its encryption function. After utilizing strong Blowfish encryption algorithm the victims may observe one of the following extensions appended at the end of their file names: .raid10, .blt, .globe, .encrypted, .mia.kokers@aol(.)com. The cybercriminals demand a ransom of 0.8 BTC or more to deliver the decryption key. However, we recommend the avoidance of any negotiations with the foes.
If you’re a victim of this troublesome threat keep reading the article, we have good news for you. In case you have landed on this page because you eager to learn we recommend you to meet the specifics of Globe2 ransomware and know how to prevent infection.
Spread Methods of Globe2 Ransomware
Like many other ransomware Globe2 may be spread with the help of spam emails. The emails may contain malicious attachments or links to compromised domains. The concealed attachments may pretend to be a credible file like an invoice, a report, a document of medical test results, etc. The troublesome Gobe2 may also be hidden in alerts of fake software updates or behind ads that lead to compromised websites.
Details About Globe2 Ransomware
Globe2 ransomware is the updated version of Globe ransomware which was first detected in August 2016. However, the Globe2 cryptovirus may have nothing in common with the working mechanism of Globe ransomware.
Once it is on the computer, it starts to scan for particular files, folders or both, and encode the targeted data. It may target the most frequently used file types – audio, music, image files, documents, presentations. Unlike generally used practice of ransomware developers to encipher victim’s data with RSA or AES encryption algorithms Globe2 uses Blowfish symmetric-key block cipher. When the encryption process is done the locked files become inaccessible, and one of the following extensions will be added at the end of the file names:
- .raid10
- .blt
- .globe
- .encrypted
- .mia.kokers@aol(.)com
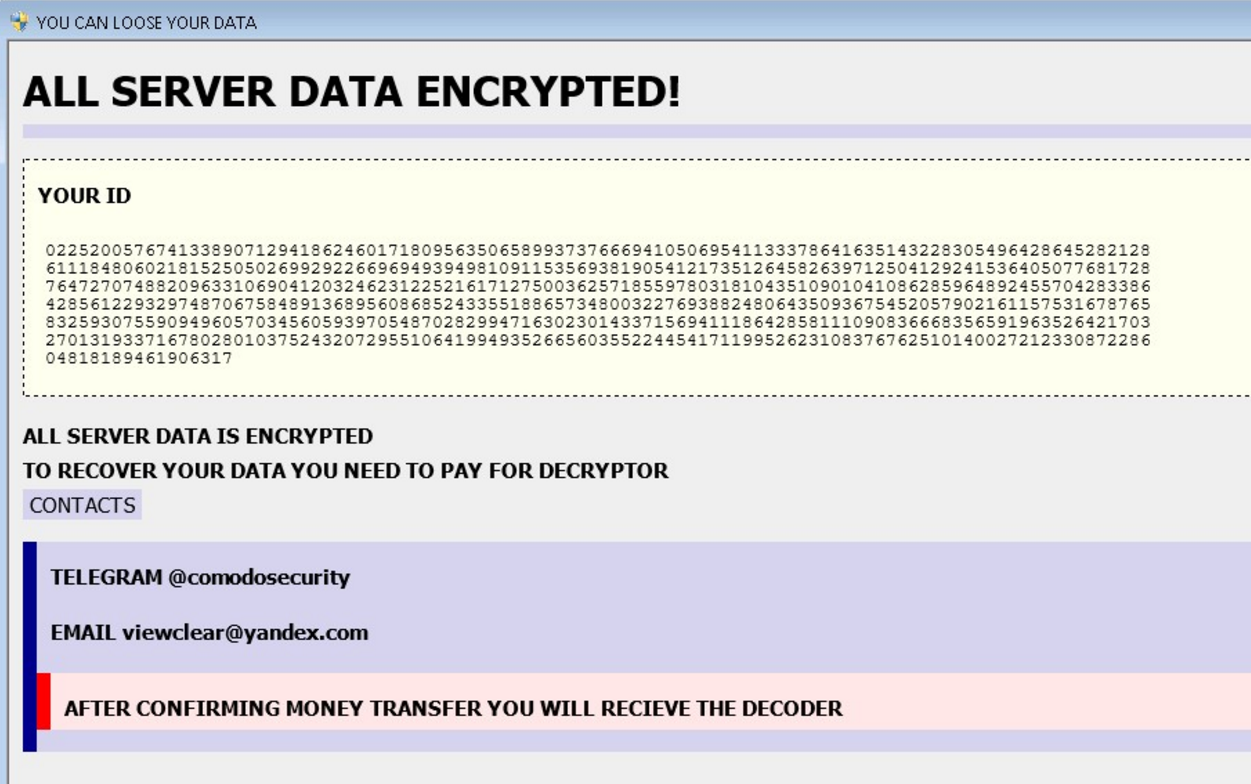
The creators of Globe2 have developed a ransom note which is usually dropped to the victim’s computer at the end of the encoding process. They have named the note “YOU CAN LOOSE YOUR DATA”. The depicted text give information of the victim’s ID, the impact the virus has just made to the system and contact details for a payment for the decryptor.
“ALL SERVER DATA ENCRYPTED!
YOUR ID (random numbers)
ALL SERVER DATA IS ENCRYPTED.
TO RECOVER YOUR DATA YOU NEED TO PAY FOR DECRYPTOR.
CONTACTS
TELEGRAM @comodosecurity
EMAIL viewclear@yandex(.)com
AFTER CONFIRMING MONEY TRANSFER YOU WILL RECEIVE THE DECODER.”
Decrypt Files Locked by Globe2 Ransomware
Now let’s reveal the good news for the victims of Globe2 ransomware. The security researchers from Emsisoft have been analyzing the code of Globe2 for weaknesses, and a free decrypter is available! We need to inform you that first, your computer should be safe from Globe2 malicious files. Then you will have the chance to bring your files back to normal. Follow the instructions at the end of the article and remove all nasty files and objects from the system. Afterward all of you who have locked files with Globe2 ransomware could download the decrypter by following the link:
Removal of Globe2 Ransomware
We firmly advise all victims of Globe2 ransomware to remove the threat instantly from their computers. The timely removal of all malicious files and objects will prevent more security-related problems. We have provided a removal guide below which allows infected users to choose whether to remove Globe2 manually or automatically. Scanning your computer with advanced anti-malware software will bring maximum effectiveness during the removal process and prevent future infections.
What Can I Do To Prevent Globe 2 Ransomware?
A ransomware infection is a clear signal that your computer lacks the necessary protection. The problem may be solved by:
- Better anti-spam measures – don’t download shady attachments
- Don’t give your email to sites with pirated content
- Never install suspicious ZIP or RAR files from spammed emails
- Get an anti-malware tool
The Globe2 ransomware infection received an update earlier this year. The new version of the virus is more dangerous and infectious than ever. There are few changed that will be apparent to the average user – Globe still infects your computer and encrypts your files:
Globe 3 Ransomware Virus (Removal Steps and Protection Updates)
Summary
| Name | Globe2 |
| File Extensions | .raid10, .blt, .globe, .encrypted, .mia.kokers@aol(.)com. |
| Ransom | 0.8 BitCoin |
| Easy Solution | You can skip all steps and remove Globe2 ransomware with the help of an anti-malware tool. |
| Manual Solution | Globe ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Infection | Email Spam, PUPs, dangerous sites. |
Globe2 Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
- 1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
- 1) Open My Computer/This PC
2) Windows 7
- – Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
- – Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
- 1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Globe2 Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
- 1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inver
ted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
- 1) Use present backups
2) Restore your personal files using File History
- – Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
3) Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

STEP VII: Preventive Security Measures
- 1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
Globe2 Ransomware – How to Remove It and Decrypt Files
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.



