Symantec announced some observations from the past three months. They have monitored a major increase in the number of email-based attacks that use malicious Windows Script File (WSF) attachments.
The new tactic is implemented mainly by ransomware groups. This is not a surprise as many users are suspicious of emails from unknown sources that contain PDF, executables or Microsoft Office documents and avoid opening these files. So the malware attackers are always trying to trick users and their AV software by using new tactics. The security researchers have recently blocked series of new email campaigns that distribute Locky ransomware via malicious WSF files. The company’s analysis show that the malicious WSF files come packed into .ZIP archives. The emails impersonate deliveries of travel agencies, compliant letters, messages from major airlines, etc. An eventual run of the WSF file leads to installation of Locky or other malware on the victim’s computer.
This is not the first time when crooks shift their distribution plan as in August we have reported how they started using DLL files for the Locky’s malicious scheme.
But the recent email attack campaigns that use WSF attachments are not only observed for Locky distributions. The number of blocked emails containing malicious WSF attachments increased from 22 000 in June to more than 2.2 million in September.
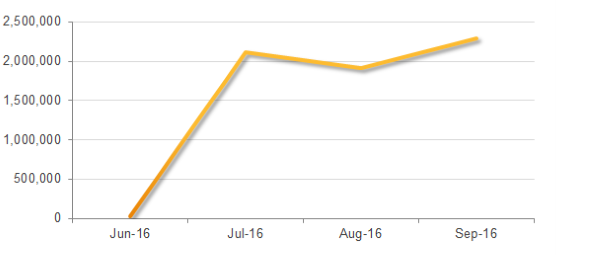
Image Source: Symantec, “Number of blocked emails containing malicious WSF attachments by month”
Why Windows Script Host (WSH) Files?
Researchers explain:
“WSF files are designed to allow a mix of scripting languages within a single file, and are opened and run by the Windows Script Host (WSH).”
It is highly possible that the users don’t set their email services to automatically block files with a .wsf extension so they can be executed as an executable file. Furthermore, the new practice could mislead the AV software if the vendors have not improved their defenses against certain malicious file types. Thus the attack slip through defenses and the infection starts without any alert that something wrong is going to happen once you open the .wsf file.
Yet another reason for choosing WSF files could be that this file type is rarely used by most of the users. So they are more curious to see what will be displayed after they open the file and don’t even expect what could be the risk once the file is running.
In Conclusion..
Note from the researchers:
“In a constantly shifting threat landscape, organizations need to remain vigilant and aware that threats can come from new and unanticipated sources.”



