UltraLocker is the name given to a malware of ransomware type. UltraLocker is malicious software developed to block access to a computer system until a ransom is paid. Upon encryption of target data, it is designed to insert the infix .locked between the original file name and its original extension. Keep reading and learn how to deal with UltraLocker in case you are a victim of this cryptovirus.
| Name |
UltraLocker |
| File Infix |
.locked |
| Ransom |
$1000 in Bitcoins | Special Feature |
Screen Lock Function |
| Solution #1 |
Remove UltraLocker ransomware with the help of an anti-malware tool. |
|
Solution #2 |
UltraLocker ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
UltraLocker Ransomware in Details
First, let’s be sure that you are infected with exactly this ransomware. In this paragraph will describe its distinguishing features.
UltraLocker is a new variant of CryptoWire ransomware. This means that it is developed on the basis of CryptoWire ransomware project.
UltraLocker is using strong AES (256) encryption algorithm that transforms the files making them useless without the password (decryption key). The encrypted data cannot be read and once encrypted the infix .locked is injected between the file name and its original extension. The template is original_file_name.locked.original_file_extension and if you have a document file with the name “work“ – work.docx, UltraLocker ransomware will rename it to work.locked.docx. The threat is probably configured to encrypt your music and video files, documents, PDF files, images, etc.
The developers of UltraLocker ransomware store the decryption key on a remote server that is under their control. They are trying to extort a ransom payment by the victims and require an amount of $1000 in Bitcoins (Digital currency) for the decryption key of .locked files.
The ransomware has the function to lock your screen by displaying its ransom message called Ultralocker. It is reported to look like this:
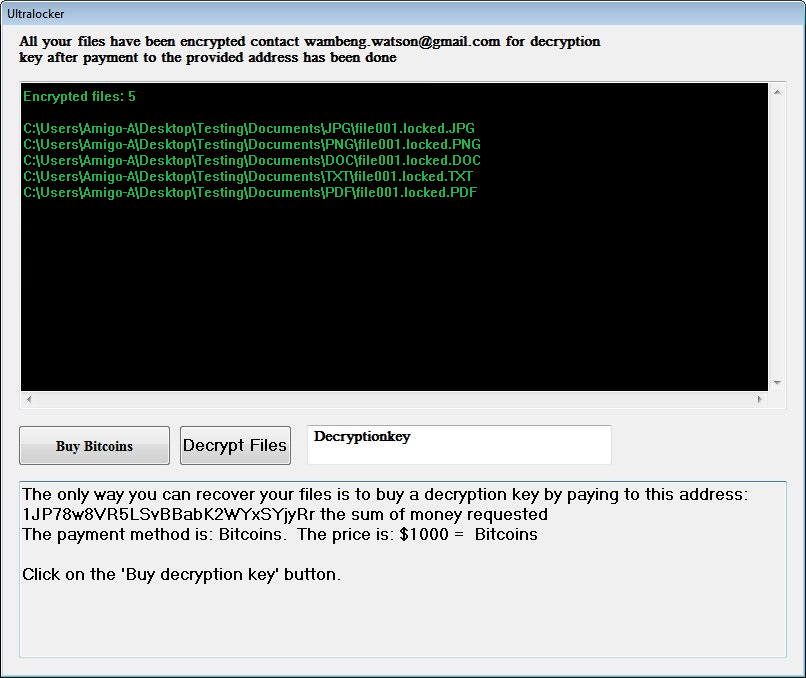
And the text on it reads:
“All your files have been encrypted contact [email protected] for decryption key after payment to the provided address has been done.
Encrypted files: /number of the encrypted files/
/Their exact locations on the system/
The only way you can recover your files is to buy decryption key by paying to this address: 1JP78w8VR5LSyBBab***** the sum of money requested.
The payment method is: Bitcoins. The price is $1000 = Bitcoins
Click on the ‘Buy decryption key’ button.”
There are two buttons one “Buy Bitcoins” and other “Decrypt Files”. The decryption of the .locked files is possible when the decryption key is written in a field “Decryptionkey” that is again on the windows displayed by UltraLocker ransomware.
We advise you to reject any contacts with the crooks. They often are trying to mislead you that when you submit a payment, they will send you a working solution. There is no guarantee that they have a working decryption key that will restore your .locked files, so if you pay you might only get scammed.
How Cyber Crimminals Deliver UltraLocker Ransomware
As reported UltraLocker ransomware is detected to be distributed mainly through spam email that contains a malicious document attachment with the name Quotation200809.doc. Have in mind that the attachment may be another one. It could be .ZIP or .RAR file that may contain malicious JavaScript or HTML files.
However, the malicious intenders often use several infection vectors and malvertising (short for malicious advertising) is one of them. Malvertising is a process of injecting malicious code in advertisements that are displayed on legitimate online web pages. If you click on such compromised ad – a popup, box message or banner, the result is automatic and most of the cases unnoticed download of the UltraLocker’s malicious payloads on your computer.
Remove UlraLocker Ransomware and Try to Restore .Locked Files
The removal of malicious UltraLocker’s files and objects that allow its successful execution is obligatory. Otherwise, the hackers may find a way to grant access to your PC and infect you with another malware, steal sensitive data, etc. Below you can find a guide that provides sequential removal steps that will help you clean your system from this notorious ransomware.
In case that you prefer to remove the threat by your own here is a list of files and objects associated with UltraLocker:
- Quotation200809.doc
- Quotation1.exe
- Art work sample.exe
- README.txt
The malicious files may be located in several Windows folders including:
- %AppData%
- %Temp%
- %Roaming%
- %User’sProfileName%
- %System32%
Once you find out their location, make sure to delete them. If you have any doubts that UltraLocker still exists on your computer we advise you to consider the use of anti-malware software. Еxcept that it will remove completely the cryptovirus it will keep you away from all types of malware in future.
As UltraLocker is based on CryptoWire source code, we could guess that once a decryptor for CryptoWire ransomware is available it will work for UltraLocker too. As soon as this happens, we will update the information in this article so you can easily find how to decrypt your .locked files.
Meanwhile, you can try to recover any .locked files with the help of data recovery software. Either free or paid. You can prevent future data loss simply by creating backup copies of all your important files. The safest storage way is on an external drive or USB flash drive.
UltraLocker Ransomware Removal
For a faster solution, you can run a scan with an advanced malware removal tool and delete UltraLocker completely with a few mouse clicks.
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely UltraLocker Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
-
1) Use present backups
2) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



