The Cerber Ransomware is a very dangerous threat that has continued to evolve and infect thousands of computer world wide. Its latest iteration features updated code that kills database processes and connections to impact the stored data as well.
| Name |
Cerber Ransomware |
| File Extensions |
variant-specific extension (.cerber, .cerber2 or .cerber3) or random extensions |
| Ransom |
Varies |
| Solution #1 |
Cerber ransomware can be removed easily with the help of an anti-malware tool, a program that will clean your computer from the virus, remove any additional cyber-security threats, and protect you in the future. |
|
Solution #2 |
Cerber Ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Various distribution methods, most likely through spam email messages that contain links or attachments holding the malware. |
A Lot of Cerber Ransomware Variants and Only a Handful of Decryptors
Cerber is one of the most popular and aggressive ransomware variants that have plagued computer users worldwide. The threat has a dozen variants that use different mechanisms of encryption and depending on the infection the users may find that different files are encrypted. Cerber has also gone through several important milestone updates – some of them render early versions of the decryption software useless, while others add new mechanisms of action. One of the last versions of the Cerber ransomware has updated the code to feature database process killing. This is used by computer criminals to render even more damage.
A Typical Cerber Infection
The Cerber ransomware and its variants encrypt the most commonly used file extensions such as .jpg .doc .avi and others. They are renamed with a variant-specific extension (.cerber, .cerber2 or .cerber3), while some of them also random extensions such as .a242, .b1013, c.1414 and others.
The ransomware then creates ransom instructions that contain instructions on how to pay the criminals to restore the affected files. Security experts advise all victims to use decryption utilities and anti spyware solutions to protect and restore their machines from such attacks.
How to Use the Cerber File Decryptor
If you are affected by the first version of Cerber you can use the free decryptor software that is available for victims of the threat.
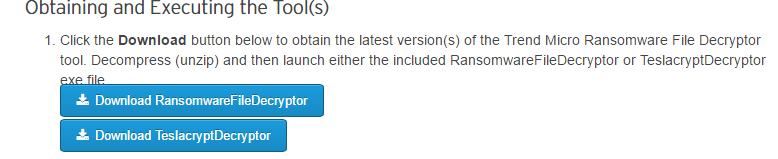
- To restore your files you need to first navigate to Trend Micro’s site where you can download it.
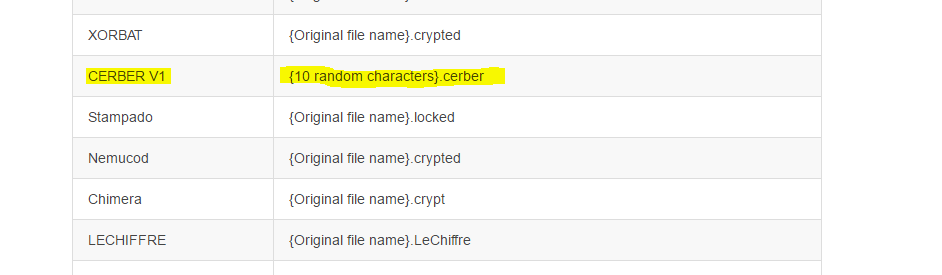
- Notice that the ransomware threats that can be decrypted by the utility are listed on the site. The original Cerber version is supported, the victims can identify it by looking at the encrypted file name extension. It should match the formula {10 random characters}.cerber.
- Click on the “Download Ransomware Decryptor” button to get a copy of the tool.
- You need to uncompress the downloaded .zip file and execute it to continue.
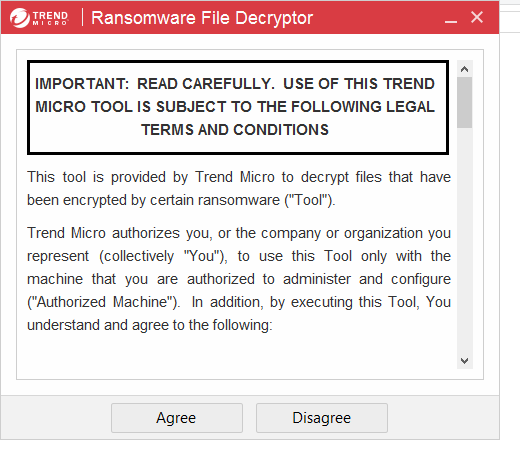
- AN EULA screen will appear, to continue press the “Agree” button.
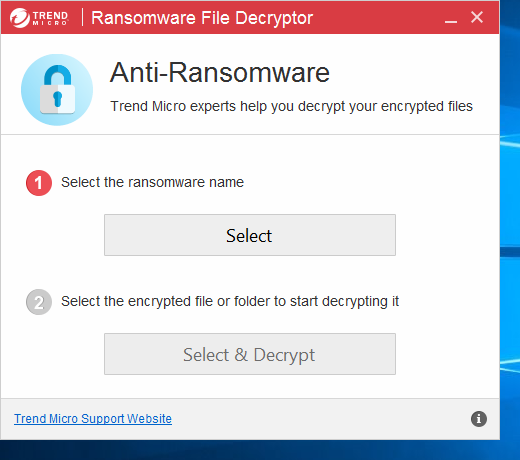
- The main screen prompts the user to select the ransomware type. Press the “Select” button to engage the menu.
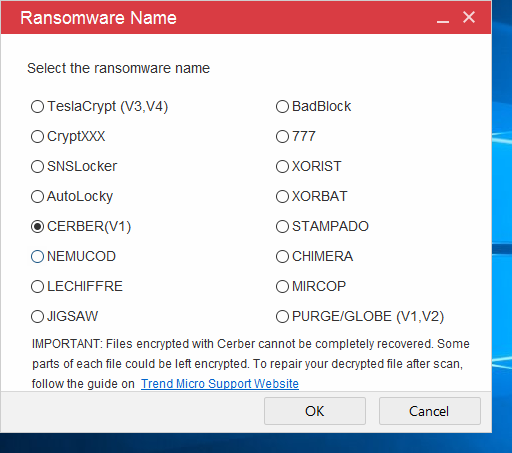
- On the next screen choose the appropriate threat, in this case this is the “CERBER (V1)” checkbox. Press the “OK” button to go back to the main screen.
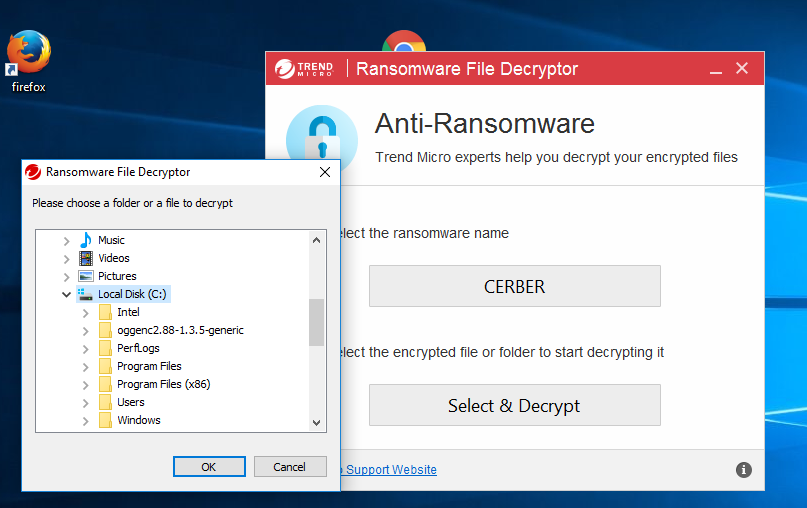
- Now you can press the “Select & Decrypt” button to start the decryption process. When this is pressed the user is prompted to select a drive which is affected by the ransomware. As Cerber has the capability to infect the whole system we advice all victims to select all drives from the drop-down menu.
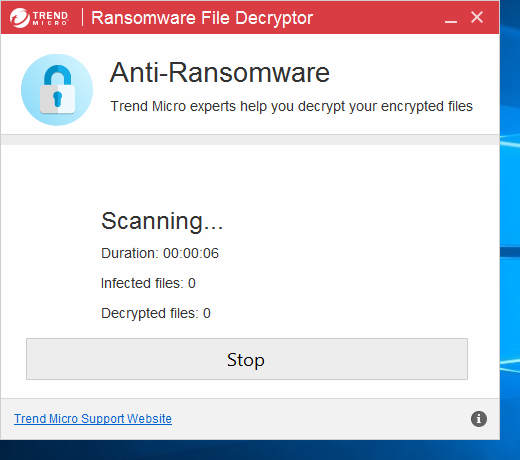
- The scanning and decryption process is started. This may take a while depending on your computer speed, partition size and the number of Cerber-affected files.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



