The PEC 2017 ransomware virus is a newly discovered malware that encrypts user data and marks it with the .pec extension. It displays a ransomware note in Italian and primarily infects via malicious office documents made by the hackers. Victims can remove the PEC 2017 ransomware virus by:
- Follow our manual removal guide at bottom of the article, or
- Using a quality virus removal tool.
DOWNLOAD PEC 2017 RANSOMWARE VIRUS REMOVAL TOOL.
PEC 2017 Ransomware Virus Description
The PEC-2017 ransomware is a virus which has been made by an unknown hacker or a hacker collective. The initial security analysis does not show any correlation between these samples and any of the known malware families.
At this moment it features only a single encryption module which targets a predefined list of file type extensions. The processed data includes the most commonly used files such as documents, photos, videos, archives, backups and etc. After this process is complete all of the affected data is renamed using the .pec extension.
The generated PEC 2017 ransomware virus note is written in Italian and is saved into a AIUTO_COME_DECIFRARE_FILE.html file. An English machine-translated version of it reads the following:
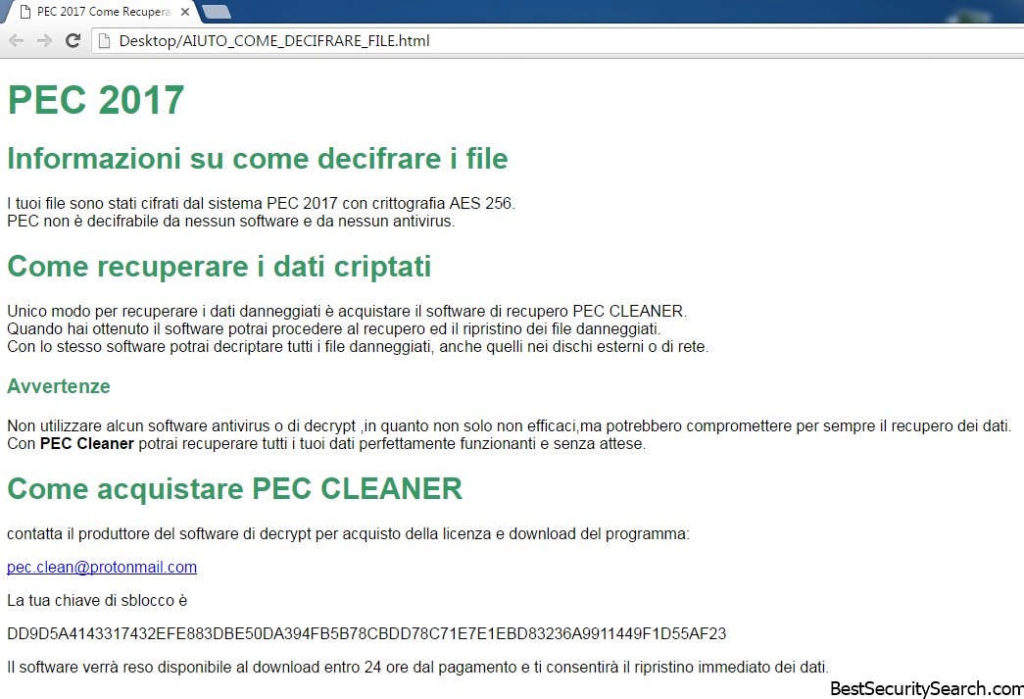
The hackers use the known tactics of explainig to the PEC 2017 ransomware virus victims that the only way of recovering data is to pay a ransomware sum. They make it appear as this is the only possible way of restoring the infected computers and specifically state that the use of a quality anti-virus (or anti-spyware) solution is not required. If the victims want to contact the criminals they can write an email message to an anonymous address. The hackers have opted to use Proton Mail as the email hosting service, this is a anonymous and encrypted system which can be used both directly and as a relay. This sets the PEC 2017 ransomware virus apart from other basic malware that all use popular free solutions like Gmail and Yahoo.
During the infection phase the PEC 2017 ransomware virus has generated an unique machine ID that is also displayed in the PEC 2017 ransomware virus note. A time limit is also stated (24 hours) which further pressures the victims into paying the hackers. Like other similar threats the amount is not defined. This is a widely used tactic where the compromised files have their price adjusted by the operators.
PEC 2017 Ransomware Virus Distribution
The captured samples that are associated with the PEC 2017 ransomware virus indicate that it is placed in a single malicious binary file called languageplugin.exe. This means that there are several possible scenarios that all use social engineering tricks to make the targets download and run it on their computers:
- The File May Pose as a Browser Plugin – Auto translation browser extensions are popular and there is a heavy competition in this industry. The criminals may present the PEC 2017 ransomware virus as a new product or a free version of a legitimate solution.
- Stand Alone Application – The PEC 2017 ransomware virus may be placed in a file that poses as as legitimate standalone translation program.
- Randomly Named Programs – The hackers can use other types of disguise to mask the PEC 2017 ransomware virus.
The PEC 2017 ransomware virus mainly targets Italian-speaking users as its ransomware note (in its current version) displays information only in the Italian language.
The main infection tactic is the use of malicious Microsoft Office documents. The hackers primarily use the CVE-2017-0199 vulnerability. Its full description reads the following:
Microsoft Office 2007 SP3, Microsoft Office 2010 SP2, Microsoft Office 2013 SP1, Microsoft Office 2016, Microsoft Windows Vista SP2, Windows Server 2008 SP2, Windows 7 SP1, Windows 8.1 allow remote attackers to execute arbitrary code via a crafted document, aka “Microsoft Office/WordPad Remote Code Execution Vulnerability w/Windows API.”
This effectively means that the criminals craft Microsoft Office documents (usually Word rich text documents or Excel spreadsheets) that infect the computers when the victims of the PEC 2017 ransomware virus interact with them.
Other ways of distributing the PEC 2017 Ransomware virus is the bundling of the malicious code with legitimate software installers. The operators behind the malware take legitimate software installers of famous applications, games, patches and updates which are modified to include the PEC 2017 ransomware virus code. They are then distributed on hacker-controlled download sites and P2P networks like BitTorrent. In many of the cases the fake apps and sites pose as legitimate copies and sources.
Browser hijackers are another popular source of PEC 2017 ransomware virus infections. They are malicious browser extensions that are usually made for the most popular applications: Google Chrome, Safari, Mozilla Firefox, Microsoft Edge and Internet Explorer. Upon installation they immediately change the default search engine, new tabs page and home page to a hacker-controlled site. Through redirects the PEC 2017 ransomware virus is introduced. In addition they seriously endanger the privacy of the victims by extracting the stored settings, cookies, bookmarks and account credentials. Review browser hijacker removal guides if you are infected with one to prevent any ransomware infections.
Crafted web scripts, ad networks and other internet sites can all attribute to a PEC 2017 ransomware virus infection. Depending on the scale of the ongoing campaign such instances can be created in a semi-automated manner.
Criminals can also opt to launch direct intrusion attempts against their targets by using automated vulnerability testing frameworks. Computer users can protect themselves by always running the latest versions of their installed software. The use of a quality-anti spyware solution also guarantees protection against potential PEC 2017 ransomware virus attacks. It can also remove active infections with only a few mouse clicks.
Summary of the PEC 20176 Ransomware Virus
| Name |
PEC 2017 |
| File Extensions |
.pec |
| Ransom |
Varies |
| Easy Solution |
You can skip all steps and remove PEC 2017 ransomware with the help of an anti-malware tool. |
|
Manual Solution |
PEC 2017 ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
PEC 2017 Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely PEC 2017 Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover .pec Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore .pec Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



