Victims of the dangerous WannaCry ransomware can attempt to recover their files by using a freely available decryptor created by the security community. The utility is designed to restore WannaCry ransomware files and data on some versions of the Microsoft Windows operating system.
WannaCry Ransomware Decryptor Overview
Computer users affected by the WannaCry ransomware can try to recover the affected files by using a ready-made decryptor. The utility has been created by security community that investigated the WannaCry virus soon after the large-scale attack campaign started to infect targets across the world. Its effective only in cases where it is run after the infection has been complete as it relies on a memory issue that is present in the majority of the malware samples. The decryptor is able to crack the code using mathematical functions with prime numbers that can decrypt the cipher. It works by analyzing the process memory of the main virus module which is responsible for creating the public and private key pairs. If the computer is rebooted or shutdown the decryptor will not work as the memory state is lost during a power event.
The WannaCry decryptor is an updated version of an earlier version that works only on Microsoft Windows XP. The revised program works for all versions up to Windows 7 (Windows XP, 2003, Vista and Windows 7). The original encrypted files (with the .WNCRY extension) remain unchanged. All decrypted are created separately, this means that there should be enough disk space on the computer to accommodate the data.
WannaCry Ransomware Decryptor Recovery Instructions
It’s very easy to use start the decryption process by reading our guide. Victims can attempt to restore their computers and recover their data by following three simple steps:
- Download The Decryptor – Click here to download the decryptor utility from our site. When this is done unzip the archive in a new folder.
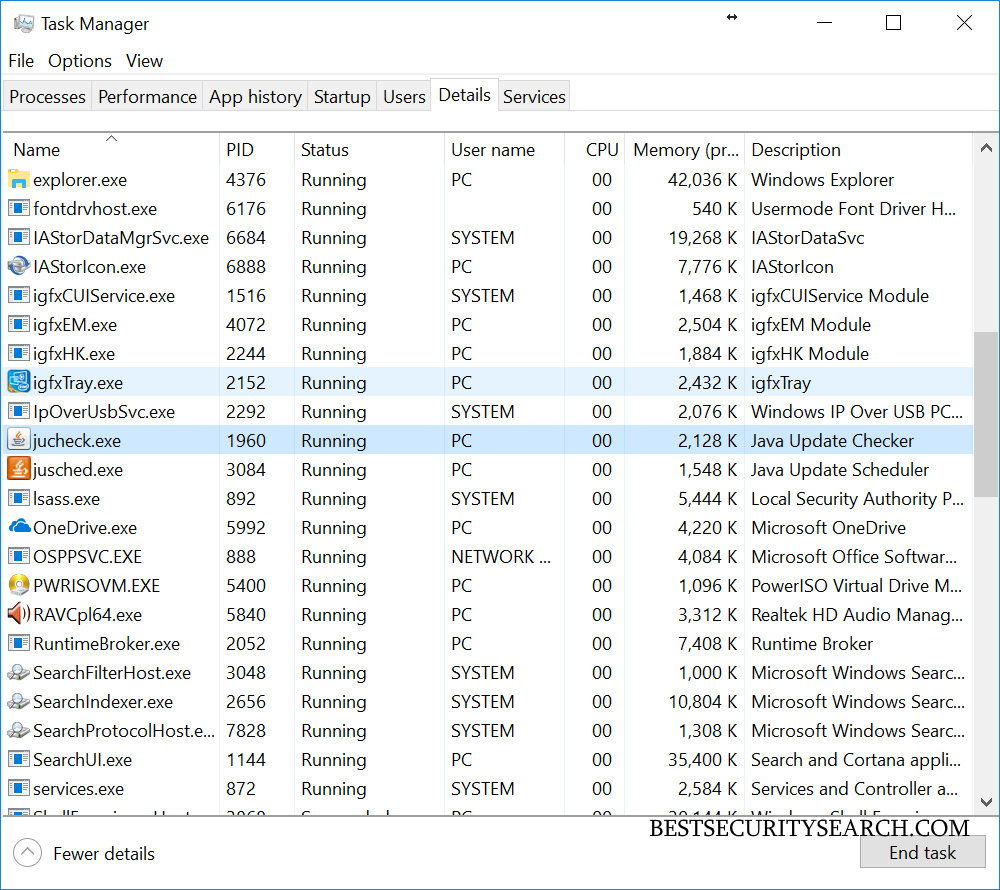
- Start The Decryptor – In most cases double clicking on the application should automatically start the decryption process. By default the decryptor is configured to target the most common sample configurations used by the hackers in the large-scale attack campaigns. In case this fails the users can specify the WannaCry ransomware PID by opening the task manager and looking for the process. To open it right click on the task bar and choose “Task Manager”. If the application opens in the minimal view click on “More details” and navigate to the “Details tab”.

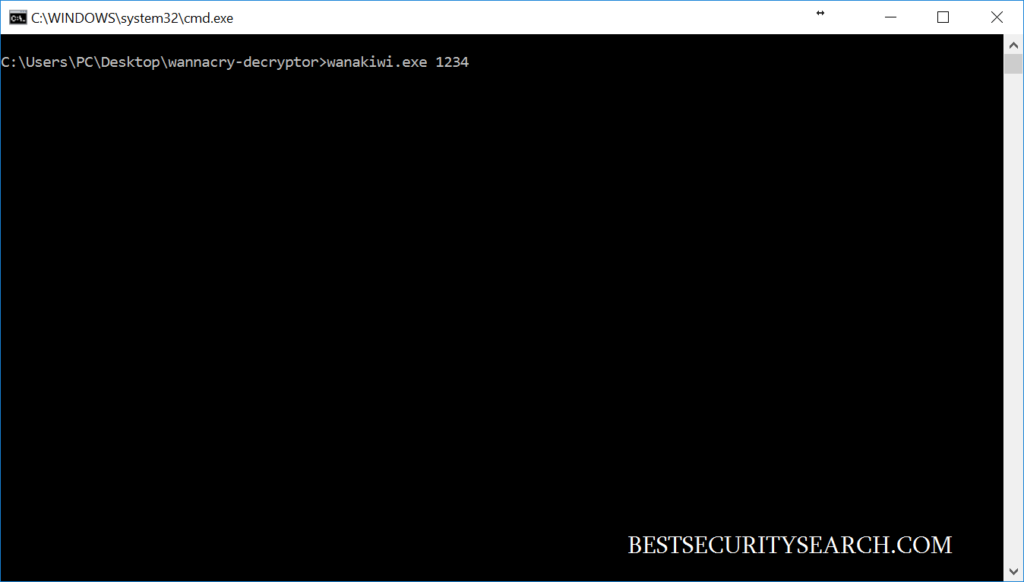
Once it is acquired hold the shift key and right click on the folder containing the decryptor and choose the “Open command window here” option. This is done by typing wanawiki.exe and the WannaCry ransomware PID .

- It is recommended that all files decrypted files are immediately copied to a backup device before the computer is shut down or rebooted, including the generated decryption key saved as a 00000000.dky file.
Refer To Our WannaCry Ransomware Removal Guides
To learn all about the menace refer to our in-depth WannaCry ransomware removal guide. It gives detailed technical information about its behavior.
We explain how users can use an easy to use and powerful anti-malware solution to remove all traces of the WannaCry ransomware, as well as alternative manual removal instructions.