
Computer hackers are actively exploiting a critical issue (CVE-2017-0199) in Microsoft Word via a large-scale email campaign, read our article to learn more about the problem.
The Microsoft Word Vulnerability (CVE-2017-0199) Used In Email Scams
Security specialists discovered that computer hackers are taking advantage of a Microsoft Word vulnerability – CVE-2017-0199. The alarming fact is that even the latest version Office 2016 has been identified as vulnereable. The criminals have used a global email spam campaign to distribute malware to a large group of target users. The infection process follows a predefined pattern:
-
The emails are crafted and sent to the targets via hacked email servers or a botnet.
-
The targets receive email messages that contain various content templates. The emails themselves feature file attachments in the form of RTF files encoded with the DOC file type extension.
-
When the user interacts with the file it connects to a remote server and downloads a file from it. It contains HTML code which is executed as a HTA file.
-
As a consequence of this the attackers gain full remote control execution privileges on the affected machines.
During the network analysis the researchers uncovered that the HTA content is disguised as an ordinary rich text file (RTF) with the intent of evading some of the security engines used by anti-virus products. However malicious Visual Basic (VB) scripts were found in parts of the file. When the exploit has complete its built-in pattern it pop ups a fake Microsoft Word application window. This is done to distract the users from the infection process.
The vulnerability is caused by the zero-day vulnerability that is associated with malicious Windows Object Linking and Embedding (OLE) abuse. This is an important feature of all Microsoft Office suite applications as it allows the users to use various types of files in their documents. The Microsoft Security response Center has been contacted with details about the discovered samples and the impacted victims.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Dridex Trojan Distribution
It appears that the Protected View can protect against possible abuse which is why the experts advise end users to take advantage of it. The latest wave has been used to carry the dangerous Dridex Trojan. According to Proofpoint security the spam wave consists of millions of email sent to targets globally. However most of them are located in Australia. This can mean that some of the members of the hacker collective behind the emails may be Australian. The second wave carried email messages that resemble document scans. This is also the first instance in which the Dridex hackers are using an unpatched zero day vulnerability to spread the Trojan. Microsoft has already started rolling out updates for Microsoft Word that fixes the issue.
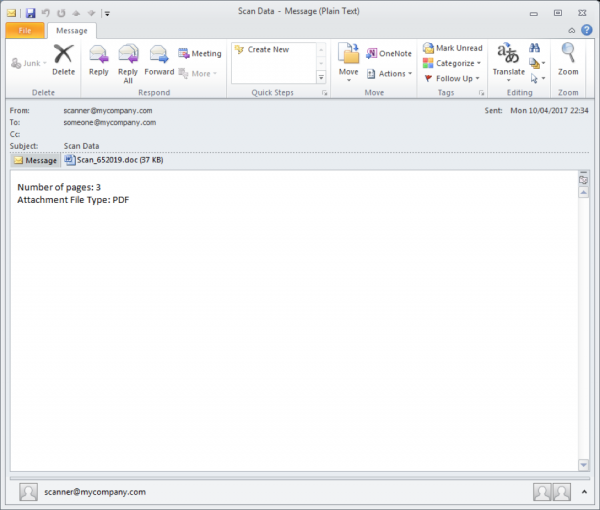
The emails follow a template-based system of naming the messages:
-
The senders appear to be customized from a list that follow a predefined pattern: ‘<[device]@[recipient’s domain]>‘. [device]. Possible combinations include: copier, documents, noreply, no-reply or scanner.
-
The subject lines in all cases are “Scan Data”.
-
The attachments are either DOC or PDF files which are named as “SCAN_[random-digits].XXX”.
The Dridex trojan samples have been configured to detect if the users access banking portals of Australian banks and other popular websites such. It injects phishing forms and pages into the browsers in an attempt to steal account credentials. This means that it is compatible with the most commonly used web browsers: Mozilla Firefox, Google Chrome, Microsoft Edge and Internet Explorer.
The discovered issue in the popular productivity application has already been patched by Microsoft. The security update For Microsoft Office KB3141538 released during the last Patch Tuesday fixes the critical CVE-2017-0199. All Microsoft Office users are recommended to apply the patch as soon as possible.
|
As always we recommend that all users refrain from opening up files obtained from untrusted locations – P2P networks, email messages, download sites and etc. A quality anti-malware solution can effectively guard against intrusion attempts and remove all active infections with a few mouse clicks. |
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



