Computer criminals are using large-scale spam campaigns and novel techniques that distribute the Cerber ransomware to a variety of targets.
Cerber Ransomware Distribution on a Large Scale
Security researchers have discovered that computer criminals have started several large-scale spam email campaigns that deliver the latest strain of the Cerber ransomware known as 5.0.1. The new distribution techniques rely on novel infection vectors which utilize proxy servers such as Google and Tor2Web.
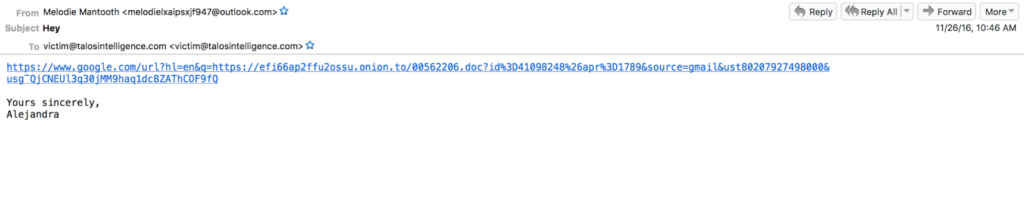
The identified Cerber ransomware campaign has started on November 24 and has been actively involved in targeting a variety of computer hosts. The email messages were distributed with legitimate signature blocks and contained various social engineering tricks which are popular among the criminals.
The messages use malicious Google redirections and the Tor2Web proxy service to evade detection by anti-spyware solutions and make recovery more difficult.
The associated email messages contain hyperlinks that pose as files that may be of interest to the recipients – photos, order details, financial documents, transaction logs and etc. The subject lines contain the name of the recipient which makes them appear more legitimate as compared to other similar attacks.
The contained hyperlinks use Google redirections which point to the malicious payload which is hosted on the anonymous TOR network. The “onion.to” domain is used in the initial redirection link to enable the malicious operators to use the Tor2Web proxy service. This makes it possible to access the anonymous network without downloading and installing the TOR client. Such techniques are used by some of the popular exploit kits such as Nuclear.
Email subjects include the following:
- Hi
- How are you
- Howdy
- Hello
- Hey
- Whats up
The fact that the payload is hosted on the TOR network makes it much more difficult to take it down. The attackers can also modify the redirection chain at will in a quick manner to bypass any blacklisting measures which may be set by the network administrators who have identified the threat.
When the victim clicks on the link an infected MS Word document is downloaded that acts as the payload downloader for the Cerber ransomware. The document uses the Windows Command Processor to run a Powershell command which downloads and executes the Cerber executable. The attackers have used various obfuscation and evasion techniques to make detection difficult.
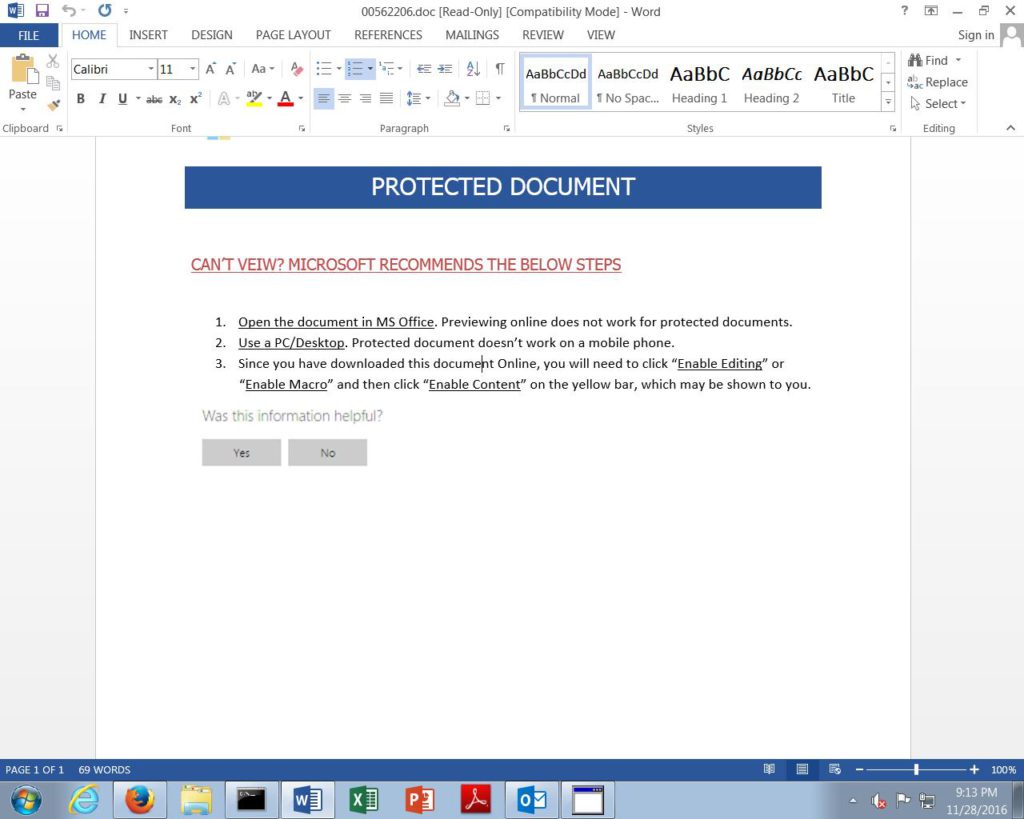
Upon successful infection the Cerber 5.0.1 ransomware is executed. The attackers have used the strain to demand a ransomware fee of 1.3649 Bitcoins which is about 1000 US Dollars. The attackers have used a five day limit after which the sum is raised to 2.7298 Bitcoins.



