Intel Security and Kaspersky lab cooperated on a project with NoMoreRansom, the Dutch police and the European Cybercrime Centre to combat the dangerous ransomware infection known as the WildFire virus. The joint operation has produced decryption tools, that you can download from here.
The WildFire Ransomware
The WildFire crypto-virus surfaced on the web in mid-2016. WildFire encrypts the files of infected users and demands 1,5 BTC, around $900 for their encryption. In reality, most users payed around 0,5 BTC, around $300. A user who had some bargaining skills could lower the price, depending on what the scammers would accept. The virus infected victims mainly in the Netherlands and Belgium. The virus encrypted filed with the military grade algorithm AES – 256, which is very strong and hard to crack.
Picture of the Ransomware Note:
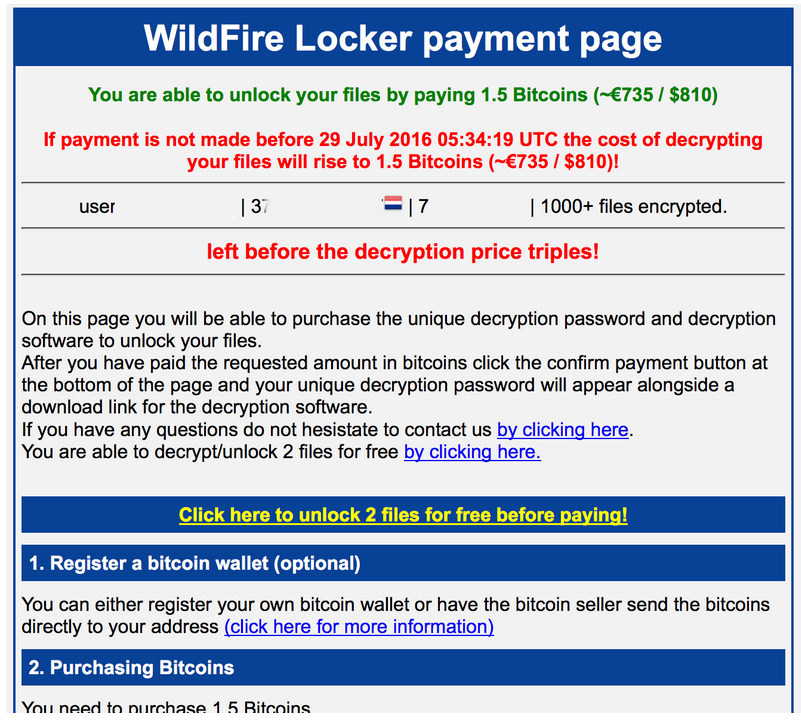
The ransomware was distributed by email spam. The emails mimicked Dutch transport companies. The fake emails contained information in Dutch and warned about non-existing delivery problems. Once the victims click on it, the virus infects the system and starts encrypting important files, like documents, pictures, videos.
Who Is Responsible?
The group that created the WildFire ransomware is likely from eastern Europe, as they use Ru(Russia) and SU (Soviet Union) domains to communicate with virus victims. Involvement by Dutch cybercriminals is also suspected, as the infected emails were written in good Dutch, looked very authentic, and even contained genuine information about existing businesses in the Netherlands. Ransomware is a worldwide problem, but there aре а lot of scams originating in former Soviet bloc countries, mainly Russia.
The Threat of Ransomware Is Only Increasing
The ransomware business is heating up. There are hundreds of viruses created every day. The low risk and high reward of the scams make them a very lucrative business. There are rumors of entire branches of the Russian mob dedicated to ransomware. The crooks behind the Cerber ransomware bank close to a million dollars a year. And that’s just a single branch of the giant ransomware tree. More ransomware kits pop-up every day. Nowadays, it’s now even necessary for crooks to have the know-how to create a virus, they can just base their ransomware on a pre-existing variant. That’s what the Shark ransomwareproject and similar ransomware are all about. Hospitals are especially threatened from ransomware, as they often lack the necessary cyber-security to combat the threats. The crooks take full advantage of that and often infect healthcare institutions with ransomware for a quick cash-grab.



