The .MOLE03 ransomware virus is the third strain of the devastating ransomware Mole. The threat encrypts particular files making them not working and demands a ransom to decrypt them. At the end of infection, a ransom note appears on the PC screen while all corrupted files have the malicious file extension .MOLE03 appended to their names. The instructions in this article aim to help all infected users to remove the ransomware and recover .MOLE03 files without paying the ransom.
Manual Removal Guide
Recover .MOLE03 Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How Does .MOLE03 Ransomware Virus Infect
The .MOLE03 ransomware virus samples can be delivered via different techniques. One of the most common strategies is the creation and coordination of crafted spam email campaigns that feature social engineering tricks. The aim of hackers is to trick victims into infecting themselves with the .MOLE03 ransomware virus by opening file attachments or links inserted in the body content. The messages pose as being sent from legitimate companies or government institutions and are usually done by adding graphics and text that resemble the real companies.
The .MOLE03 virus payload can also be hosted on hacker-controlled or hacked download sites that may pretend to be distributing legitimate sources. Based on the infection plan the the .MOLE03 ransomware virus code can be bundled in software installers or documents.
Other methods include direct hacker attacks, browser hijacker deployment, and automated software vulnerability attacks.
Infection Flow of .MOLE03 Ransomware Virus
The .MOLE03 ransomware virus derives from the Mole ransomware family and appears to be third on a roll after .MOLE and Mole00-02 ransomware.
It drops its malicious executable file on the system, and once it is running on it, the ransomware performs a sequence of malicious system and data modifications. Thus it may drop or create additional malicious files and hide some of them in essential Windows folders like %Temp%, %AppData%, %UserProfile% and %Roaming%. The .MOLE03 ransomware virus can establish an online connection with website or host controlled by cyber criminals so they can receive more details about the system and the decryption key which is generated during the encryption process.
The encryption is realized via RSA 2048 and AES 128 cipher algorithms. It is applied to each file that has one of the file extensions predefined in .MOLE03 ransomware target data list. As its predecessors this Mole variant is believed to have the same list of target file extensions in its code which are:
.0 .1CD .1PA .1ST .2BP .36 .3DM .3DS .3FR .3GP .411 .4DB .4DL .4MP .73I .7Z
.8XI .A3D .AB4 .ABM .ABS .ABW .ACH .ACT .ADB .ADN .ADP .ADS .AES .AF2 .AF3 .AFS
.AFT .AFX .AGP .AHD .AI .AIC .AIF .AIM .AIT .AL .ALF .ANI .ANS .APD .APJ .APK
.APM .APS .APT .APX .ARC .ART .ARW .ASC .ASE .ASF .ASK .ASM .ASP .ASW .ASX .ASY
.ATY .AVI .AWP .AWT .AWW .AZZ .BAK .BAR .BAT .BAY .BBS .BC6 .BC7 .BD .BDB .BDP
.BDR .BGT .BIB .BIG .BIK .BKF .BKP .BM2 .BMP .BMX .BMZ .BNA .BND .BOC .BOK .BPW
.BRD .BRK .BRN .BRT .BSA .BSS .BTD .BTI .BTR .BYU .BZ2 .C .C4 .C4D .CAL .CAN
.CAS .CD5 .CDB .CDC .CDF .CDG .CDR .CDT .CDX .CE1 .CE2 .CER .CF .CFG .CFP .CFR
.CFU .CGM .CIN .CIT .CKP .CLS .CMA .CMD .CMT .CMX .CNM .CNT .CNV .CPC .CPD .CPG
.CPI .CPP .CPS .CPT .CPX .CR2 .CRD .CRT .CRW .CS .CSH .CSL .CSR .CSS .CSV .CSY
.CT .CV5 .CVG .CVI .CVS .CVX .CWT .CXF .CYI .DAC .DAD .DAF .DAS .DAT .DB .DB0
.DB2 .DB3 .DBA .DBC .DBF .DBK .DBR .DBS .DBT .DBV .DBX .DC2 .DCA .DCB .DCH .DCR
.DCS .DCT .DCX .DDD .DDL .DDS .DED .DER .DES .DF1 .DGC .DGN .DGS .DGT .DHS .DIB
.DIF .DIP .DIZ .DJV .DM3 .DMI .DMO .DMP .DNC .DNE .DNG .DOC .DOT .DP1 .DPP .DPX
.DQY .DRF .DRW .DRZ .DSK .DSN .DSV .DT .DT2 .DTA .DTD .DTW .DVI .DVL .DWG .DX
.DXB .DXF .DXG .DXL .EBD .ECO .ECW .ECX .EDB .EFD .EGC .EIO .EIP .EIT .EMD .EMF
.EML .EP .EPF .EPK .EPP .EPS .EQL .ERF .ERR .ESM .ETF .ETX .EUC .EXF .EXR .FAL
.FAQ .FAX .FB2 .FB3 .FBL .FBX .FCD .FCF .FDB .FDF .FDR .FDS .FDT .FDX .FES .FF
.FFD .FFF .FFT .FH .FH3 .FH4 .FH5 .FH6 .FH7 .FH8 .FHD .FIC .FID .FIF .FIG .FIL
.FIM .FLA .FLC .FLI .FLR .FLV .FM .FM5 .FMP .FMV .FOL .FOS .FP3 .FP4 .FP5 .FP7
.FPK .FPT .FPX .FRM .FRT .FSH .FT7 .FT8 .FT9 .FTN .FX0 .FX1 .FXC .FXG .FXR .FZB
.FZV .G3 .GDB .GEM .GEO .GFB .GGR .GHO .GIF .GIH .GIM .GIO .GPD .GPG .GPN .GRO
.GRS .GRW .GRY .GSD .GTP .GV .GWI .GZ .H .HBK .HDB .HDP .HDR .HHT .HIS .HKX
.HPG .HPI .HPL .HPP .HS .HTC .HWP .HZ .I3D .IB .IBD .ICN .IDC .IDX .IGT .IGX
.IHX .IIF .IIL .IIQ .IMD .INK .INT .IPF .IPX .ITL .ITM .ITW .IWD .IWI .J .J2C
.J2K .JAS .JB2 .JBR .JIA .JIS .JNG .JOE .JP1 .JP2 .JPE .JPG .JPS .JPX .JS .JTF
.JTX .JWL .JXR .K2P .KDB .KDC .KDI .KDK .KES .KEY .KF .KIC .KLG .KNT .KON .KPG
.KWD .LAY .LBF .LBM .LBT .LGB .LGC .LIS .LIT .LJP .LMK .LNT .LOG .LP2 .LRC .LRF
.LST .LTR .LTX .LUA .LUE .LUF .LVL .LWO .LWP .LWS .LYT .LYX .M .M2 .M3D .M3U
.M4A .M4V .MA .MAC .MAF .MAM .MAN .MAP .MAQ .MAR .MAT .MAW .MAX .MB .MBM .MCL
.MDB .MDC .MDE .MDF .MDN .MDT .ME .MEF .MFT .MFW .MIN .MKV .MLX .MML .MMW .MNG
.MNR .MNT .MOS .MOV .MP3 .MP4 .MPF .MPG .MPO .MPP .MRG .MRW .MSG .MSO .MT9 .MTE
.MUD .MWB .MWP .MX0 .MXL .MYD .MYI .MYL .NCF .NCR .NCT .ND .NDD .NDF .NEF .NFO
.NJX .NK2 .NLM .NOW .NRW .NS2 .NS3 .NS4 .NSD .NSF .NSG .NSH .NTL .NV2 .NWB .NX1
.NX2 .NYF .NZB .OBJ .OC3 .OC4 .OC5 .OCE .OCI .OCR .ODB .ODC .ODF .ODG .ODM .ODO
.ODP .ODS .ODT .OFL .OFT .OIL .OMF .ONE .OQY .ORA .ORF .ORT .ORX .OTA .OTG .OTH
.OTI .OTP .OTS .OTT .OVP .OVR .OWC .OWG .OYX .OZB .OZJ .OZT .P12 .P7B .P7C .P7S
.P96 .P97 .PAK .PAL .PAN .PAP .PAQ .PAS .PAT .PBM .PBO .PC1 .PC2 .PC3 .PCD .PCS
.PCT .PCX .PDB .PDD .PDF .PDM .PDN .PE4 .PEF .PEM .PFD .PFF .PFI .PFS .PFV .PFX
.PGF .PGM .PHM .PHP .PI1 .PI2 .PI3 .PIC .PIP .PIX .PJT .PL .PLC .PLT .PM .PMG
.PNG .PNI .PNM .PNZ .POP .POT .PP4 .PP5 .PPM .PPS .PPT .PRF .PRT .PRW .PS .PSD
.PSE .PSK .PSP .PST .PSW .PTG .PTH .PTX .PU .PUB .PUZ .PVJ .PVM .PVR .PWA .PWI
.PWR .PX .PXR .PY .PZ3 .PZA .PZP .PZS .QBA .QBI .QBO .QBP .QBR .QBT .QBW .QBY
.RB .RM .RNG .RPD .RPF .RPT .RRI .RS .RSB .RSD .RSR .RST .RT .RTD .RTF .RTP
.RTX .RUN .RW2 .RWL .RWZ .RZK .RZN .S3M .SAF .SAI .SAM .SAY .SB .SBF .SCC .SCH
.SCI .SCM .SCT .SCV .SCW .SD0 .SDA .SDB .SDF .SDM .SDW .SEP .SET .SFC .SFW .SGM
.SID .SIE .SIG .SIS .SK1 .SK2 .SKM .SLA .SLD .SLK .SLM .SLS .SMF .SMS .SNP .SNX
.SOB .SPA .SPE .SPH .SPJ .SPP .SPQ .SPR .SQB .SQL .SR2 .SRF .SRT .SRW .SSA .SSK
.ST .ST4 .ST5 .ST6 .ST7 .ST8 .STC .STD .STE .STI .STM .STN .STP .STR .STW .STX
.STY .SUB .SUM .SVA .SVF .SVG .SWF .SXC .SXD .SXG .SXI .SXM .SXW .T12 .T13 .T2B
.TAB .TAR .TAX .TB0 .TBN .TCX .TDF .TDT .TE .TEX .TFC .TG4 .TGA .TGZ .THM .THP
.TIF .TJP .TLB .TLC .TM .TM2 .TMD .TMP .TMV .TMX .TN .TNE .TOR .TPC .TPI .TRM
.TVJ .TXT .U3D .U3I .UDB .UFO .UFR .UGA .UNX .UOF .UOP .UOT .UPD .UPK .USR .V12
.V30 .VBR .VBS .VCF .VCT .VDA .VDB .VDF .VEC .VFF .VML .VNT .VOB .VPD .VPE .VPK
.VRP .VSD .VSM .VST .VSX .VTF .VTX .VUE .VW .W3X .WAV .WB1 .WB2 .WBC .WBD .WBK
.WBM .WBZ .WCF .WDB .WDP .WGZ .WKS .WLL .WMA .WMF .WMO .WMV .WN .WP .WP4 .WP5
.WP6 .WP7 .WPA .WPB .WPD .WPE .WPG .WPL .WPS .WPT .WPW .WRI .WSC .WSD .WSH .WTX
.WVL .X .X11 .X3D .X3F .XAR .XDB .XDL .XF .XLA .XLB .XLC .XLD .XLF .XLL .XLM
.XLR .XLS .XLT .XLW .XML .XPM .XPP .XPS .XSN .XWP .XXX .XY3 .XYP .XYW .Y .YAL
.YBK .YML .YSP .YUV .Z3D .ZDB .ZDC .ZIF .ZIP .ZW
The .MOLE03 ransomware virus name comes from the malicious extension of the same name .MOLE03 that renames each encrypted file. Once the ransomware transforms the original code of all target files they become unable to be open with no software except the ransomware decryptor. For the purpose users will need the unique private decryption key which is possessed by hackers. Unfortunately, they demand 1.0 bitcoins ransom for the key which is an insane price as 1 BTC is currently 2758.70 US Dollar with rising trend.
Also .MOLE03 crypto virus drops a specially crafted file that contains ransom message from hackers to infected users. The file is named _HELP_INSTRUCTION.txt and is believed that the ransomware creates new values in Windows Registry to set the automatic ransom note appearance at the end of infection. All that is reads is:
!_! INFORAMTIONS !_!
All of your files are encrypted with RSA_2048 and AES_128 ciphers.
More information about the RSA and AES can be found here:
URL1: https://en.wikipedia.org/wiki/RSA_numbers
URL2: https://en.wikipedia.org/wiki/Advanced_Encryption_StandardDecrypting your files is only possible with
he private key and decrypts program, which is on our secret server.Follow these steps:
1. Download and install Tor Browsers: https://www.torproject.org/download/download-easy.html
2. After a successful installation, run the browser and wait for initialization.
3. Type in the address bar:
URL1: http://supportxxgbefd7c.onion/
URL2: http://supportjy2xvvdmx.onion/
4. Follow the instructions on the site.
!_! Your DECRYPT-ID: XXXXXXXX-XXXX-XXX-XXXXXX-XXXXXXXXXXXXX !_!
Below you can see the ransomware payment page mentioned in the ransom note. Iy is hosted on the TOR Network:
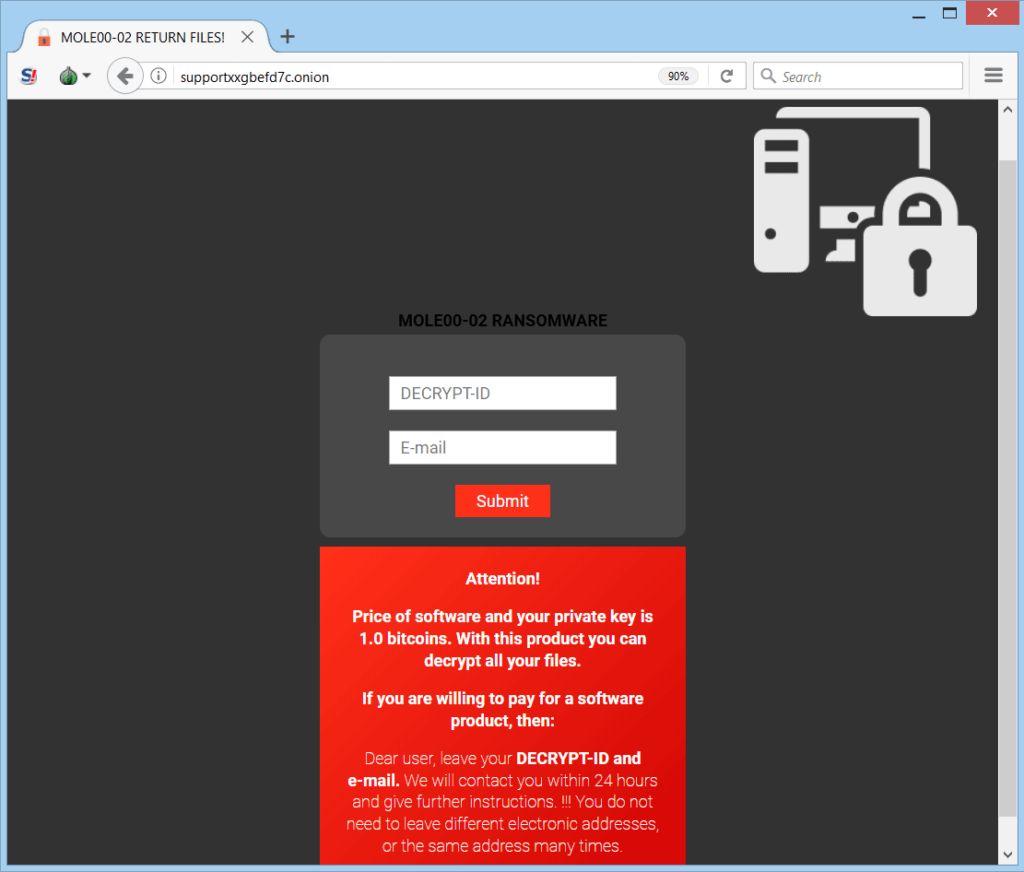
Remove .MOLE03 Ransomware Virus and Restore Encrypted Files
WARNING! Manual removal of .MOLE03 ransomware virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
.MOLE03 Virus File – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
-
– Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
-
– Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover .Mole Files
WARNING! All files and objects associated with .MOLE03 ransomware virus should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD .MOLE03 Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
UPDATE: Security researchers that are part of the “No More Ransom” project have updated their decryption tool list with a Mole Decryptor. The thorough reverse-engineering process of Mole ransomware samples performed by specialists at CERT Polska team “turned out to be a good idea”, they said. Now victims of Mole ransomware virus can retrieve the encrypted data without having to pay the criminals. Find out how to restore .mole files by visiting the No More Ransom page with decryption tools.
In case that some files remain corrupted after the decryption process you can try alternative data recovery solutions.
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
-
– Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



