Exotic 2.0 is the updated version of the Exotic ransomware virus. The virus extension remains the same – .exotic. The relatively short timeframe between the 2.0 update and the old version of the virus makes us think that the developers of Exotic don’t have much faith in their work. The ransom sum of $50 is also fairly small compared to other viruses. Here’s all you need to know to protect yourself from the virus.
| Name |
Exotic 2.0 Ransomware |
| File Extensions |
.exotic |
| Ransom |
50 US Dollars |
| Solution #1 |
Exotic 2.0 Ransomware can be removed easily with the help of an anti-malware tool, a program that will clean your computer from the virus, remove any additional cyber-security threats, and protect you in the future. |
|
Solution #2 |
Exotic 2.0 Ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Exotic 2.0 ransomware is distributed mainly through spam email campaigns that link or contain infected binary files. |
Exotic 2.0 Ransomware Virus – Distribution
Exotic 2.0 can sneak into your system through infectious emails. Spam is a popular way to spread malware. 2016 marked the beginning of a massive spike in spam.
There’s an ironic development in spam protection. Right now, email hosting sites often utilize effective filters that block most malicious letters. However, that puts users into a false sense of security. Users are more likely to click on emails since they trust the anti-spam systems.
You can’t be 100% from infection, but if you avoid opening the following types of emails, you’ll be much safer from ransomware and other malware types:
- Emails sent from weird addresses, claiming to be from a legitimate company
- Emails that include .zip files or other archives
- If you download an attachment, don’t open it
The Exotic 2.0 is a relatively new virus, so the specific methods of distribution remain unknown. If you have any relevant information, post it in the comment section or contact a cyber-security developer. That can help with the fight against the virus and help to decrypt your files.
Exotic 2.0 Ransomware Virus – Tech Details
The infectious file that starts the Exotic 2.0 process of encryption is probably a .exe or a .dll. The virus will encrypt many important files. Exotic 2.0 aims at these types of files:
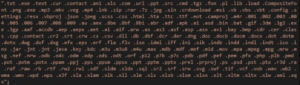
Exotic 2.0 was created by a ransomware developer known as “eviltwin.” His appalling English is displayed in Exotic’s ransom note:
YOU ARE INFECTED BY THE EXOTIC VIRUS
DON’T TRY TO DELETE OR KILL THE VIRUS OR YOUR FILES ARE GONE SEND US 50 USD IN WORTH OF BITCOINS TO THIS ADDRESS [BTC wallet address] ~ HAVE A NICE DAY =)
All encrypted files will have the .exotic extension added at the end of their name, and the original file name will be randomized. Here’s an example:
Importantfiles.jpg become UIo125Y.exotic
This is done to avoid detection and make it harder for users to find important files.
Remove Exotic 2.0 and Protect Your Computer From Future Threats
Don’t listen to the ransom note. If your computer is compromised, you should remove the virus before it causes more damage. You can do that in the following ways:
- Remove Exotic 2.0 with an anti-malware program
- Remove it manually by following the detailed guide bellow
The first option is preferable for users lacking technical skills. An anti-malware program is also a good investment in your future cyber-security. Ransomware viruses can cost you hundreds of dollars in damages. That’s why it always pays to have extra protection against malware.
Exotic 2.0 Ransomware Removal
For a faster solution, you can run a scan with an advanced malware removal tool and delete Exotic 2.0 completely with a few mouse clicks.
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Exotic 2.0 Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
-
1) Use present backups
2) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



