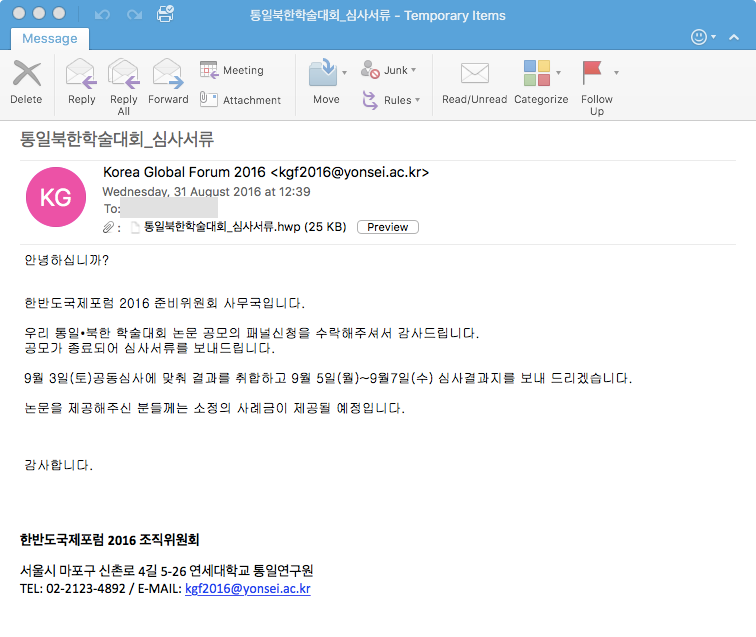
Cisco Talos experts discovered a dangerous new malware threat which is known as ROKRAT and is delivered via email spam messages.
ROKRAT Malware Discovered
Security researchers from Cisco Talos discovered a dangerous new malware named ROKRAT which target users in South Korea. It is distributed mainly through a large-scale email phishing campaign. It uses template messages that are very similar to the campaign we reported back in February. The analyzed samples were pretty interesting. One of the captured instances of the malware contained a message which praised the user for accepting an invitation to a panel related to a conference titled “Korean Reunification and North Korean Conference“. The hackers explain that the recipients must complete an attached document form. Another sample attempts to social engineer the users into interacting it it by simulating a plea for help. All detected samples so far contain attachments that attempt to compromise the host by using a known software vulnerability tracked in the CVE-2013-0808 advisory – Buffer overflow in the gldll32.dll module in EPS Viewer 3.2 and earlier allows remote attackers to execute arbitrary code via a crafted EPS file.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
ROKRAT Malware Route Of Infection
The security analysis shows that the malware has some interesting built-in features:
-
The virus does not work in execute if it is running on Windows XP or an older version of Microsoft’s operating system. The engine includes a version check module which uses the system API to retrieve the installed operating system.
-
The virus retrieves of the running processes to check if there are any running sandbox environments, virtual machines or security solutions in place.
-
The following applications and processed are supported by the engine: VMWare Tools, OllyDBG, Python Environment, File Monitor, Registry Monitor, PEiD, Process Explorer, VirtualBox, Fiddler, Portmon, Wireshark, Process Monitor, Autoruns and TCPView. If any of these processes are discovered active on the system during the infection phase the engine creates a function which starts to generate dummy HTTP traffic. This severely impacts dynamic analysis and can make system administrators unaware of the malware if they are not experienced enough to spot it. The function creates connections to often used URLs such as Amazon and Hulu.
When the first stage of infection has been complete the malware engine uses a legitimate infrastructure solution to report and receive orders. This is possible through the use of 12 hardcoded tokens via public API modules. Some of the more complex cases include complex communication processes:
-
Twitter – 7 different API tokens are included in the analyzed samples which are laid out in a set order: Consumer Key, Consumer Secret, Tolen & Token Secret. The malware engine can retrieve remote commands by checking the last message available on the hacker’s timeline. Depending on the issued command the remote client may be made to execute certain commands, move a file, delete a file, kill a process or download & execute a file from a remote location. The module allows the infected machines to tweet status messages as well which are coded in a special pattern. The sent data is assigned a random prefix that follows a 3-characters hardcoded word.
-
Yandex – The ROKRAT malware can use the Yandex Cloud platform using 4 hardcoded tokens. The used API allows the hackers to issue commands that can either download & execute files on the compromised files or download arbitrary user data. The stolen data is uploaded to a hacker-controlled cloud account.
-
MediaFire – This is an alternative to the Yandex mechanism which supports the same set of features.
Additional damage can be caused by engaging any of the Trojan features available in the analyzed samples – a sophisticated keylogger which can record keystrokes and capture screenshots on request.
Consequences Of a ROKRAT Malware Infection
The malware has been rated as extremely dangerous as it is tailored against South Korean users. The sophisticated way in which it is created and run presumes that a lot of users may be impacted. The researchers state that the virus uses a very innovative method for C&C communication. The fact that it also uses a fake network generator to conceal itself sets it apart from other similar threats.
As always we highly recommend that all users use a quality anti-malware solution to protect themselves from possible intrusion attempts, as well as to remove active infections with a few mouse clicks.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



