The Scwerer ransomware is a new Autoit based virus which can be removed by following our complete removal guide.
Schwerer Ransomware Description
Schwerer Ransomware is a newly discovered virus strain that may possibly be of original design as no shared code with other malware families has been identified by the preliminary analysis. It features a basic encryption engine which uses the AES cipher to process the target files.
Upon infection it automatically starts the encryption engine which targets a predefined built-in list of target file type extensions. At the moment we don’t have a copy of it yet however we presume that it targets the most commonly used data: documents, photos, music, videos, configuration files, archives, databases and etc.
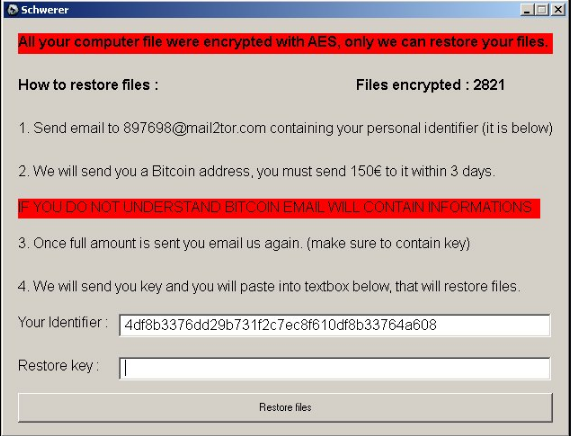
The Schwerer ransomware proceeds with the creation of a screenlocker which displays the ransom note and prevents any user interaction with the infected computer. This is done by overlaying the screen with an application frame titled “Schwerer” which shows the following message:
All your computer file were encrypted with AES, only we can restore your files.
How to restore files : *****
Files encrypted : 2821
1. Send email to [email protected] containing your personal identifier (it is below)
2. We will send you a Bitcoin address, you must send 150€ to it within 3 days.
IF YOU DO NOT UNDERSTAND BITCOIN EMAIL WILL CONTAIN INFORMATIONS
3. Once full amount is sent you email us again. (make sure to contain key)
A. We will send you key and you will paste into textbox below, that will restore files.
Your Identifier: 14df8b3376dd29b731f2c7ec8f610df8b33764a608
Restore key: *****
[Restore files]
The note contains a mixture of several important variables:
- The ransomware note filename – Used to display the unique machine ID identifier which is assigned to the computer.
- Contact Email – This field shows the hacker’s contact email. The captured samples shows that the hackers use the mail2tor email service provider which routes the messages through the TOR anonymous network.
- Ransomware Amount – The current iteration requests the sum of 150 Euro paid in Bitcoins.
- Bitcoin Delivery Address – This field shows the address to which the amount can be paid to the hackers.
The ransomware sum is listed in Euro and we assume that the operators of this threat operate from Europe. As this is a basic virus we presume that the criminals might create an upgraded version of the Schwerer Ransomware. Updated versions of this threat can contain additional functions such as the following:
- Keylogger – A keylogger found in ransomware samples can be used to monitor the actions of the users and record all input from the keyboard mouse.
- Information Harvesting – The inclusion of such modules can steal data from the victim machines at will.
- Remote Control – A Trojan component can allow remote control of the infected machines.
- Additional Payload Delivery – The Schwerer Ransomware can be used to deliver additional malware to the infected hosts.
- Botnet Recruitment – Advanced ransomware strains can recruit the victim computer into a worldwide botnet that can be utilized further by the attackers.
The analysts discovered that the virus adds a registry entry to the Windows operating system:
“HKCU\Software\Other\Schwerer” ,”complete” , “REG_SZ”
This mechanism is frequently used to enable a persistent environment. Even though the current iteration does not feature this module a future version might use this registry value to continously modify the environment and render any manual removal attempts useless. Such a state of infection modifies any changes made by the user which might interfere with the virus process. Recovery prevention is made possible by the use of several techniques including the following:
- Process Monitoring – The virus engine may include a built-in list of anti-virus processes which are automatically killed during the early stages of infection. This effectively stops their real-time agents and safely infects the computer without resistance. Specialist anti-malware engines infections like this one by using a high-quality and innovative detection engine.
- Registry Modification – To prevent recovery options the virus engine may modify key registry entries related to user or system applications.
- Windows Settings Modifications – Schwerer ransomware can include a module which can modify essential settings such as boot options to prevent administrators from recovering their computers.
The analysts discovered that the virus is writen in the AutoIt automation language. This is scripting language that is very similar to BASIC which can mean that its creator are not experienced programmers. These scripts can easily be converted into small stand-alone files which can be run on most modern versions of the Microsoft Windows operating systems.
Schwerer Ransomware Distribution
The Schwerer Ransomware can be distributed in a number of different ways. Depending on the campaign, targets and scope the hackers can use various methods.
One of the primary and most popular ways of infecting people with ransomware is the use of spam emails. They are constructed according to a template system. One of the recent trends is the use of infected office documents. They pose as files of user interest – letters, invoices, statements and etc. Once the victim opens them a prompt is displayed which asks them to enable the built-in scripts (macros). They act as payload downloaders for the Schwerer ransomware.
Another method is the infection of software installers. They are modified by the hackers to include the virus code and can take forms of both free or trial versions of the popular software including games, Windows updates, applications and utilities. They are usually distributed on hacked or hacker-controlled download sites or BitTorrent trackers where pirate content is usually found. The hackers can also opt to use malicious ad engines which both generate income for the operators and redirect the victims to dangerous hacker download sites where the Schwerer ransomware is hosted.
Browser hijackers are another source of ransomware infections. They are malicious browser extensions made for the popular web browsers – Mozilla Firefox, Google Chrome, Internet Explorer, Safari and Microsoft Edge. They change the default home page, search engine and new tabs page to point to a hacker-controlled site which distributes viruses. In addition the hijackers have the ability to extract sensitive information such as stored cookies, history, accounts and can track the users in real time. This is also one of the supply channels for email address harvest.
Direct hacker intrusion attempts are used by automated penetration testing frameworks. They attempt to find a vulnerability in installed software packages on the victims computers.
Summary of the Schwerer Ransomware
| Name |
Schwerer Ransomware |
| File Extensions |
Unknown |
| Ransom |
150 Euro in Bitcoins |
| Easy Solution |
You can skip all steps and remove Schwerer Ransomware ransomware with the help of an anti-malware tool. |
|
Manual Solution |
Schwerer Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
Schwerer Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Schwerer Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Schwerer Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore Schwerer Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



