The security vendor ZScaler identified a currently unnamed new Android banking Trojan that operates in South Korea.
The New Banking Trojan Is Still Limited Only to South Korea
The experts from ZScaler have identified a new Android Banking Trojan that is targeting individuals in South Korea. The threat is still unnamed however it has gained notoriety as it poses as a legitimate security application.
The program poses as a version of the V3 Mobile Plus solution made by AhnLab, a South Korean company that specializes in anti-virus and other security products. The real app is a mobile transaction solution that provides real-time detection of smartphone malware.
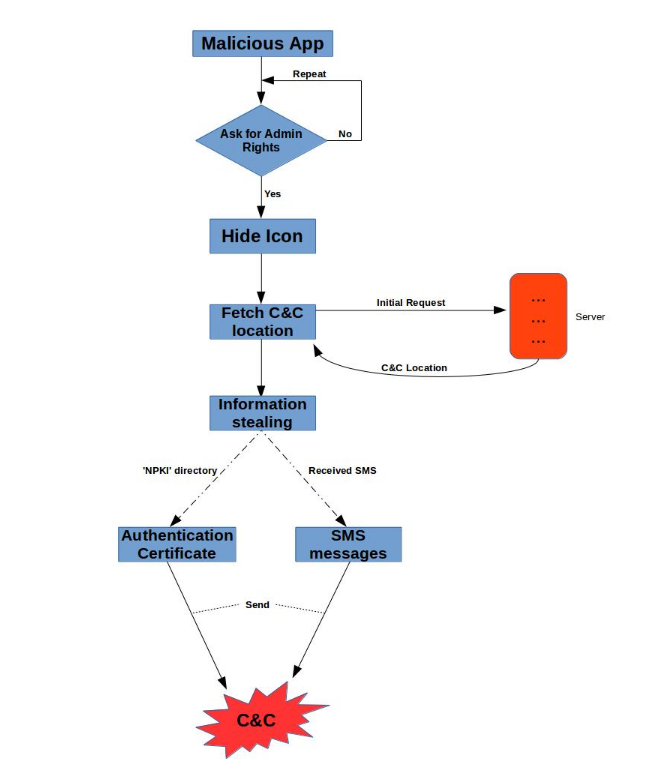
The Trojan poses as the legitimate app with the name V3 Mobile Plus and asks for administrator privileges upon launch. After claiming the necessary rights, the program hides itself which makes the victim user think that it has been removed from their device. At the same time, the app runs various services in the background. The main goal of the Trojan is to steal the victim’s SMS messages and authentication certificates used in the National public key infrastructure for the control. They are sent to the remote malicious command and control servers.
The stolen SMS messages are also stolen along with specific device parameters including the IMSI number and the phone number. The Trojan cancels the broadcast which makes the victims unaware that they have received any messages.
The current version of the malware also has a security detection function. It actively searches for the V3 Mobile Plus 2.0 or ALyac Android mobile apps and doesn’t execute if they are found on the system to avoid detection. The experts believe that new package names can be added in the future.
The application is designed to be persistent on the victim devices. However it can be removed by following these instructions:
- Boot the device into safe mode according to the manufacturer instructions
- Remove the administrator privileges. Navigate to Settings –> Device Administrator, choose the malicious app and tap on deactivate
- Navigate to the Settings –> Apps menu and uninstall the malware
For more information you can refer to the full analysis.