Serpico ransomware is a new variant of DetoxCrypto cryptovirus. It infiltrates the system, executes itself and demands ransom fee from the victims. It doesn’t use any particular extension to indicate that a file is encrypted unlike the typical practice used by almost all ransomware viruses. Part of its infection is to drop a ransom note to the victim’s desktop written in Serbsko-Croatian. The purpose of such kind of infections is a ransom demand. In case of infection, this article will help you to deal with the threat and stay secured in future.
| Name |
Serpico Ransomware |
| File Extensions |
No changes are made |
| Ransom |
50 Euro |
| Solution #1 |
Serpico Ransomware can be removed easily with the help of an anti-malware tool, a program that will clean your computer from the virus, remove any additional cyber-security threats, and protect you in the future. |
|
Solution #2 |
Serpico Ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Serpico ransomware is distributed mainly through spam email campaigns that link or contain infected binary files. |
Stages of Serpico Ransomware Infection
This new variant doesn’t present as counterfeit Pokemon Go application as some of previous DetoxCrypto’s versions do. The Serpico cryptovirus may be distributed to criminals in the Dark Web.The threat has been discovered by security researcher S!Ri back in August.
The new variant of DetoxCrypto has been named Serpico because of the folder’s name where it stores its associated files. However, in the ransom note the ransomware entitled itself CryptoLocker. Here is a list of files and folders associated with Serpico ransomware:
- C:\Users\UserName\the Serpico\bg.jpg
- C:\Users\UserName\the Serpico\key.pkm
- C:\Users\UserName\the Serpico\the Serpico.exe
- C:\Users\UserName\the Serpico\sound.wav
- C:\Users\UserName\the Serpico\total.pkm
- C:\Users\UserName\Desktop\MotoxUnlocker.exe
Following infiltration, Serpico ransomware uses an EXE file named Serpico.exe or its copy called MotoxUnlocker.exe that launches the attack. However, the name of the executable files may be modified to appear as a legitimate Windows process like TaskManager.exe. Once the malicious executable file is running the encryption stage starts. Serpico targets 53 data types which are:
→ .3ds, .7z, .acbl, .all, .backup, .bak, .bmp, .bz2, .cab, .cdr, .cer, .cpr, .crt, .cs, .csv, .dat, .db, .dbf, .der, .doc, .docx, .dwg, .eps, .gif, .ibd, .ibz, .iso, .jpeg, .jpg, .mdb, .mdf, .myd, .pdf, .php, .png, .ppt, .pptx, .psb, .pst, .rar, .rns, .s3db, .sql, .sqlite, .sqlitedb, .tar, .txt, .xls, .xlsx, .xlt, .xltx, .xml, .zip.
Serpico encodes the data utilizing strong AES encryption algorithm. Encrypted files don’t have appended or changed extensions, they retain their original names.
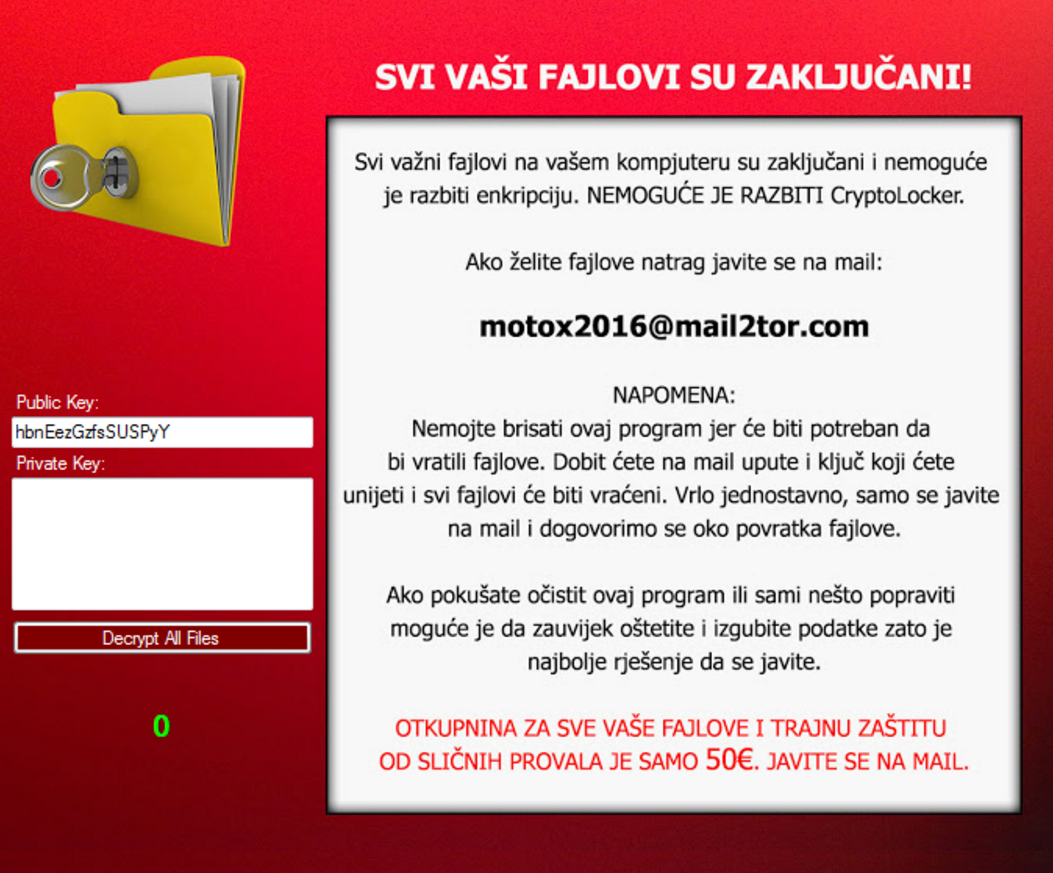
One of the installed files by Serpico is an image file used to replace the computer’s wallpaper image with a ransom note. The text of the note reads:
“SVI VAŠI FAJLOVI SU ZAKUUČANI!
Svi važni fajlovi na vašem kompjuteru su zaključani i nemoguće je razbiti enkripciju. NEMOGUĆE JE RAZBITI CryptoLocker.
Ako želite fajlove natrag javite se na mail:
[email protected]
NAPOMENA:
Nemojte brisati ovaj program jer će biti potreban da bi vratili fajlove. Dobit ćete na mail upute i ključ koji ćete unijeti i svi fajlovi će biti vraćeni. Vrlo jednostavno, samo se javite na mail i dogovorimo se oko povratka fajlove.
Ako pokušate očistit ovaj program ili sami nešto popraviti moguće je da zauvijek oštetite i izgubite podatke zato je najbolje rješenje da se javite.
OTKUPNINA ZA SVE VAŠE FAJLOVE I TRAJNU ZAŠTITU OD SLIČNIH PROVALA JE SAMO 50€. JAVITE SE NA MAIL.”
The attackers demand a ransom of 50 Euros in exchange for a key that will restore the data. The best advice we can give to all victims of Serpico ransomware is to avert the contact with the malicious intenders.
Distribution Techniques of Serpico Ransomware
Serpico ransomware is likely to be spreading with spam emails. The sender may pose as various legitimate sources. The text may be trying to convince you that the information is valuable and should be opened immediately. The threat itself may be hidden within an attachment or in a link to compromised website provided in the email message. Beware of file attachments that contain WSF files as it is a new distribution practice used by crooks. This technique allows them to obfuscate the malicious payloads of the threat.
Fake update notifications are also may be also used for the ransomware spreading. Sometimes the links that lead to compromised websites and cause Serpico ransomware infection may be posted in messages or posts on social media sites like Facebook.
What to Do to Prevent Infection with Serpico Ransomware
Keep your security tools up to date. Analyses show that many anti-malware and anti-virus software detect and block the infection. In case you don’t use any anti-malware tool consider downloading any because the risk to fall into the trap of the malicious intenders is high.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How to Remove Serpico Ransomware and Decrypt Locked Files
Serpico ransomware virus is a grave threat for your computer. It endangers the regular performance of the operating system and exposes all your data and privacy to solid risks. An instant removal of all installed files and created objects in the registry by the malware is the best step for your security. Don’t let cyber criminals harass you and better avoid payment of the ransom. All of your encoded files could be decrypted for free after the removal of the threat. Victims of Serpico ransomware can use the free Serpico decrypter released by the security researcher Michael Gillespie. But first, make sure that all malicious files are removed. Follow the removal guide, get rid completely of Serpico ransomware and download the decryption tool to recover your locked files.
Serpico Ransomware Removal
For a faster solution, you can run a scan with an advanced malware removal tool and delete Serpico ransomware completely with a few mouse clicks.
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Serpico Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
-
1) Use present backups
2) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



