A new attack method utilizes WPAD protocol and PAC files and allows the hackers to get the complete information about all HTTPS URLs visited by the user. Alex Chapman and Paul Stone who are working in the UK cyber security and consultancy firm, Context have made the discovery.
More About WPAD Protocol and PAD Files
WPAD protocol or Web Proxy Auto-Discovery Protocol is a type of protocol that has the function to fetch the proxy configuration file of the URLs. The fetching is realized through PAC files. A PAC file is the acronym of Proxy Auto-Config File. This file is responsible for the proxy configuration. It contains a JavaScript function that sends back a string with specifications of the access method to a given URL. PAC files are used when fetching a given URL. Web browsers and user agents receive PAC files that tell them which proxy server to use when trying to reach a given URL.
The Sniffing Attack Through WPAD Protocol and PAD Files
Many web browsers and operating systems deal with PAC files. The default proxy settings in Windows give permissions to the applications and web browsers to auto-discover PAC files via Web Proxy Auto-Discovery (WPAD) protocol. If the attackers successfully damage the WPAD protocol they can grant them access to the PAC files. They can sniff for the transition of PAC files, and once they detect them, they can insert malicious code in them. Thus the JavaScript code allows them to monitor every request you make through your browser and the full HTTPS URL.
Some attacks that aim to sniff HTTPS traffic allows the attackers to see only the main part of the URL. In this case, the researchers explain that the attack technique that uses PAC files for sniffing can grant access to the full URL. This includes leaking of the path and the parameters of the HTTPS URL due to the functions of PAC files. Thus delicate information about your search terms and websites logins is exposed at risk of leaking. WPAD attacks hide huge danger because an attacker can make various nasty things once he has access to your web traffic. The content of all visited pages that are non-encrypted can be seen. The HTTPS protocol should avoid man-in-the-middle attacks but obviously that’s only in theory.
The experts from Context show how a simple PAC file may look:
if (host.indexOf(‘initech.corp’) >= 0)
return ‘proxy.initech.corp’;
return ‘DIRECT’;
}
How to Prevent a WPAD Man-In-The-Middle Attack
If you are a Chrome, Android, iOS or OS X user make sure you have installed the latest updates. You are prevented if you are using the latest versions of the products.
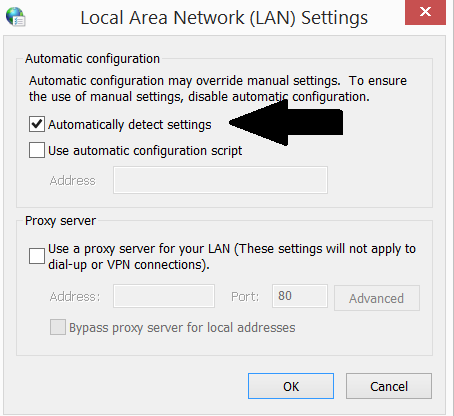
When it comes to Windows, the one of the default settings of the Internet Properties should be disabled. It is the ‘automatically detect settings’ option in the LAN settings. Now we will take you there step-by-step:
1) Press and hold ”Windows key” + “R”
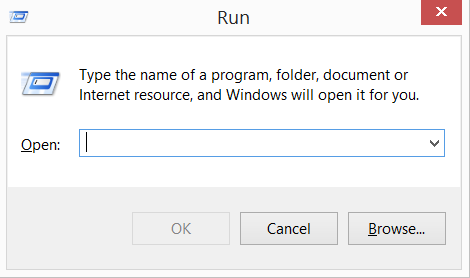
2) In the field type “inetcpl.cpl”
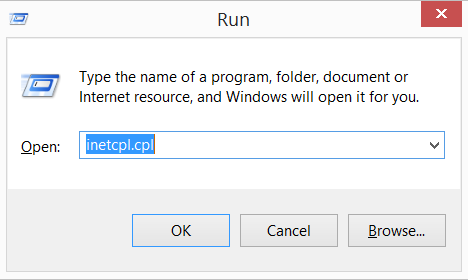
3) Go to tab “Connections”
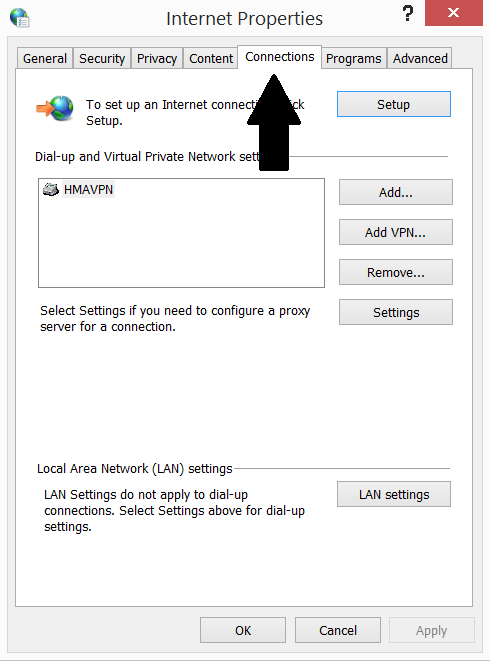
4) Click on “LAN settings” button
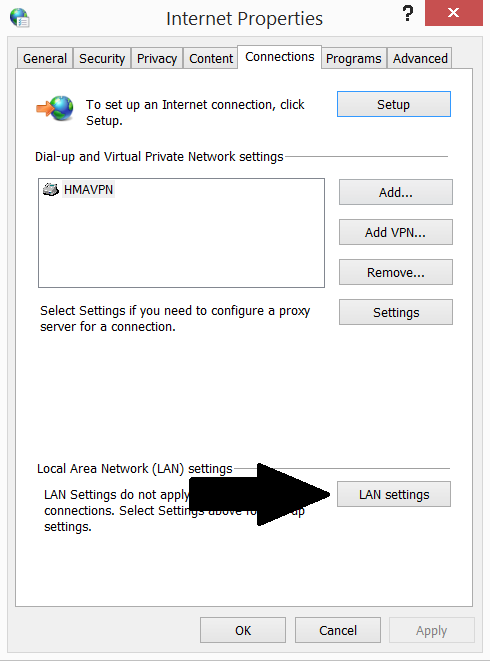
5) Unmark the “Automatically detect settings” option
See also: How to Stop Google from Tracking Your Browser



