Cerber 6 Ransomware Virus Description
The Cerber ransomware family has grown once again with the addition of its latest iteration. The newest Cerber 6 virus has been identified in a series of attacks initiated by an unknown hacker collective. In comparison with previous versions there are several important feature additions:
- New Encryption Patterns – The hackers have rewritten and revised the encryption process that takes place after Cerber 6 virus has infected the computer. The programmers created a separate function that reads and encrypts the contents of the target data files.
- Improved Anti-Debugging Protection – During the initial analysis, researchers discovered that the captured Cerber 6 virus samples are able to actively guard themselves against sandboxes and debugging environments.
- Security Solutions Bypass – Like other advanced malware threats the new iteration of the Cerber ransomware family is able to prevent removal by most anti-virus software and firewalls. Only a quality anti-malware solution can effectively remove the active infections and protect against possible intrusions.
- New Delivery Methods – Cerber 6 is delivered as self-extracting archives that contain Visual Basic Script (VBS) or Dynamic-link libraries (DLL).
Upon infection with the Cerber 6 ransomware virus, the following behavior pattern has been observed:
- One of the first steps in the infection is the enforcement of the stealth protection module. It actively monitors the running processes and makes sure that no anti-debugging or sandbox environment is running on the machine. This is also true for virtual machines or other types of emulated computer instances. Its important for the victims to know that Cerber 6 can disable all running security software to prevent detection.
- The engine then continues to modify important Windows settings to achieve a persistent state of execution. This effectively prevents any manual removal attempts that can be initiated by the victims.
- An interesting trait that has been observed with Cerber 6 is the fact that the encryption engine performs a language settings check. This is used in the event of an inclusion of a blacklist. The criminal hackers behind the Cerber 6 virus can opt to choose users from certain countries that can be shielded from the attacks. This makes the malware suitable for attacks against whole regions.
- The encryption engine is then initiated which starts to encrypt sensitive user data with a very strong cipher. All affected files are renamed with a randomly-named extension. This version is also capable of deleting backups depending on the configuration.
- The virus engine contacts the remote command and control versions to report the infection.
- A ransomware note is shown to the victims which bribes them to pay a ransomware fee to restore their files.
In a very similar manner the victims are shown a ransomware note which is applied to the wallpaper, on the desktop and in various folders:
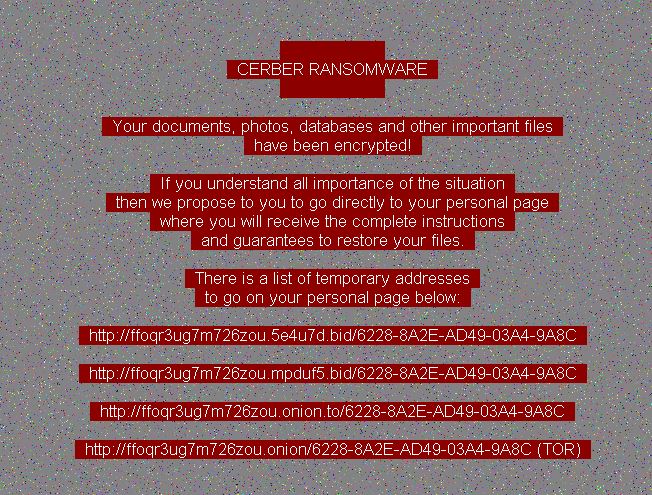
The language check done by the virus engine is used to display the ransomware note in the language used by the user.
The virus payment gateway is located on the anonymous TOR network as usual. Security researchers showcase that one of the biggest changes in this version is that the encryption routine uses the Cryptographic Application Programming Interface by Microsoft which is very similar to the infamous Spora ransomware. It is very likely that the programmers behind Cerber 6 ransomware are the creators of the Spora.
Like other advanced malware families, Cerber 6 has shifted to a RaaS (ransomware as a service) model. This makes it possible for hackers to make it available for purchase or rent to criminals in the underground black markets.
Cerber 6 Ransomware Virus Distribution
Like previous Cerber ransomware iterations, Cerber 6 virus also employs email spam messages as the primary infection method. The hackers send out spam email messages that contain a zipped attachment which includes a malicious .JS (Javascript) file. Depending on the campaign there are two ways of infection:
- Direct Infection – The preliminary installation module downloads directly the sample from a hacker-controlled remote server. A scheduled task then executes the viruses after a two minute delay.
- Embedded Script Execution – Cerber 6 virus can run an embedded script from the payload file which immediately starts the infection process.
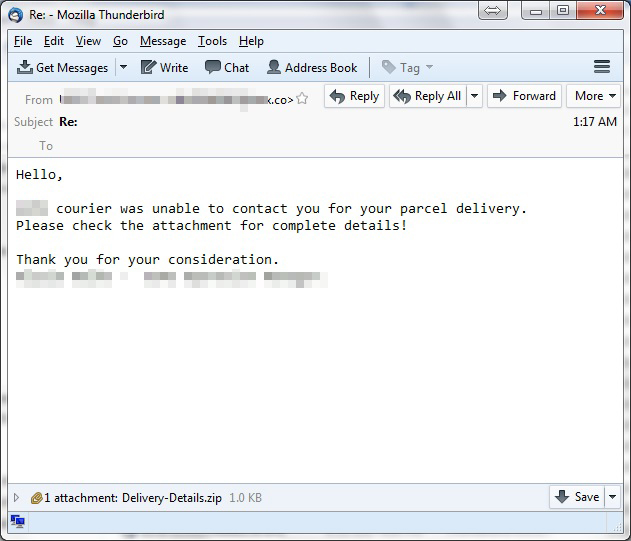
Various templates are used to make the targets infect themselves with Cerber 6. The majority of the infections are done using self-extracting archives and malicious scripts. Unlike some of the previous Cerber malware strains, Cerber 6 version uses a very complex infection chain. The hackers are distributing it globally. The majority of the infections have been initiated against the United States, Japan, Taiwan and Australia.
Other methods of infection include infected software installers that are modified by the hackers. The criminals choose free or trial versions of popular free or trial applications, games, utilities and patches. They are distributed on hacked or hacker-controlled sites that pose as legitimate download sites. Related malicious ad networks and redirects can also lead to a virus infection.
Browser hijackers are another source of possible infections. They are malicious extensions that are usually made for the most popular applications – Google Chrome, Mozilla Firefox, Internet Explorer, Safari and Microsoft Edge. Upon installation, the hijackers change the settings of them installed browsers. This includes the default home page, default search engine and default new tabs page. Other dangers include the harvesting of stored account credentials, cookies, bookmarks, settings and etc. The imposed redirects can trigger the Cerber 6 ransomware download.
P2P networks like BitTorrent are also used to spread various malware. They are a popular download source of iliegal content (pirate apps and games), this is the reason why the virus is being actively uploaded to various trackers. Review browser hijacker removal guides if you are infected with one to prevent any ransomware infections.
In rare cases the criminals can opt to launch direct intrusion attempts against their targets by using automated vulnerability testing frameworks. Computer users can protect themselves by always running the latest versions of their installed software. The use of a quality-anti spyware solution also guarantees protection potential malware attacks. It can also remove active infections with only a few mouse clicks.
Exploit Kits such as RIG have been used to spread some of the previous samples.
A quality anti-spyware solution can defend against both the viruses, payload droppers and exploit kits.
Summary of the Cerber 6 Ransomware Virus
| Name |
Cerber 6 |
| File Extensions |
Randomly-named extensions |
| Ransom |
Varies |
| Easy Solution |
You can skip all steps and remove Cerber 6 ransomware with the help of an anti-malware tool. |
|
Manual Solution |
Cerber 6 ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
Cerber 6 Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Cerber 6 Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Cerber 6 Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore Cerber 6 Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



