QSearch virus app invades Mac operating systems with the primary purpose to generate revenue for its developers. It can wreak havoc on your machine once it loads on it. The program is categorized as potentially unwanted. It operates behind your back by changing main settings and then becomes able to generate annoying ads, load on every system start and harvest certain data from browsers it affects. An infection with the nasty QSearch may lead to serious system security issues. If you are a victim of the QSearch Mac virus, you can try to restore and protect your Mac computer by following our illustrated removal guide.
Remove QSearch and Secure macOS
QSearch Manual Removal Guide
Skip all steps and download anti-malware tool that will safely scan and clean your Mac.
Run a free scan and check if your Mac is infected with malware.
SpyHunter for Mac Scanner feature is free. Other features are paid. Here you can review its EULA and Privacy Policy.
Distribution of QSearch browser hijacker on Mac
QSearch is a nasty potentially undesired application – browser hijacker – which has been reported to be infecting Mac devices. At the moment security experts have not been able to identify a single tactic that is being used to infect the targets. We presume that the bad actors are using several of the most important methods to carry out malicious campaigns.
A common way of setting browser hijacker attacks like QSearch is the use of fake Flash Player update notifications. These nasty notifications are propagated on various questionable websites that in turn load in popular browsers as browser redirects. Other cases can utilize complex social engineering tricks and hyperlinks that are specifically made to confuse the intended targets into infecting themselves. Two more scenarios that are used in combination with email messages rely on infected files used as payloads ‒ documents and software installers.
- Infected Software Installers ‒ The criminals craft malicious packages made out of legitimate software installers. They are taken from the official vendor download sites, modified and then posted on online sites or attached (either as file attachments) or linked in the email messages.
- Infected Documents ‒ They represent dangerous files that usually come in the form of some of the most popular document types: rich text documents, spreadsheets and databases. When the users open them up a notification prompt will ask them to enable the built-in scripts (macros). If this is done then the malware is installed on the victim computer.
Malicious browser plugins carriers of QSearch and the associated program can be uploaded to hacker-controlled sites and P2P networks like BitTorrent as well. The hacker operators frequently utilize template design, text and images to create portals that look like legitimate download sources. They may also use domain names that are very similar to legitimate sites and advertise them via pop-ups or ad networks.
The browser hijacker code associated with QSearch may also be found in numerous malware toolbars. They are usually made for the most popular web browsers: Mozilla Firefox, Google Chrome, and Safari. They can be distributed on shady download sites or even on the browsers repositories (such as the Chrome Web Store for Google Chrome) using fake developer accounts.
Impact of QSearch Mac Virus
As we mentioned QSearch is a potentially undesired application of browser hijacker-type. However, QSearch is often considered as a virus by affected users. The good news is that the program is not developed to corrupt macOS and personal files. But it still poses a certain danger to victims’ online security and privacy.
Being classified as a potentially unwanted program, QSearch “virus” harasses online users by delivering numerous intrusive ads in their browsers. As a typical browser hijacker, the primary purpose of this program is to deliver as many ads to infected users as possible. This is due to the fact that the owners of QSearch get paid each time you click on an ad displayed by their nasty services.
The ads may appear during browsing sessions or even when your browser is closed. The intrusive ads can slow down the performance of the browser and the whole system as well. Crashes may happen sometimes. All pop-ups, pop-unders, images, banners and other types of ads injected by QSearch could display phrases like:
- Powered by QSearch
- Ads by QSearch
- Promoted by QSearch
- Displayed by QSearch
- Advertised by QSearch
Additionally, once QSearch establishes its malicious files on the system it is able to harvest specific details from your system and installed browsers. It is a common practice of undesired programs like the discussed one. This could be explained by the fact that malicious intenders attempt to build a complete profile of the victims with all their interests and patterns of online behavior. Then they could deliver targeted content or even sell the records to third-parties of unknown origin.
QSearch ads and all files associated with this infection expose your system at risk of severe malware attacks. Thus, they must be eliminated completely before any privacy and security risks occur. This is why we recommend that all infected users need to remove the active infections by following our in-depth removal guide.
QSearch Removal Guide
If your system is showing infection symptoms, you should definitely take action and remove QSearch and related files from your macOS. The sooner the better! Below you can find our step-by-step Mac virus removal instructions that give you the opportunity to get rid of QSearch either manually or automatically. If you don’t feel comfortable with manual instructions, download a reliable QSearch removal tool that will scan your Mac system for malware and clean it safely for you. If any questions arise, or additional help is needed leave us a comment.
How to Remove QSearch on a Mac Manually
Remove QSearch and related files from OSX.
- 1. Force Quit all suspicious applications.
Go to the Apple menu in the upper-left corner of your screen and choose Force Quit option.
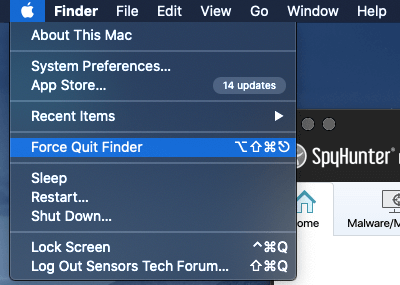
You will see a list of all currently running applications. Go find QSearch, select it and then navigate to the “Force Quit” button. You can also find the last application you installed on your Mac and stop it as well.
Since software bundling is a common propagation method, the QSearch may get installed along with the lastly installed application and their activities on the system may be related.
- 2. Remove QSearch and other related potentially unwanted applications from the Applications folder.
Open the Finder and select the Applications menu. Then search for the unwanted application and drag it to the Trash.

- 3. Мanually look for QSearch in the Libraries of your Mac.
WARNING! You are about to tamper with Library files on Mac. Make sure that you know the name of the virus file. Deleting the wrong file may cause irreversible damage to your MacOS.
Select Go from the top menu bar and navigate to Go to Folder…
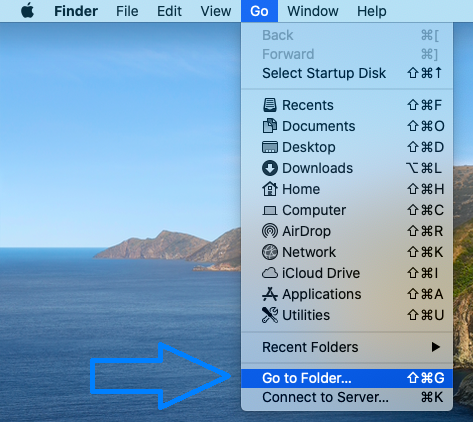
When the window appear start entering the following folder locations one by one:
/Library/Application Support
/Library/LaunchDaemons
~/Library/LaunchAgents
In each folder look for any recently-added suspicious files and move them to the Trash. Examples of files generated by browser hijacker:
- installmac.AppRemoval.plist
- myppes.download.plist
- mykotlerino.ltvbit.plist
- kuklorest.update.plist
Remove QSearch From Your Browser
Remove suspicious browser extensions that can be responsible for the appearance of invasive pop-ups and browser redirects.
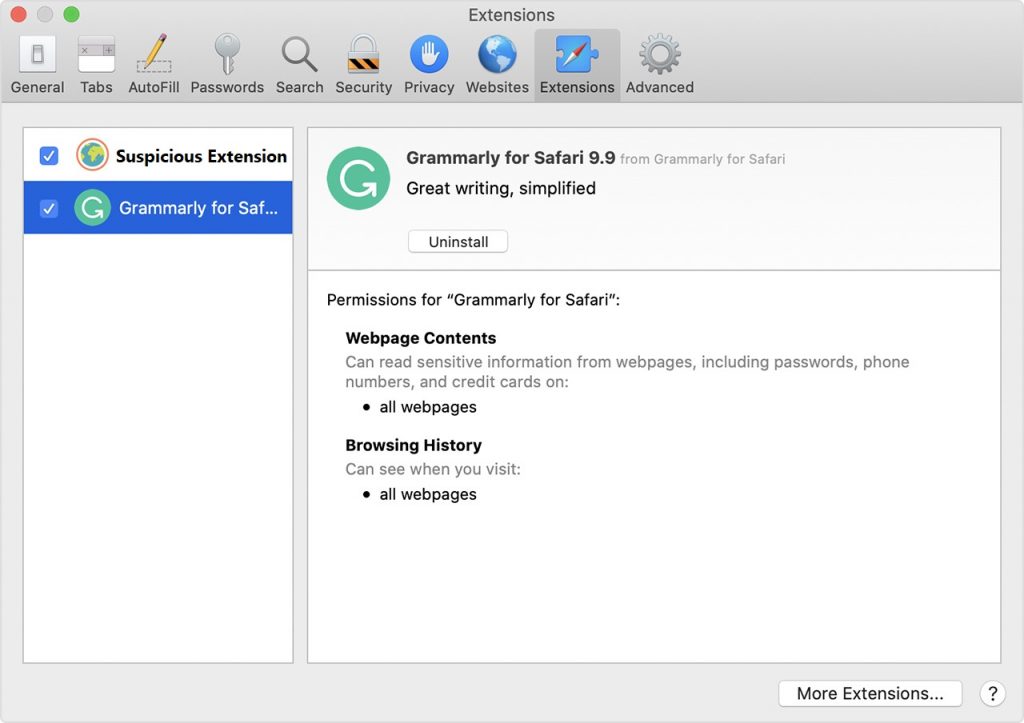
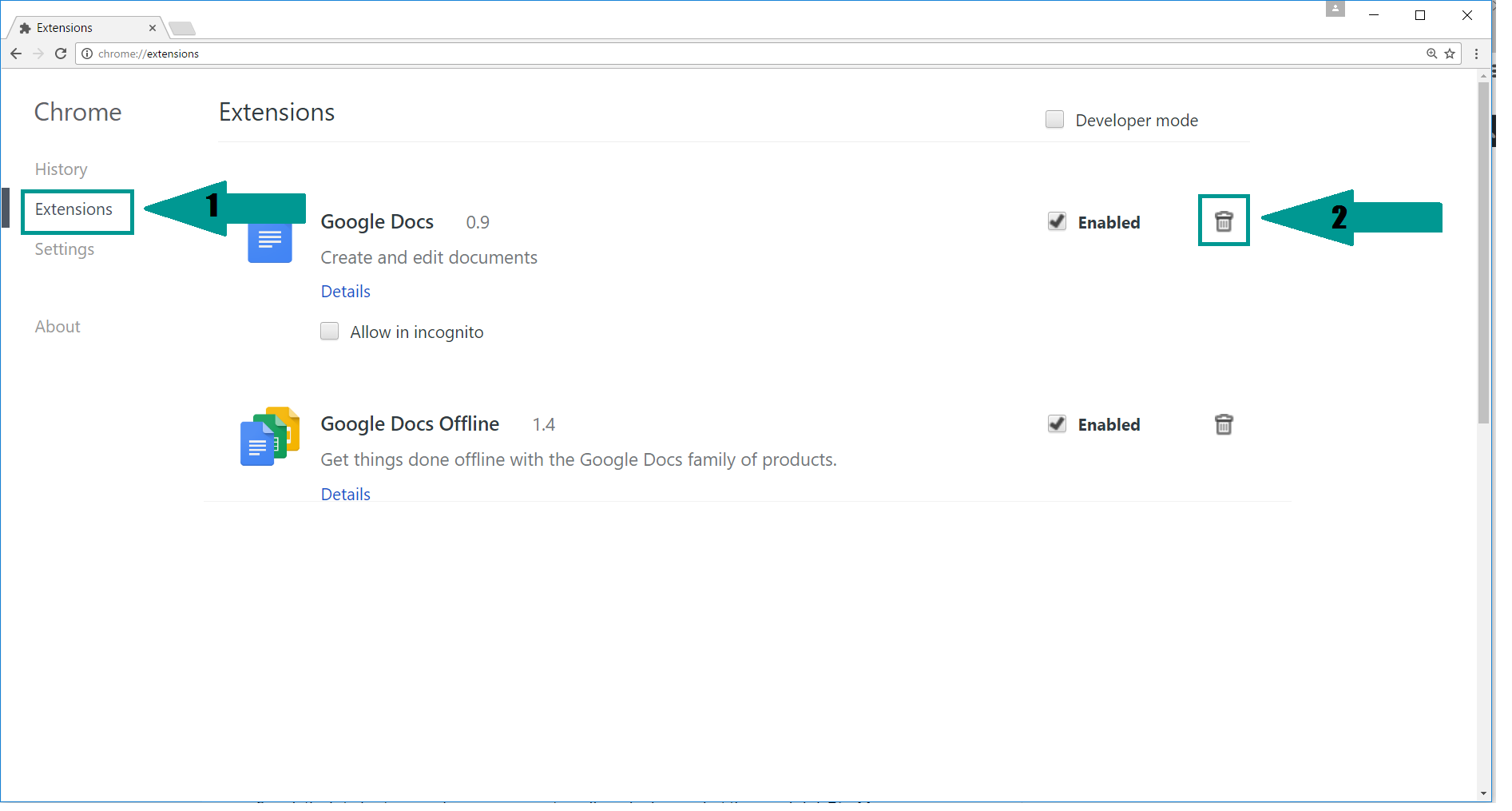
2. Click on the “Extensions” tab. If you see a suspicious or unwanted extension, select it and click “Uninstall“.
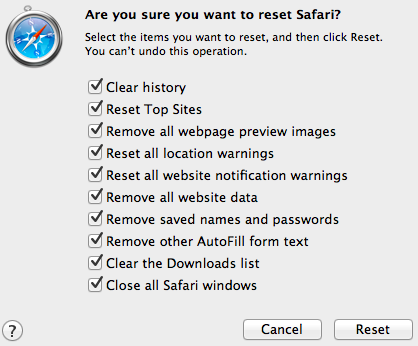
3. Reset Safari web browser. Beware that this step will remove the history as well as some of your saved data. Before you proceed we recommend that you make sure to write down all passwords, logins and important details.
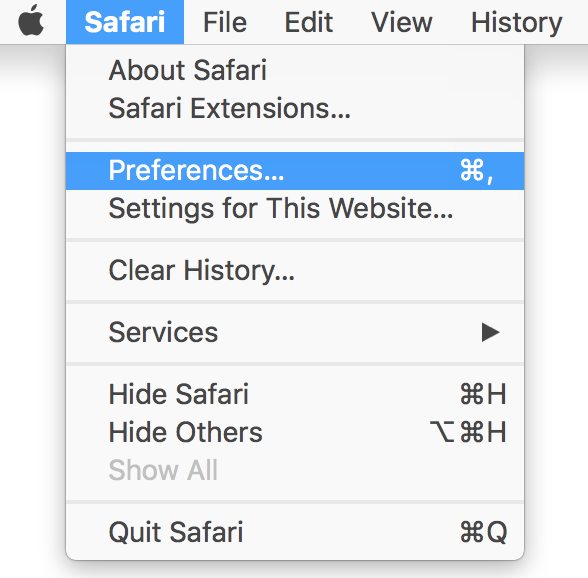
If you are using Safari version 9 or higher open the browser and go to “Preferences“. Then select the “Privacy” tab. When the window appears on screen click on the “Remove All Website Data” button.
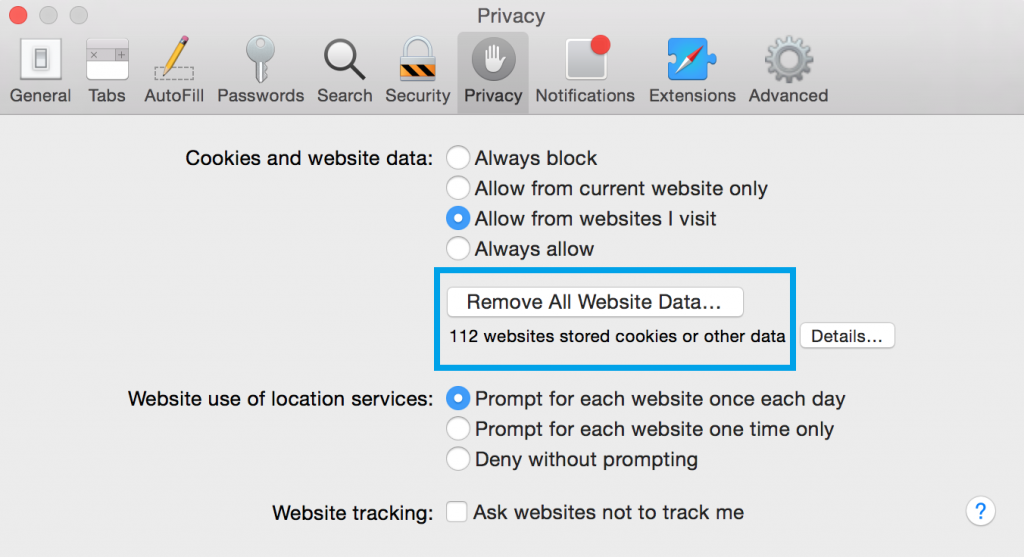
In case that your Safari web browser is running a version from 5 to 8, then just select Safari on the top menu bar and click on “Reset Safari” option. Choose which data to be cleaned from the browser.
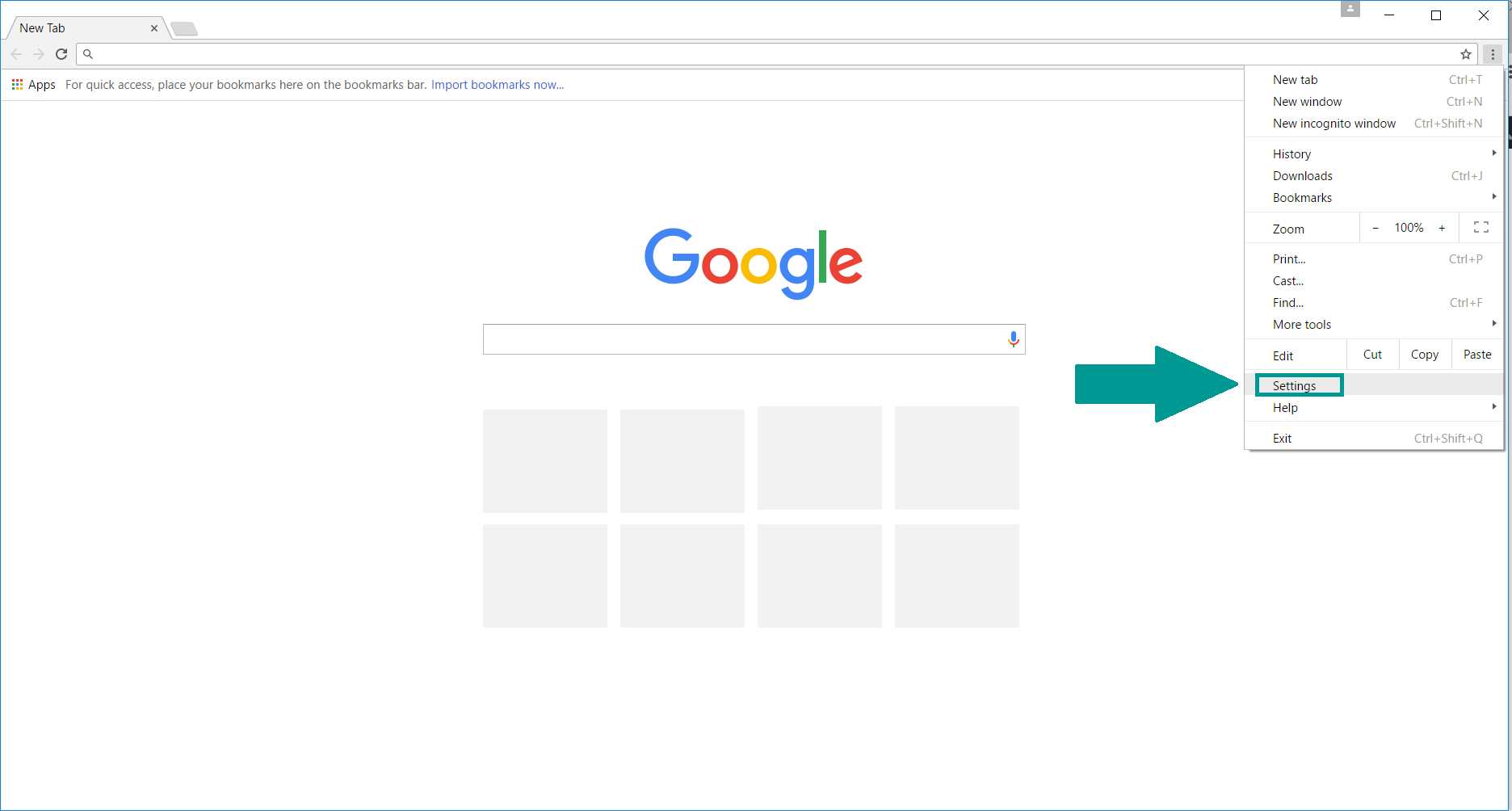
2. Click “Extensions” in the left menu. Then click on the trash bin icon to remove the suspicious extension.
3. Again in the left menu, under Chrome, Click on “Settings“. Go under “On Startup” and set a new page.
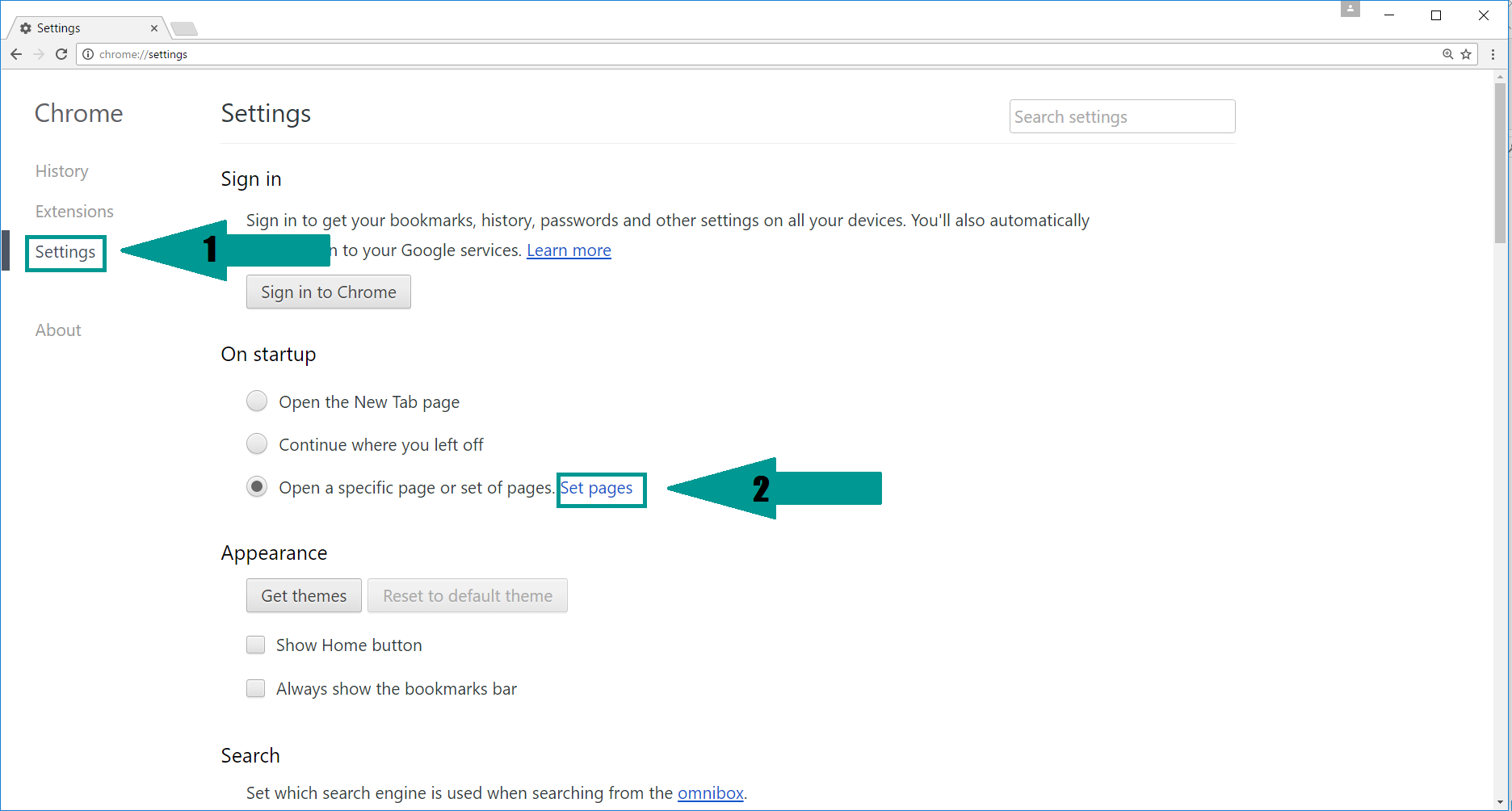
4. Afterward, scroll down to “Search“, click on “Manage search engines“.
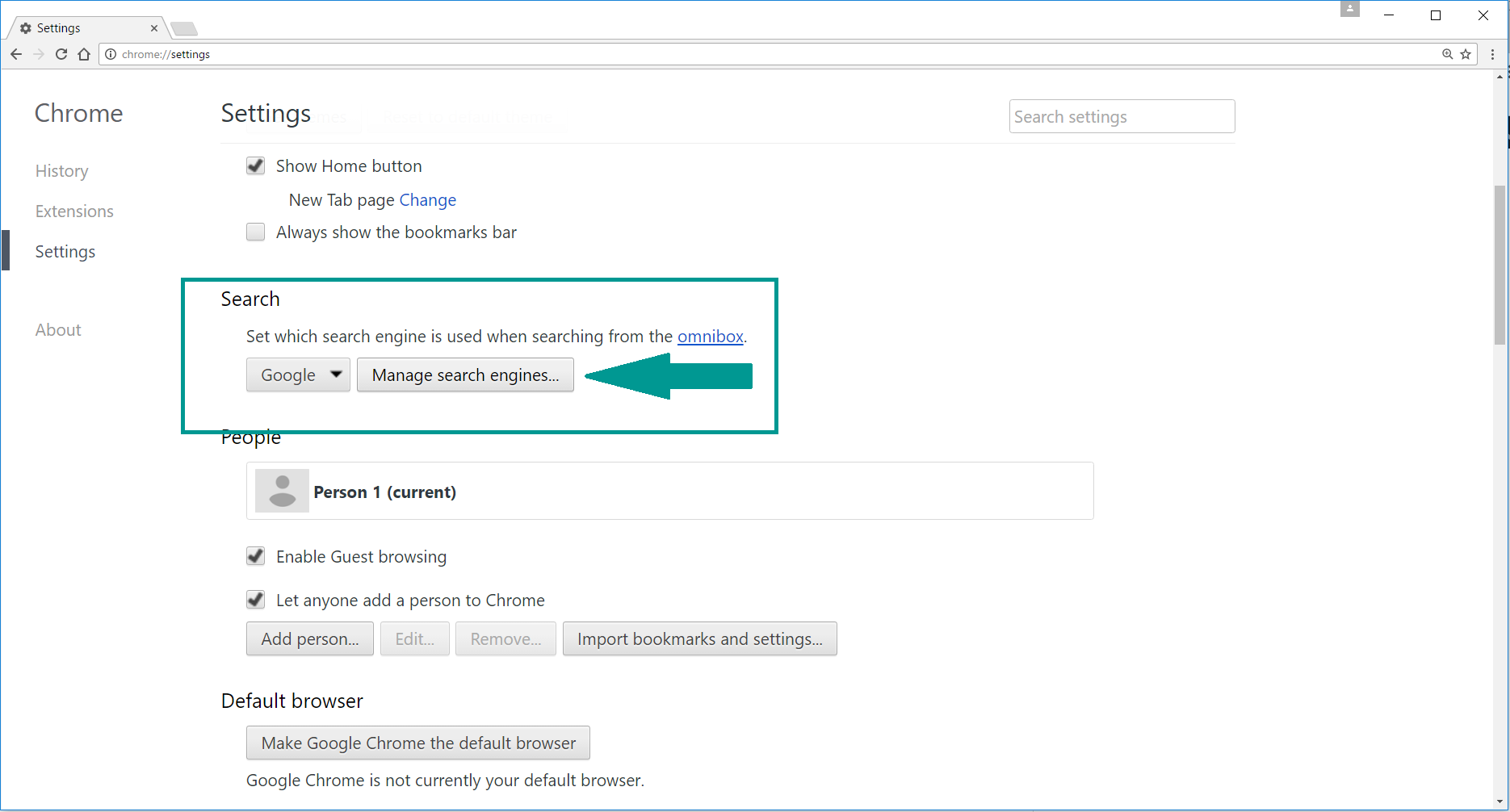
5. In the default search settings list, find the unknown search engine and click on “X“. Then select your search engine of choice and click “Make default“. When you are ready click “Done” button in the right bottom corner.
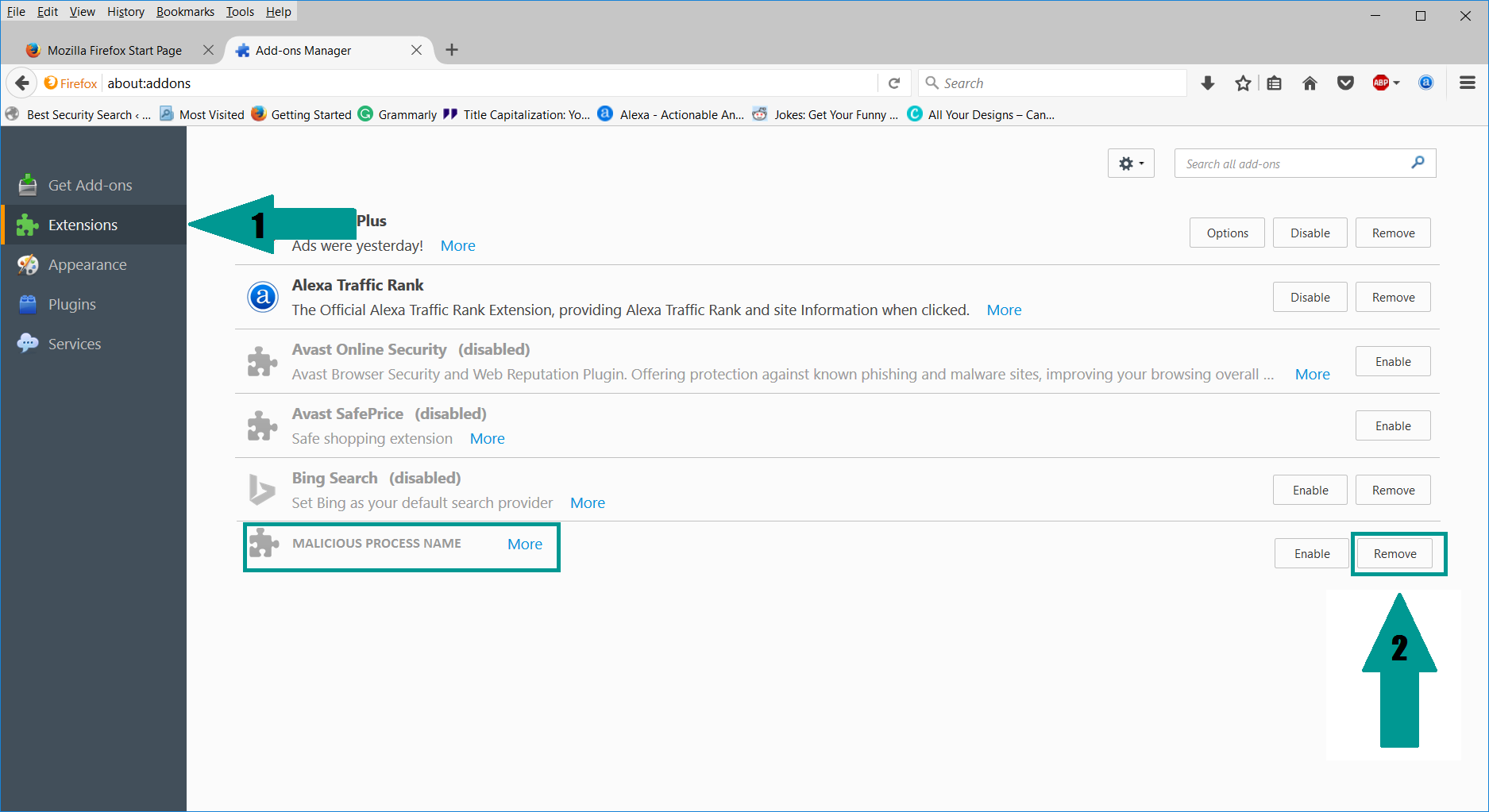
1. Start Mozilla Firefox. In the upper right corner, click on the Open menu icon and select “Add-ons“.

2. Inside the Add-ons Manager select “Extensions“. Search the list of extensions for suspicious entries. If you find any, select them and click “Remove“.
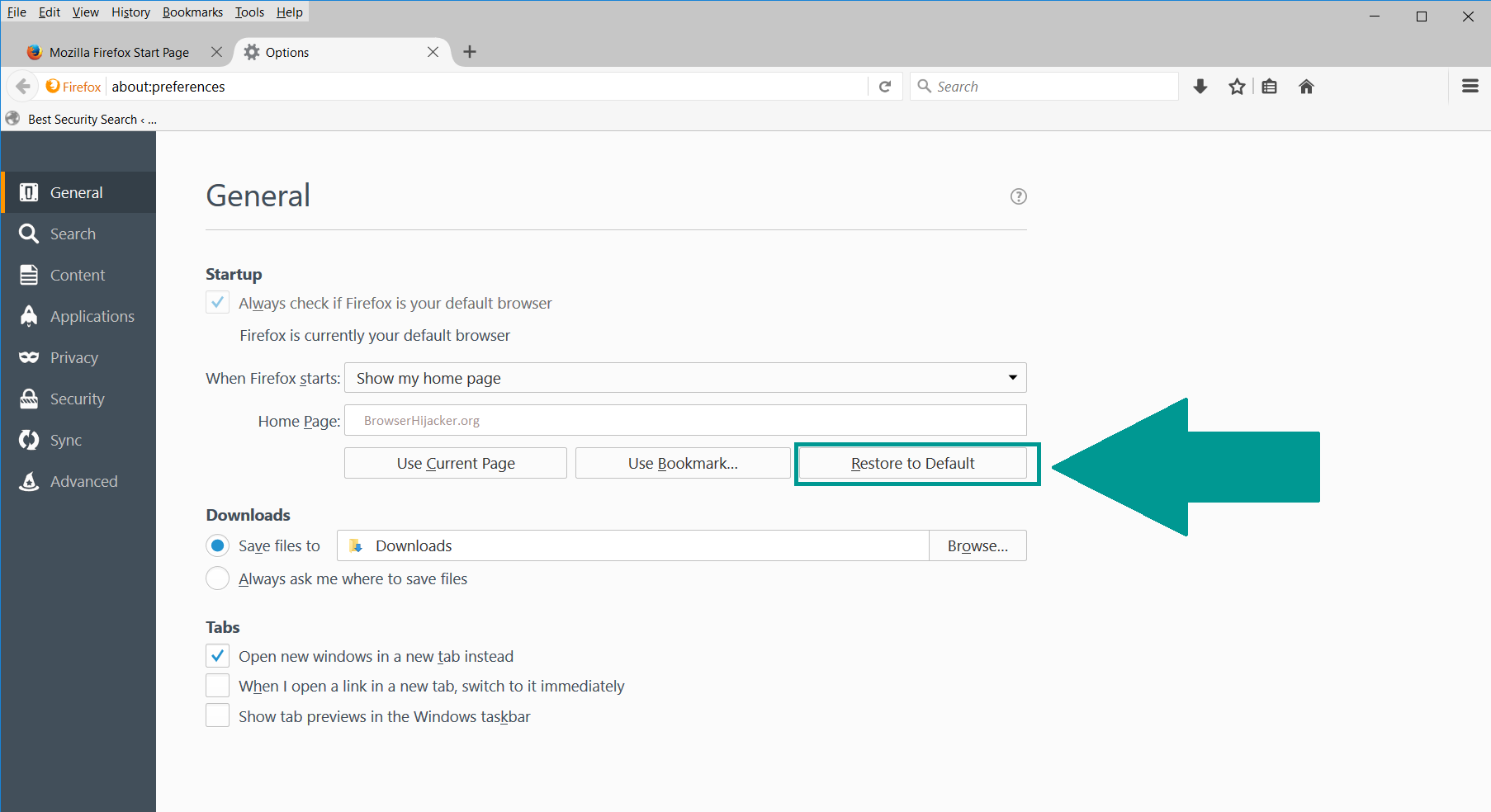
3. Click again on the Open menu icon, then click “Options“.

4. In the Options window, under “General” tab, click “Restore to Default“.
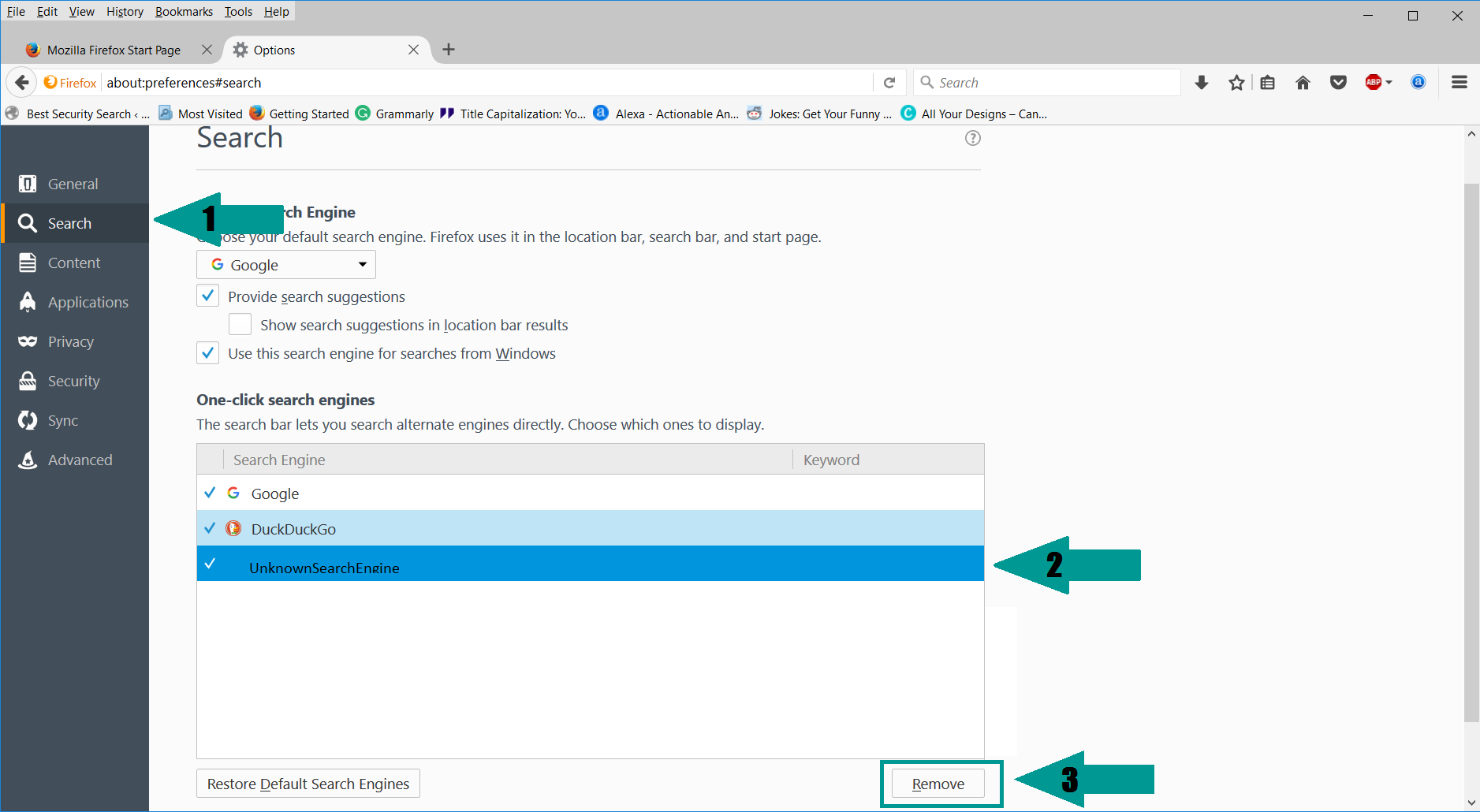
5. Select “Search” in the left menu, mark the unknown search engine and press “Remove”.
Remove QSearch from a Mac Automatically
While the above steps work very well in most of the cases when users’ OSX is infected with PUP or malware, sometimes the Mac virus removal requires the help of a professional application. This anti-malware tool will scan and remove malware from your Mac. It offers an active protection shield and comes with a variety of handy features that will keep your system fast, clean and secure.
DOWNLOAD Antivirus for MacSpyHunter for Mac Scanner feature is free. Other features are paid. Here you can review its EULA and Privacy Policy.



