Update! WannaCrypt0r 2.0 Ransomware Virus is the new iteration of WannaCry virus.
The WannaCry ransomware virus is an evolved strain of the Wcry family which encrypts sensitive user data. It encrypts victims’ files adds the .wcry extension to them. After that it asks for a ransom fee in exchange for a decryption key. We strongly suggest you to not pay that sum to the cyber criminals. Instead, remove WannaCry immediately from your system and only then try to recover your encrypted files.
Manual Removal Guide
Recover .WNCRY Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
WannaCry Ransomware Virus – Description
WannaCry virus is a newly discovered virus which has proven to be very dangerous to the infected computers. The initial security analysis shows that it is also distributed under the alias of WannaCryptor ransomware and it is derived from the Wcry ransomware family.
WannaCry virus uses the AES-128 cipher to target a list of predefined file type extensions which includes the following:
.123, .3dm, .3ds, .3g2, .3gp, .602, .7z, .aes, .ai, .ARC, .asc, .asf, .asp, .avi, .backup, .bak, .bmp, .brd, .c, .cgm, .class,
.cpp, .crt, .cs, .csr, .csv, .db, .dbf, .dch, .dif, .dip, .doc, .docb, .docm, .docx, .dot, .dotm, .dotx, .dwg, .edb, .eml, .fla, .flv,
.frm, .gif, .gpg, .gz, .hwp, .ibd, .jar, .java, .jpeg, .jpg, .js, .jsp, .key, .lay, .lay6, .ldf, .m3u, .m4u, .max, .mdb, .mdf, .mid, .mkv,
.mml, .mov, .mp3, .mp4, .mpeg, .mpg, .msg, .myd, .myi, .n, .nef, .odb, .odg, .odp, .ods, .odt, .ost, .otg, .otp, .ots, .ott, .p12, .PAQ,
.pas, .pdf, .pem, .php, .pl, .png, .pot, .potm, .potx, .ppam, .pps, .ppsm, .ppsx, .ppt, .pptm, .pptx, .psd, .pst, .rar, .raw, .rb, .rtf,
.sch, .sh, .sin, .slk, .sql, .sqlite3, .sqlitedb, .stc, .std, .stw, .suo, .swf, .sxc, .sxd, .sxm, .sxw, .tar, .tarbz2, .tbk, .tgz, .tif,
.tiff, .txt, .uop, .uot, .vb, .vdi, .vmdk, .vmx, .vob, .vsd, .vsdx, .wav, .wb2, .wk1, .wks, .wma, .wmv, .xlc, .xlm, .xls, .xlsb, .xlsm,
.xlsx, .xlt, .xltm, .xltx, .xlw, .zip
The original Wcry ransomware is signed as a counterfeiet messaging application which is then distributed to the victims via a variety of different strategies – bulk email messages, infected software installers, malicious ads and redirects and etc. All of the affected data is encrypted using the .wcry extension and we suspect that the new WannaCry virus also uses it as well. In addition, the core threat Wcry ransomware also deletes all Shadow Volume Copies available on the local machine which prevents data recovery without the use of a professional-grade solution.
The fact that WannaCry virus is also carried in several randomly-named binary files makes it very convenient for attackers to spread it to all sorts of targets – from individual users to large organizations and groups.
As the complete analysis is not yet available, we suspect that the newly created WannaCry ransomware might contain additional functionality. Modules that can be attached to the main virus engine include the following:
Persistence – The virus engine may create certain conditions which allow the threat to remain constantly active on the infected computer. This is is usually achieved by modifying the Windows settings, registry files, boot commands and other important variables. Usually as a result the virus can only be removed by using a quality anti-malware solution.
Misconfiguration – Some viruses tweak the Windows settings or those of important applications to deliberately impact performance or turn off options or functions.
Payload Dropper – Evolved versions of the WannaCry ransomware may contain a payload dropper which can be used to deliver additional viruses to the infected host. WannaCry virus may also institute various browser hijackers or other extensions to the web browsers which can harvest the stored account credentials, cookies and web search history.
Information Extraction – An advanced form of this virus can be used to extract valuable data from the infected computers. The hackers can either setup a predefined configuration of target data or use network commands to harvest information at will. Depending on the engine the network traffic flow may be encrypted for a more secure transfer.
Remote Control – Recently some of the evolved strains include a Trojan module which can be used to remote control the infected machines. The hackers can opt to take full control of the computers or spy on the users activities which include live video surveillance, keystroke recording and other types of malicious activities.
Upon infection WannaCry virus follows the basic behavior patterns associated with the Wcry engine. It starts its encryption engine which targets the predefined list of file type extensions. As this is merely a new strain with not much new additions, we suspect that WannaCry targets the same list (see above).
As always the Shadow Volume Copies of the local machine are deleted to prevent data recovery. You can restore the files using a professional grade data recovery solution (see our removal instructions below). We suspect that future iterations might even include a network worm which can propagate across the internal network.
Update! WannaCrypt0r 2.0 Ransomware Virus is the new iteration of WannaCry virus.
What’s different between WannaCry virus and some of the original Wcry ransomware samples is that once the encryption process is complete, а screenlocker is instituted as well as the standard ransomware note. This prevents normal user interaction with the infected computer until the virus has been removed.
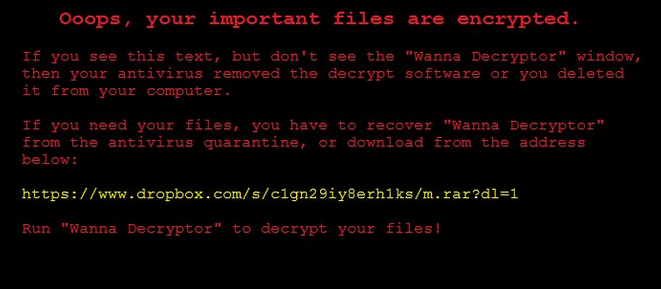
The following message is displayed:
Ooops, your important files are encrypted.
If you see this text, but don’t see the “Wanna Decryptor” window, then your antivirus removed the decrypt software or you deleted it from your computer.
If you need your files, you have to recover “Wanna Decryptor” from the antivirus quarantine, or download from the address below:
xxxxs://www.dropbox.com/s/c1gn29iy8erh1ks/m.rar?dl=1
Run “Wanna Decryptor” to decrypt your files!
No specific instructions are given except a link to the Dropbox file hosting site which links to a small archive named “m.rar”. It is password protected and probably contains another virus in itself. Virus scanners cannot efficiently scan such files and this is the reason why all users should use a quality anti-malware solution to protect themselves.
Some of the users reported succeeding in installing the hacker supplied “decryptor”. It itself displays a rather simple looking application which demands the ransom fee of 300 US Dollars payable in Bitcoins. To force users into paying the sum the hackers have used two other additional social enginering tricks:
- The use of a “payment raise” if the fee is not paid in a short period of time.
- The use of a final time limit. The hacker operators state that file access will be lost unless the payment is made.
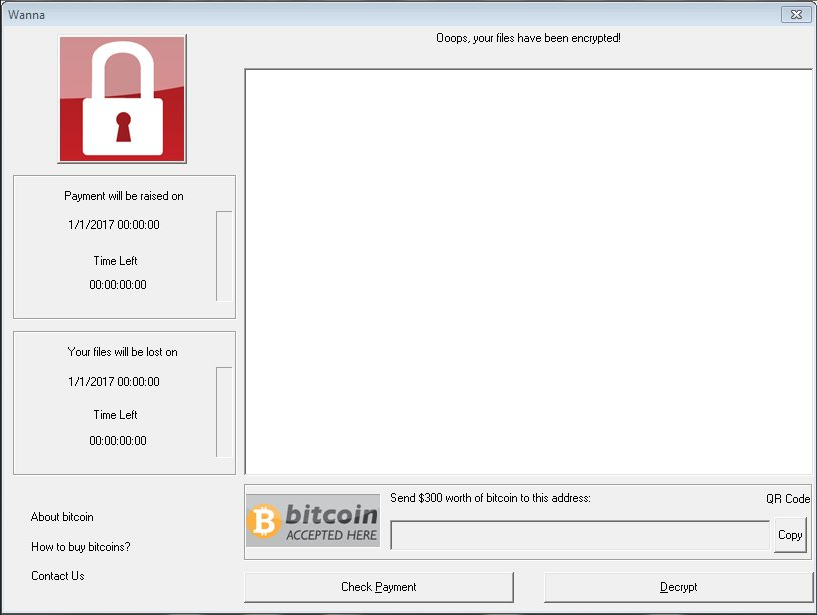
To calculate the time of the infection wannaCry virus uses several data extracted from the machine during the first phase of infection. As always the hackers have supplied detailed information about how the victims can obtain the digital currency and pay the fee to them.
WannaCry Ransomware Virus – Distribution
The WannaCry ransomware is distributed globally around the world and targets users who speak the English language. The limited number of malware samples showcases that we have been able to spot the infections in a relatively short time.
Due to the limited number of the virus infections we cannot judge which is the primary method, however we suspect that the hacker operators use the most popular ones.
One of the main strategies that malware operators use is associated with sending phishing spam emails. The criminals typically employ body text, graphics and content that appears to be sent from a well-known and legitimate user, individual, company or government institution. Depending on the type of infection, WannaCry virus may either be attached directly, hyperlinked or downloaded via a script download. This is usually achieved by attaching various documents which may appear to be of user interest such as invoices, letters and etc. When the users interact with them a malicious macro or other type of script downloads WannaCry virus from a remote server and infects the local computer.
Another possibility is the use of hacked or hacker-controlled web sites, portals and malicious ads. They typically spread spam and viruses disguised as free or trial versions of popular software – applications, games, utilities or patches. Malicious ad networks also serve this role while at the same time generate income for the operators.
The use of infected software installers is linked to the previous tactic. Such instances are also linked with BitTorrent trackers where pirate content is distributed. Browser hijackers are another case where such malicious browser extensions not only change the settings of the installed browsers (Google Chrome, Mozilla Firefox, Microsoft Edge and Internet Explorer), but also engage in other dangerous actions – retrieval of sensitive information such as stored account credentials, cookies and web search history.
Exploit kits which automatically engage in automated vulnerability intrusion attempts and direct hacker attacks can also lead to a WannaCry ransomware infection.
WannaCry Ransomware Spreads to Industrial Networks
The dangerous WannaCry ransomware has been found to infect whole computer networks that are part of industrial control systems and critical infrastructure. This includes manufacturing plants, petrochemical facilities and other high-profile businesses. The virus engine uses the same infection patterns to compromise the enterprise networks and machines. As the ransomware itself was originally made to target the end-user versions of the Microsoft operating system, it failed to infect the control machines used in some of the facilities.
During the analysis it is revealed that there are thousands of infected computer networks with failed WannaCry ransomware infections. They are able to spread across the facilities and compromise end-user desktop or laptop devices. The WannaCry ransomware spreads using a known exploit tracked in the CVE-2017-0143 security advisory. The weakness lies in the SMB (Sambaa) protocol that is used for sharing files over the network. The WannaCry virus infections are done by checking if the targets can be affected:
- The computers are running a compatible version of the Microsoft Windows and associated components.
- The SMBv1 service is enabled.
- The vulnerable system port (TCP 445) is available and a connection can be made
- Adequate protection is not configured properly.
There are several other use case scenarios where the virus can affect a company network and its associated devices:
- The WannaCry ransomware can penetrate systems by infecting points of entry. They can include workstations or laptops issued by the facilities for remote login or administration.
- Connecting to less secure perimeter network components can lead the discovery of “weak spot” that can result in a WannaCry virus infection.
- Exploiting devices and bad network configuration can lead to a succesful virus attack.
We remind all users that popular companies and web services including: The UK NHS, the Russian postal service, Chinese government agencies, Honda’s manufacturing plant and others. One of the most important aspects of the WannaCry ransomware is that it is able to propagate across networks in a worm-like fashion. Along with its many advanced features it has been labeled as one of the most dangerous computer viruses in the last few years.
Remove WannaCry Virus and Restore Encrypted Files
WARNING! Manual removal of the WannaCry ransomware virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
WannaCry Virus – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
- – Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
- – Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover .WNCRY Files
WARNING! All files and objects associated with WannaCry ransomware virus should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD WannaCry Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
- – Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
- – Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



