Pokemon has taken the world by storm since its release in July. Nowadays, you can’t walk in any big town without spotting a few trainers walking around with their eyes stuck to the smartphone. Pokemon GO seems to be everywhere. That includes the cyber-crime world. A Pokemon Go themed ransomware was spotted recently. The malicious software is reportedly developed by Hidden-Tear, the notorious ransomware scammer group.
Specific of the Pokemon Go ransomware Virus
Considering the popularity of Pokemon Go, it’s no surprise that crooks would try to capitalize on its fame. The ransomware is masked to look like a Pokemon Go .exe file. The poke-theme is the only trait that distinguishes this malicious software from your run-of-the-mill ransomware.
The ransomware was reported by Michael Gillespie on Twitter. His tweet also included the icon of the ransomware .exe file.
You can see the tweet bellow:
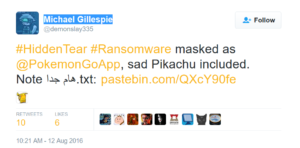
As usual, once the virus gets into your computer, it starts to look for particular files to encrypt.
The file extensions are:
.txt, .pdf, .sql,.rtf, .xlsx, .doc, .mht,.gif, .png, .htm, .xml, .psd, .asp, .aspx, .html,.docx,.xls, .ppt, .odt, .asp, .php,.csv,.mdb, .sln
When the virus finishes encrypting the files, it’ll display a ransom note in Arabic and a contact email: me.blackhat20152015(at)mt2015.com
What sets the Pokemon Go ransomware apart from similar viruses is that it creates a backdoor Windows account on the infected computer. This is very problematic, as it can lead to more complications to cyber security besides the already present threat of encryption. The Pokemon Go ransomware developers can use this account for gaining access to the user’s computer even after they have paid the ransom and have resumed normal usage of the system.
The backdoor account that the virus creates is called Hack3r. The account gains admin rights on the PC.
The ransomware will also add entry to the Windows registry key to ensure it’ll run on boot-up
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon\SpecialAccounts\UserList “Hack3r” = 0
The virus also copies itself on any removable disks that are inserted into the infected PC. That way it can spread to other computers by the infected drive. The scheme works like this; if someone uses a removable disk on a ransomwared computer and then on another computer, the other computer will also get infected. It does this by creating an autorun file. This is the name of the malicious file:
[AutoRun] OPEN=PokemonGo.exe
ICON=PokemonGo.exe
Then the cycle will begin again on the other system.
Pokemon Go Ransomware Is Still in development
The ransomware is likely still being developed, as it uses a static AES key, 123vivalalgerie. The ransomware also uses a private IP address, which means that the virus can’t connect to the Internet. As of now, Pokemon Go is ineffective, but users should be careful, as it’ll likely be finished and released soon.
Here’s a picture of the ransomware note:
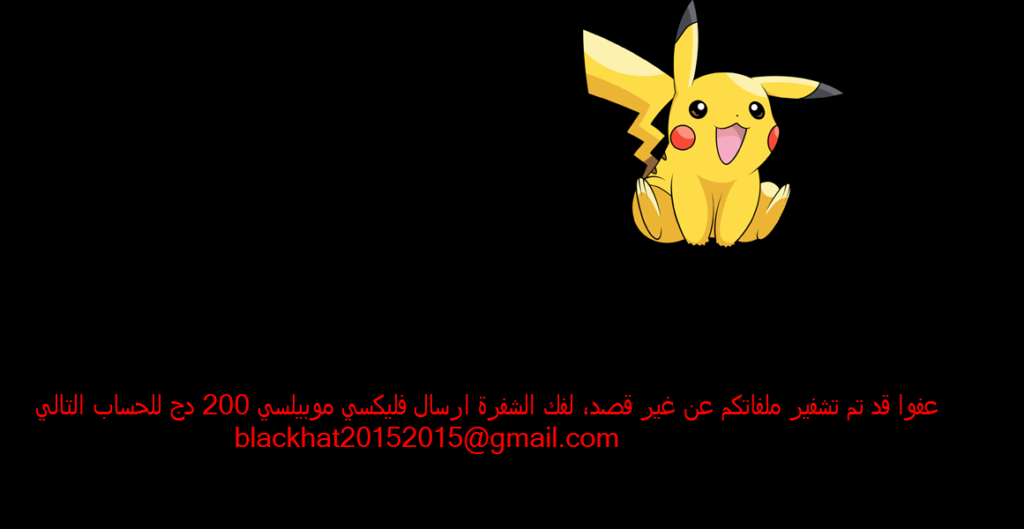
Pokemon Go ransomware targets Arabic victims, as the ransom note is in Arabic. The virus will create that following file on the computer’s desktop هام جدا.txt., Very Important.txt. The note states:
“(: لقد تم تشفير ملفاتكم، لفك الشفرة فلكسي موبيليس للعنوان التالي [email protected] وشكرا على كرمكم مسبقا “
The Google translates the message like this:
“(: Your files have been encrypted, decoding Falaksa Mobilis following address [email protected] and thank you in advance for your generosity “
Pokemon Go ransomware – Summary
The Pokemon Go virus is going to be finished soon, and it’s likely that a lot of users will get infected. The Pokemon mania that swept the world with the release of Niantic’s hit app created a large base of unwitting users who would download Pokemon related content. There have been multiple reports of malicious apps on the Google Play store that mask as Pokemon Go related content. The original app itself has been criticized for requiring excessive permissions, like access to the user’s Google account.
If you get infected by the Pokemon Go ransomware, avoid paying the ransom and try to clear you PC with a decryptor and an anti-malware tool. Don’t give money to people like Hidden-Tear, as that would only add fuel to the fire. Virus scamming is a lucrative enough business as it is. Always check whether there’s any information available for safe removal before giving any money to criminals. It’s always preferable to clear the problem by yourself instead of cooperating with the scammers, as they’re not under any obligation to keep their word and decrypt your files as promised.



