The SecretSystem ransomware virus is a newly discovered malware which encrypts user data and marks all affected files with the .slvpawned extension. It extorts the sum of 500 US Dollars payable in the Bitcoin digital currency. You can remove SecretSystem ransomware virus via:
DOWNLOAD SECRETSYSTEM Virus Removal Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Once the SecretSystem ransomware virus is removed successfully, you can try to restore your files following our instructions below.
The SecretSystem Ransomware Virus Impact on an Infected PC
The identified SecretSystem virus is the newest malware that has been identified in an attack. It is also known under the name Ransomeware_Final ransomware virus.
Upon infection it follows the typical behavior associated with basic encryption type computer viruses. The SecretSystem virus immediately starts to encrypt target user data based on a predefined list. Based on the targets and the attack campaign it can be changed by the operators. We assume that the current wave processes the most popular extensions associated with music, videos, photos, databases, configuration files, archives and etc. All processed files by the SecretSystem virus are renamed with the .slvpawned extension.
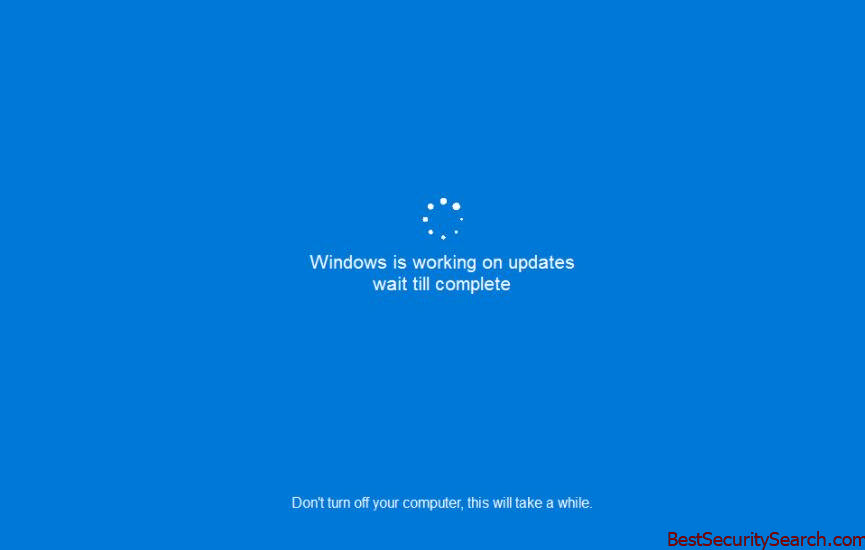
When the encryption engine has started a fake Windows update screen is shown to the victims. It is made in order to prevent the victims from noticing the attacks and attempting to remove it.
Similar Viruses: FinalRansomware Virus, SadStory Ransomware Virus, ZinoCrypt ransomware
A ransomware note is created when the encryption process is complete. It has the following contents:
All Your Files are Encrypted by SecretSystem
If you Close me you will loose all Your Files.
If you want to decrypt your files follow this simple steps:
1.) Create BitcoinWallet
2.) Buy Bitcoins worth of $500
3.) Send $500 in BitCoin to Given Address
4.) Go to http://xxxx.xxx.xxx and Enter your Personal Id
5.) You will get your Decryption Key
6.) Enter it in Given Box and Click on Decrypt
7.) Restart your Computer and Delete any encrypted file you find
Contact Me :[email protected] orfb.com/Anonymous.404.NF
From the note we can see that the hackers use a freely hosted email account and a Facebook profile for contact options. The social network profile reveals that the hacker behind the SecretSystem ransomware virus may be of Indonesian origin. The criminal extorts the victims of the virus infection for the sum of 500 US Dollars payable in the Bitcoin digital currency. Like other similar threats the SecretSystem ransomware virus creates a personalized page associated with each individual victim.
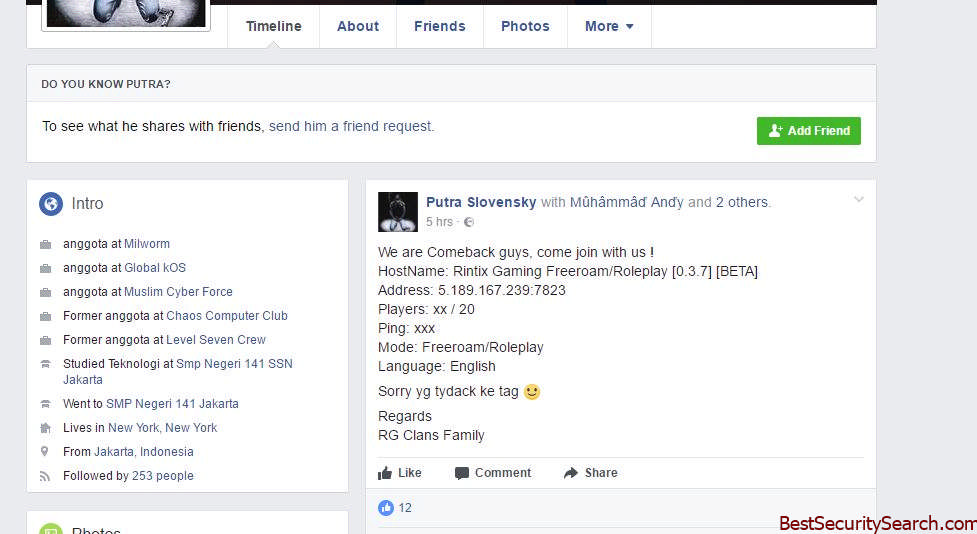
It is very likely that the unique ID associated with the SecretSystem ransomware virus has been made with extracted system information.
SecretSystem Ransomware Virus Distribution Methods
The SecretSystem virus is distributed as a single binary file called Ransomeware.exe. It can be distributed via different strategies. The most popular ines ones include the following:
- Email Spam – Hackers create coordinated email spam attacks that use all kinds of social engineering tricks. They trick the computer users into infecting themselves with the SecretSystem ransomware virus by attaching the file directly or linking it to a hacker-controlled download site. The messages pose as being sent from a well-known company or government institution.
- Infected Documents – The computer criminals create Office documents that infect the targets with the SecretSystem ransomware virus upon interaction with the built-in scripts. The malware is downloaded frm a remote hacker-controlled server and this method of deployment is significantly harder to detect by anti-virus products that use only a basic signature-based check.
- Infected Software Bundles – SecretSystem virus samples can be bundled in hacker-modified software installers.
- Hacker-controlled Download Sites – The computer criminals spread the virus binaries, infected software and other file types on hacker-controlled download sites and portals. They may even pose as official software sources. P2P networks like BitTorrent are popular among computer criminals that spread the SecretSystem ransomware virus.
- Browser Hijackers – Malicious browser extensions, also known as browser hijackers, are a possible source of SecretSystem ransomware virus infections. They modify essential settings such as the default home page, search engine and new tabs page.
Remove SecretSystem Ransomware Virus and Restore .slvpawned Encrypted Files
WARNING! Manual removal of the SecretSystem ransomware virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
SecretSystem Virus – Manual Removal Steps
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely SecretSystem Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



