Crbr Encryptor Virus is the latest version of the Cerber ransomware family, learn how to remove it in our in-depth guide.
Manual Removal Guide
Recover Crbr Encryptor Virus Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How Does Crbr Encryptor Virus Infiltrate the System?
The Crbr Encryptor virus spreads across the world in large-scale infections. There are several different methods that are employed by the hackers.
One of them is the use of the Magnitude Exploit kit. It is used by the criminals to spread the Crbr Encryptor virus by targeting vulnerable software installations. Depending on the configuration the criminals may opt to target a single vulnerability or several at once.
Malicious code found on hacker-generated web sites, applications and scripts can lead to a dangerous Crbr Encryptor virus infection. The payloads can be inserted also in plugins such as Adobe Flash and web technologies and programming languages such as JavaScript and ActiveX. All of these are popular and used in practically all social networks and other related services.
The other main strategy for distributing the Crbr Encryptor virus is the creation and coordination of email spam messages. They pose as legitimate emails from famous companies and usually include the malware either as a file attachment or a link in the body content.
The payload can also come in the form of infected software bundles. They are modified binary installers that are usually taken from the source sites. Criminal controlled sites and P2P sites are the usual placed where one can get infected with the Crbr Encryptor virus.
Another option is the use of browser hijackers to install the Crbr Encryptor virus as part of their standard installation routine. They represent malicious add-ons that are made for the most popular web browsers: Mozilla Firefox, Safari, Google Chrome, Microsoft Edge and Internet Explorer. Once installed they modify the default home page, search engine and new tabs page to a hacker-controlled site. In addition they steal sensitive information such as any stored cookies, passwords, bookmarks, account credentials, form data and history. They are transferred over to the criminals and the bulk of information can be easily used to conduct identity theft.
Related: Cerber 6 Ransomware, Cerber 2017 Ransomware
Infection Flow of Crbr Encryptor Virus
Security experts discovered a new strain of the Cerber ransomware family called the Crbr Encryptor virus. It is not a fully updated version but rather a name modification and some small code changes. At the moment the exact reason for the sudden name change is not known.
It follows the usual tactics that are usual to the Cerber family. Crbr Encryptor virus starts its encryption engine as soon as the infection has been made. It targets the most popular file type extensions while retaining the possibility to change the built-in list depending on the targets.
The affected files are renamed using a random 4-characters extension. While the Crbr Encryptor ransomware engine is running, the virus sends beacons to several hacker-controlled IP addresses – the captured samples were found to communicate with: 77.12.57.0/27, 19.48.17.0/27 and 87.98.176.0/22. As usual the ransomware note is written in “_R_E_A_D___T_H_I_S___{RAND}_.hta” and “_R_E_A_D___T_H_I_S___{RAND}_.txt”. Likewise the desktop background is also changed to reflect the infection.
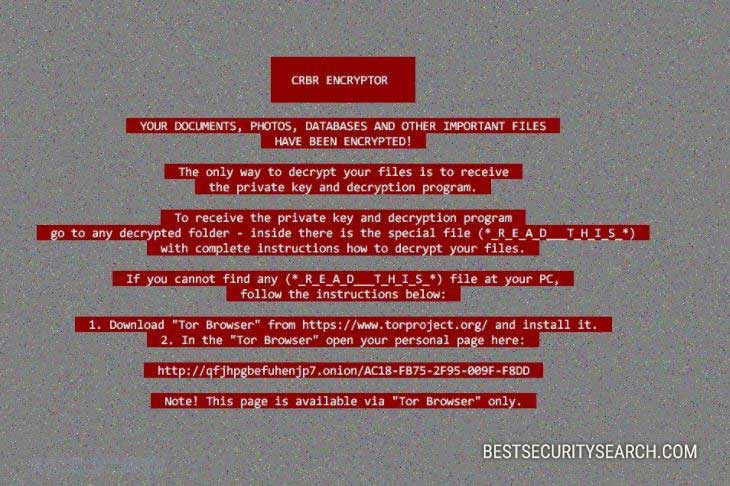
The ransomware note reads the following message:
Hi, I’am CRBR ENCRYPTOR 😉
—–
YOUR DOCUMENTS, PHOTOS, DATABASES AND OTHER IMPORTANT FILES HAVE BEEN ENCRYPTED!
—–
The only way to decrypt your files is to receive the private key and decryption program.
To receive the private key and decryption program go to any decrypted folder,
inside there is the special file (*_R_E_A_D___T_H_I_S_*) with complete instructions
how to decrypt your files.
If you cannot find any (*_R_E_A_D___T_H_I_S_*) file at your PC, follow the instructions below:
—–
1. Download “Tor Browser” from https://www.torproject.org/ and install it.
2. In the “Tor Browser” open your personal page here:
http://xpcx6erilkjced3j.onion/[victim_id] Note! This page is available via “Tor Browser” only.
—–
Also you can use temporary addresses on your personal page without using “Tor Browser”.
—–
1. http://xpcx6erilkjced3j.1t2jhk.top/[victim_id] 2. http://xpcx6erilkjced3j.1e6ly3.top/[victim_id] 3. http://xpcx6erilkjced3j.1ewuh5.top/[victim_id] 4. http://xpcx6erilkjced3j.15ezkm.top/[victim_id] 5. http://xpcx6erilkjced3j.16umxg.top/[victim_id] —–
Note! These are temporary addresses! They will be available for a limited amount of time!
The victims are blackmailed to visit the hacker-provided payment gateways where detailed instructions are placed. In the majority of cases the requested sum is 0.5 Bitcoins. This is the equivalent of about 1200 US Dollars. All transactions done using the digital currency cannot be effectively traced to a single individual or company.
The hackers use the usual blackmail tactics of placing a time limit to further force the victims into paying the sum – once the limit is reached the price is doubled.
We remind the victims that the only possible way of recovering the affected files is by using a quality anti-spyware solution and a professional-grade data recovery solution.
Remove Crbr Encryptor Virus and Restore Data
WARNING! Manual removal of Crbr Encryptor Virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Crbr Encryptor Virus – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
-
– Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
-
– Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover Crbr Encryptor Virus Files
WARNING! All files and objects associated with Crbr Encryptor Virus should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD Crbr Encryptor Virus Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
-
– Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



