An infection with the dangerous FVD Speed Dial browser hijacker leads to serious security issues. Victims can restore and protect their computers by following our complete removal guide..
Remove FVD Speed Dial Browser Hijacker and Restore PC
Manual Removal Guide
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Distribution of FVD Speed Dial Browser Hijacker
The FVD Speed Dial browser hijacker is a new threat which is being distributed at computer users worldwide. The operators behind the dangerous instance have been found to use different channels and means to infect as many users as possible.
The primary methods however rely on browser plugins that are disguised as legitimate services that offer numerous advantages to those that have installed the service. The main page associated with the FVD Speed Dial redirect lists that ready-made versions are available for the following browsers and platforms: Mozilla Firefox, Opera, Google Chrome, Android, iOS and Microsoft Edge. The security analysts note that this hijacker is different that the majority of contenders as the hacker operators have created specialist versions that are compatible with the two most popular mobile platforms as well ‒ Android and iOS.
The malicious FVD Speed Dial browser hijacker relies heavily on a well-directed marketing campaign. The operators have utilized complex landing pages, elaborate descriptions and the posting of (possibly fake) comments about the offered plugins.
Other techniques that can be utilized include email messages that feature social engineering tricks. Their goal is to make the users infect themselves by blackmailing or confusing them to install the quoted service. Depending on the configuration the following methods can be used:
- File Attachments ‒ The criminals can directly embed the FVD Speed Dial browser hijacker into the messages sent via the emails. The hackers utilize different social engineering tricks to make the victims infect themselves with the files which are usually disguised as legitimate executables files or documents of user interest.
- Hyperlinks ‒ Links to the FVD Speed Dial browser hijacker strains can be inserted in the body contents of the emails.
- Infected Documents ‒ They are linked or directly attached to the messages. Depending on the current configuration the FVD Speed Dial browser hijacker code may be placed in presentations, rich text documents or spreadsheets. When they are opened a notification prompt asks the users if they want to run the built-in macros (scripts). If this is done the infection follows.
It is possible to acquire strains of the virus by falling for hacker-controlled download sites or portals that impersonate legitimate sites. They usually distributed infected software installers which include the malware code in themselves. One of the primary strategies that the operators use is a well-designed landing page which lists that the browser extension is an useful plugin suited for organizing, syncing and storing bookmarks to popular sites.
Impact of FVD Speed Dial Browser Hijacker
The FVD Speed Dial browser hijacker upon installation changes important settings of the supported web browsers. The code changes the default home page, search engine and new tabs page to another site located at my[dot]yoursearch[dot]me.
When the user are relocated to it serious concerns concerning their privacy and security are raised. The home page lists the privacy policy and terms of conditions which signal a lot of problems. One of the most important issues related to this instance is the fact that upon infection with it a wide variety of data is extracted and sent automatically to the operators. This includes the following entries:
- FVD Speed Dial structure
- FVD Speed Dial groups
- FVD Speed Dial dials
- Screenshots of all dials
As a consequence the plugin has access to all activities made by the users. The fact that the browser plugin is able to take screenshots of the compromised browsers at all times means that the users need to remove the malware as soon as it is installed. Consequent use of it can have serious privacy concerns. When the users register on the service they also agree that the site will send them spam messages.
Another important aspect of the FVD Speed Dial browser hijacker is its inclusion of several features which make heavy use of the victim’s personal data ‒ the so-called in-app ads. They are described in the privacy policy as the following:
- Quick Preview widget ‒ For some websites (like Amazon for example), Quick Preview widget shows additional information, such as product details and its price, if a link to Amazon is present. In some cases (Amazon can still be used as an example), an affiliate ID – couponpartnerfvd or param_fvd-20 – would be added to the link when getting transferred to the site. The link on speed-dials still remains unchanged, just the way the user created it.
- Default dials ‒ When the app is installed, a few default speed dials are added. Some of those (for instance, Amazon, Booking etc.) would contain the affiliate ID in the link. Default speed dials are in no way different from regular ones, so users can delete or change them without the efficiency of the app affected in any way.
The site itself is designed to appear like a legitimate search engine page, imitating famous companies like Google and Yahoo. It features three main search options (Web, Images, Videos and Maps). Users should know that every query they send is being tracked. All behavior is recorded and the patterns are stored on a central server which collects data from all linked sites. The shown search results should not be trusted as they display sponsored sites which may not represent the content that is being seeked by the users.
Remove FVD Speed Dial Browser Hijacker and Restore PC
WARNING! Manual removal of the FVD Speed Dial browser hijacker requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
FVD Speed Dial Browser Hijacker – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Remove FVD Speed Dial from Windows
Here’s a way to remove the program. This method will work regardless if you’re on Windows 10, 8, 7, Vista or XP. Simply selecting the program and pressing delete won’t work, as it’ll leave a lot of small files. That’s bad because these leftovers can linger on and cause all sorts of problems. The best way to delete a program is to uninstall it. Here’s how you can do that:
1. Hold the “Windows” button (It’s between CTRL and Alt on most keyboards) and press “R”. You’ll see a pop-up window.
2. In the textbox, type “appwiz.cpl”, then press“ Enter ”.
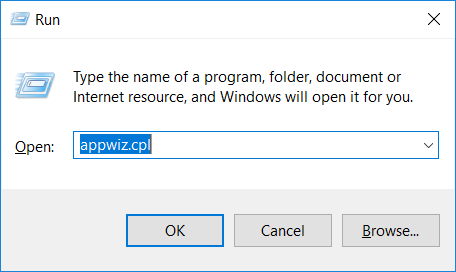
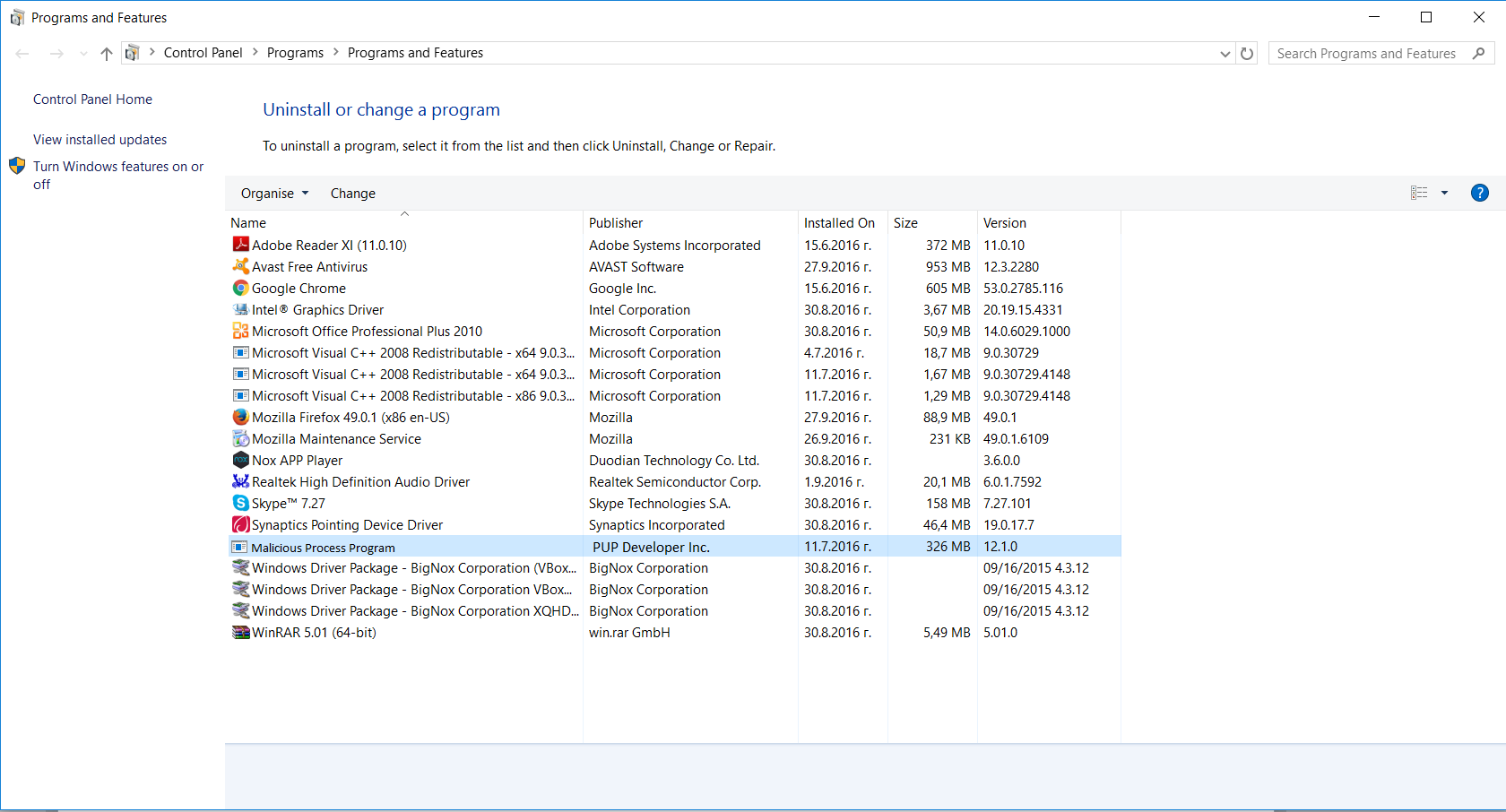
3. The “Programs and features” menu should now appear. It’s a list of all the programs installed on the PC. Here you can find the program, select it, and press “Uninstall“.
Remove FVD Speed Dial Virus From Your Browser
Before resetting your browser’s settings, you should know that this action will wipe out all your recorded usernames, passwords, and other types of data. Make sure to save them in some way.
-
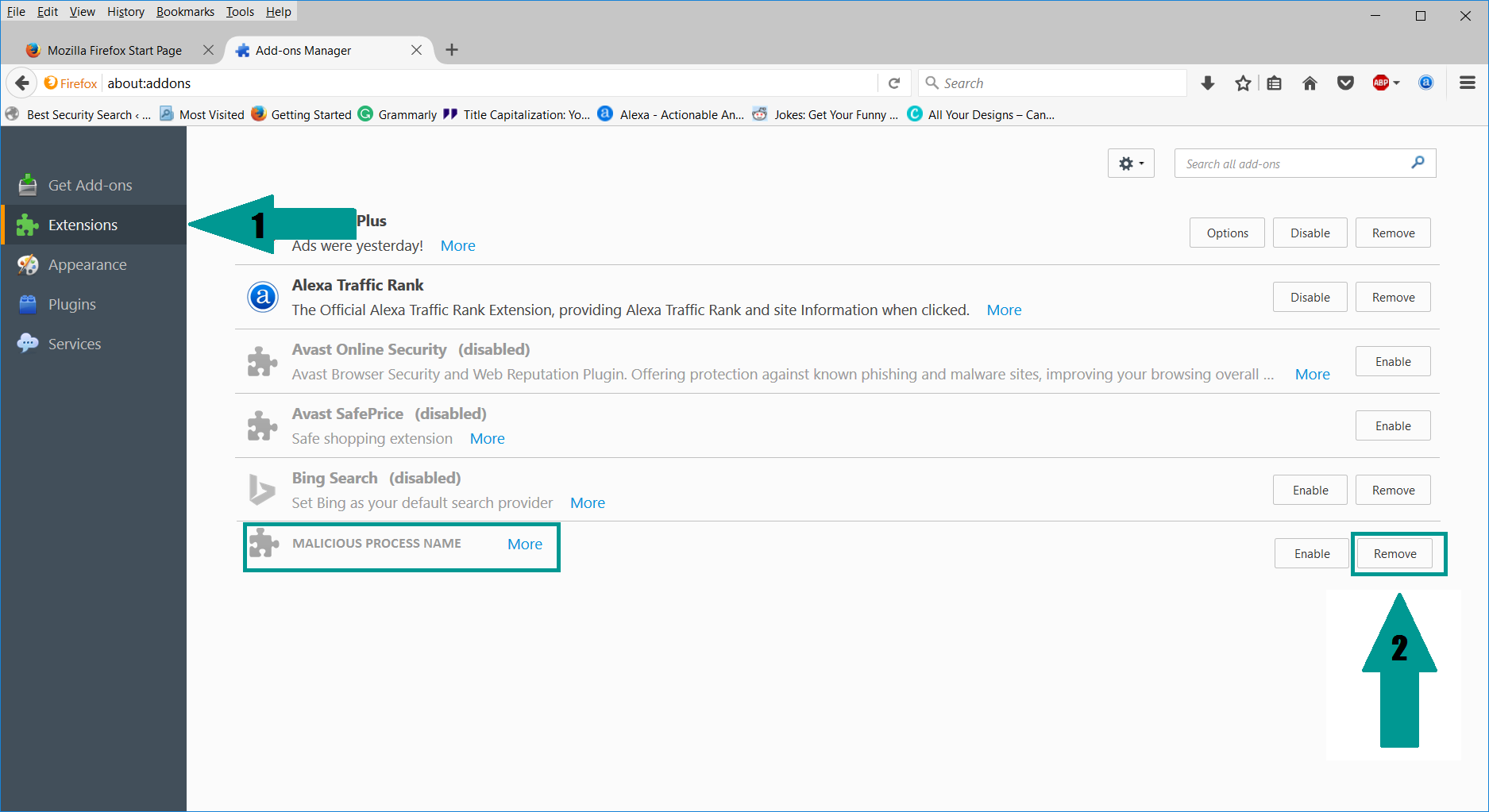
1. Start Mozilla Firefox. In the upper right corner, click on the Open menu icon and select “Add-ons“.

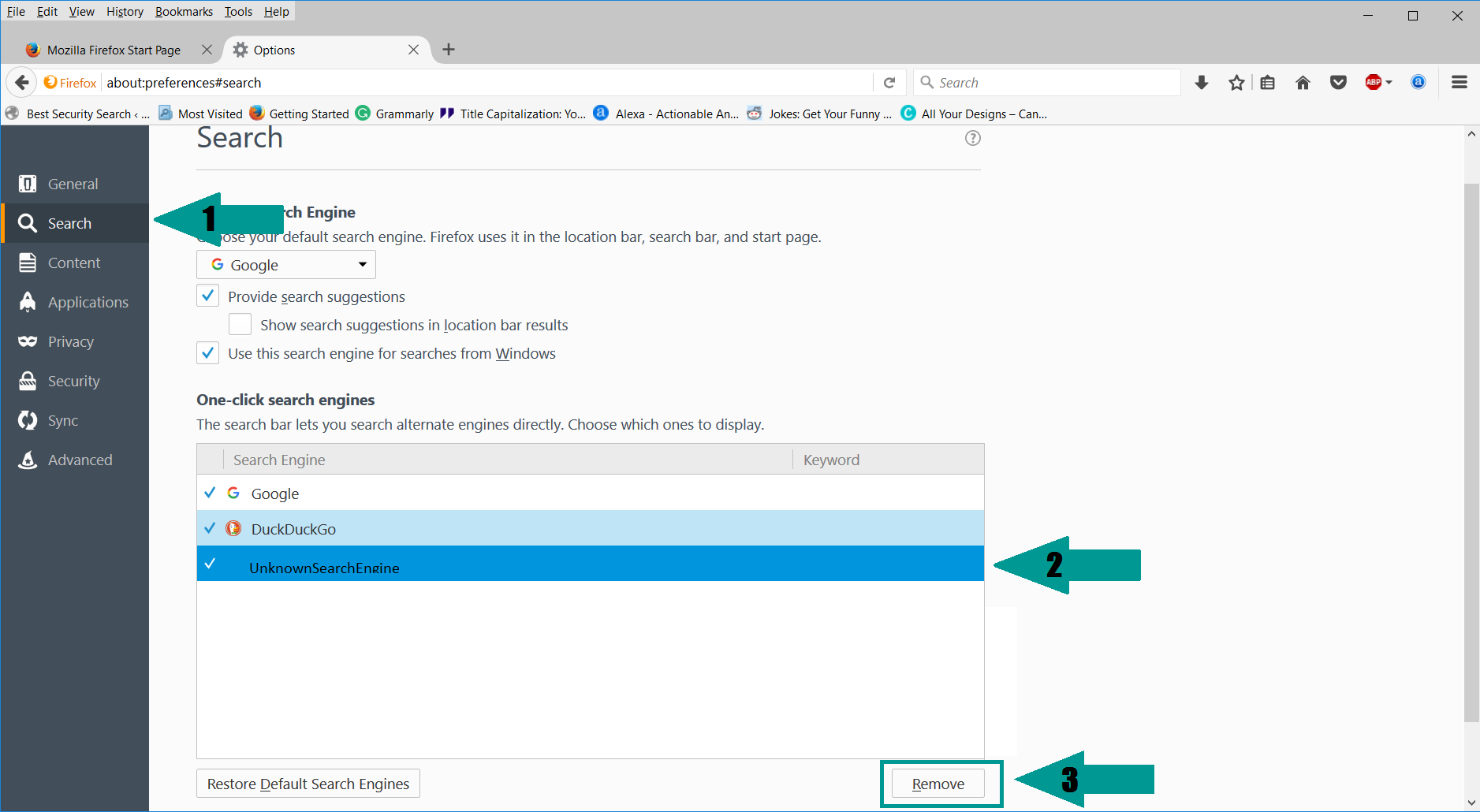
2. Inside the Add-ons Manager select “Extensions“. Search the list of extensions for suspicious entries. If you find any, select them and click “Remove“.
3. Click again on the Open menu icon, then click “Options“.

4. In the Options window, under “General” tab, click “Restore to Default“.
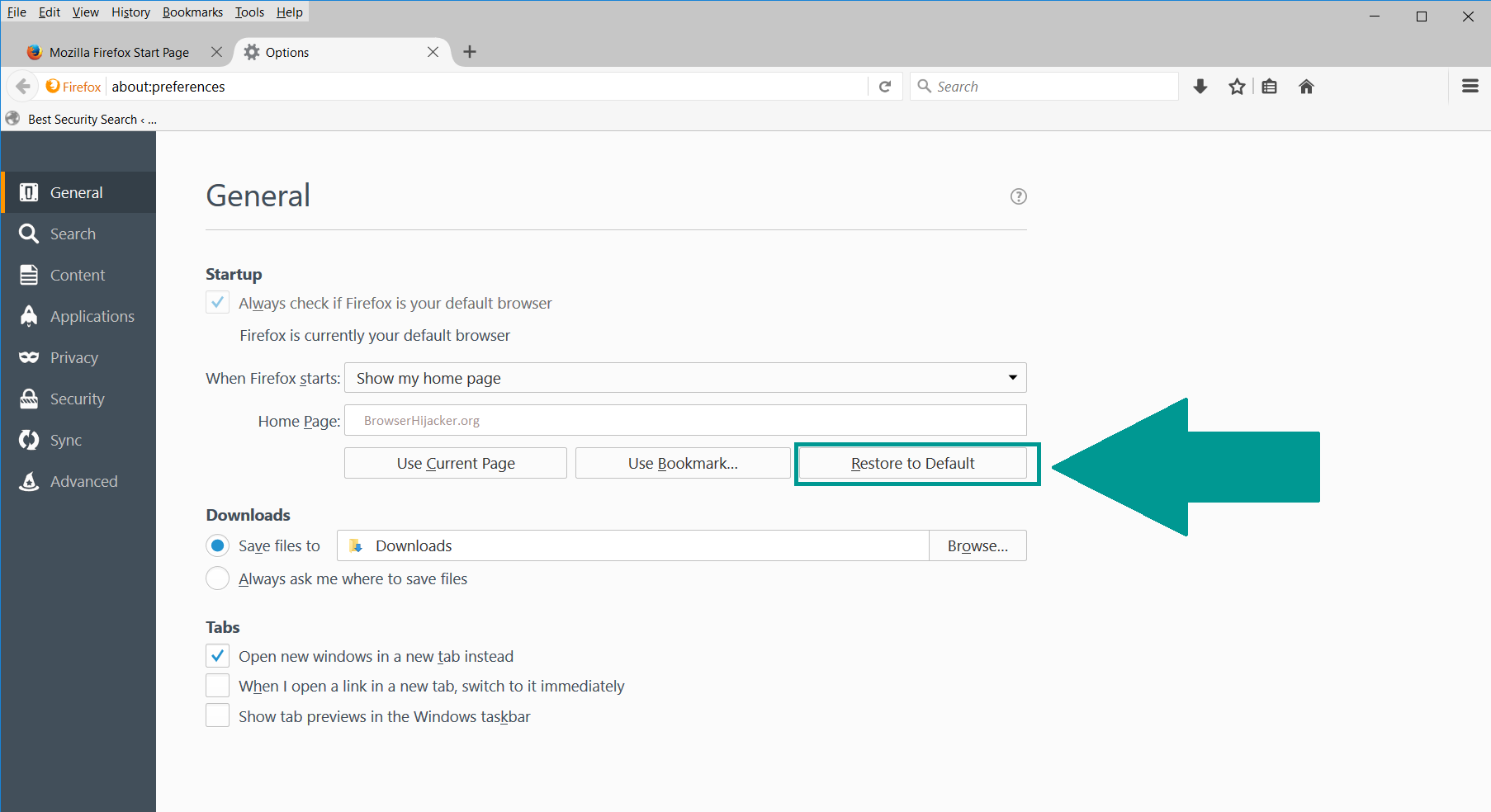
5. Select “Search” in the left menu, mark the unknown search engine and press “Remove”.
-
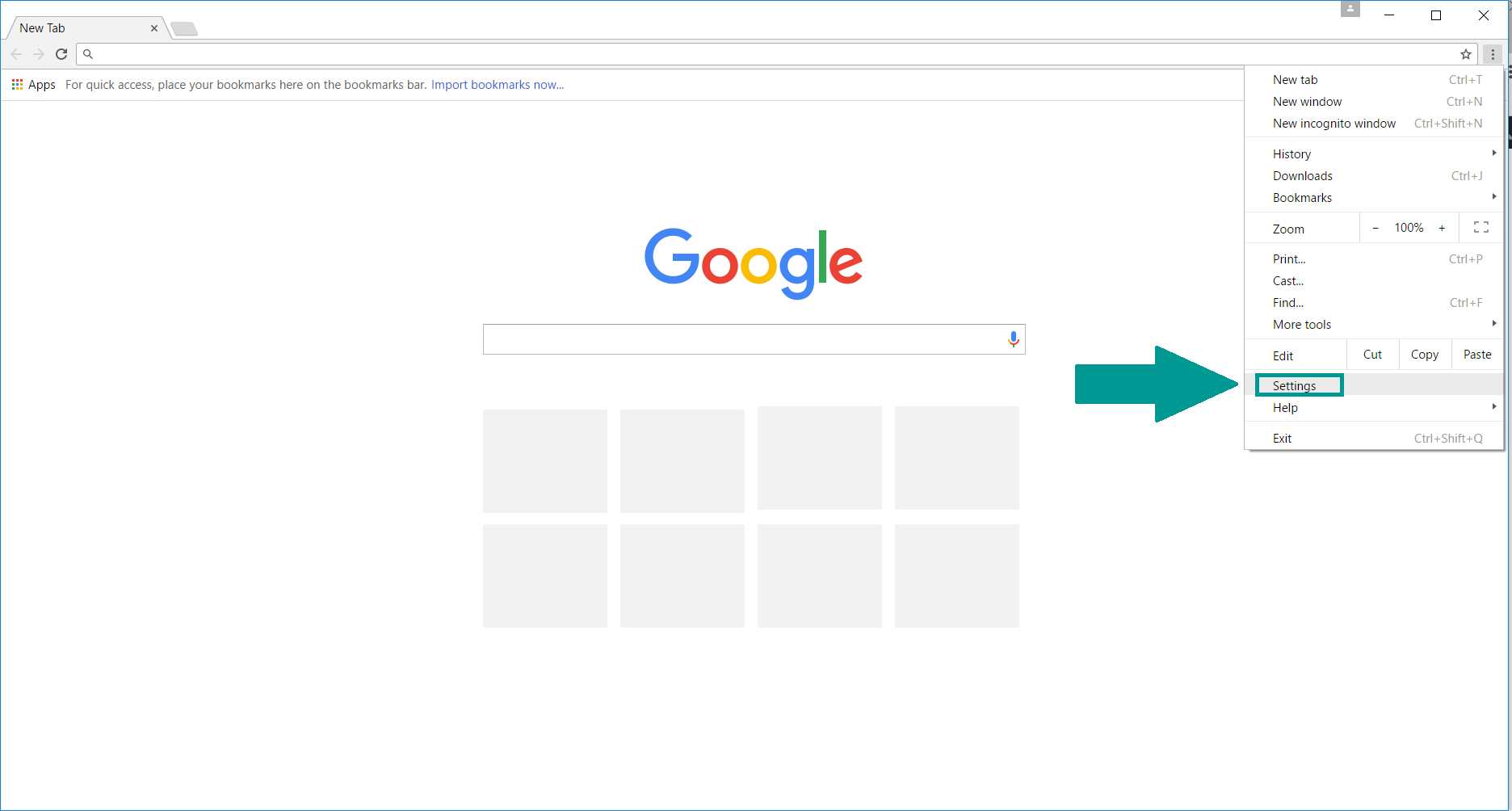
1. Start Google Chrome. On the upper-right corner, there a “Customize and Control” menu icon. Click on it, then click on “Settings“.
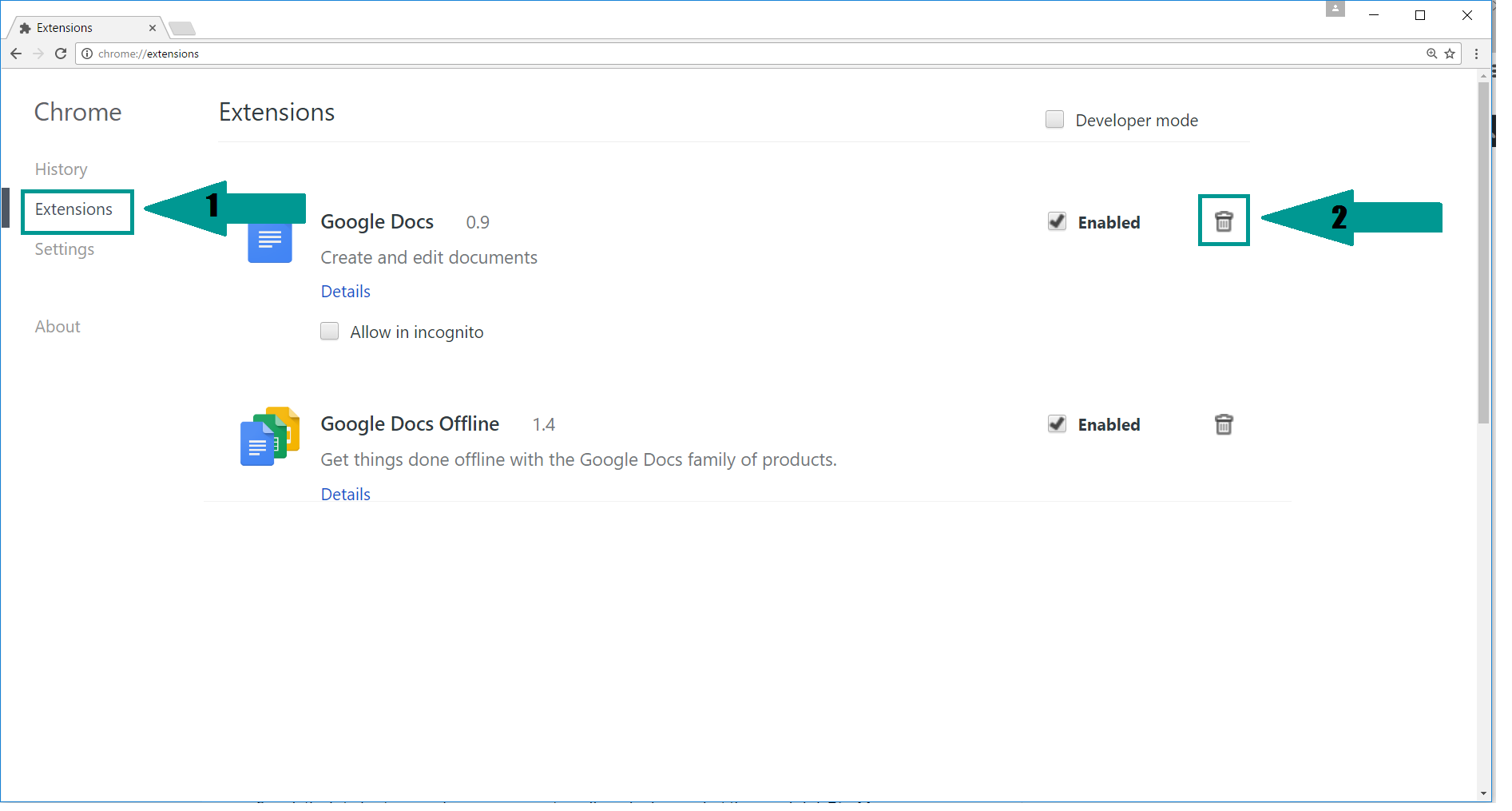
2. Click “Extensions” in the left menu. Then click on the trash bin icon to remove the suspicious extension.
3. Again in the left menu, under Chrome, Click on “Settings“. Go under “On Startup” and set a new page.
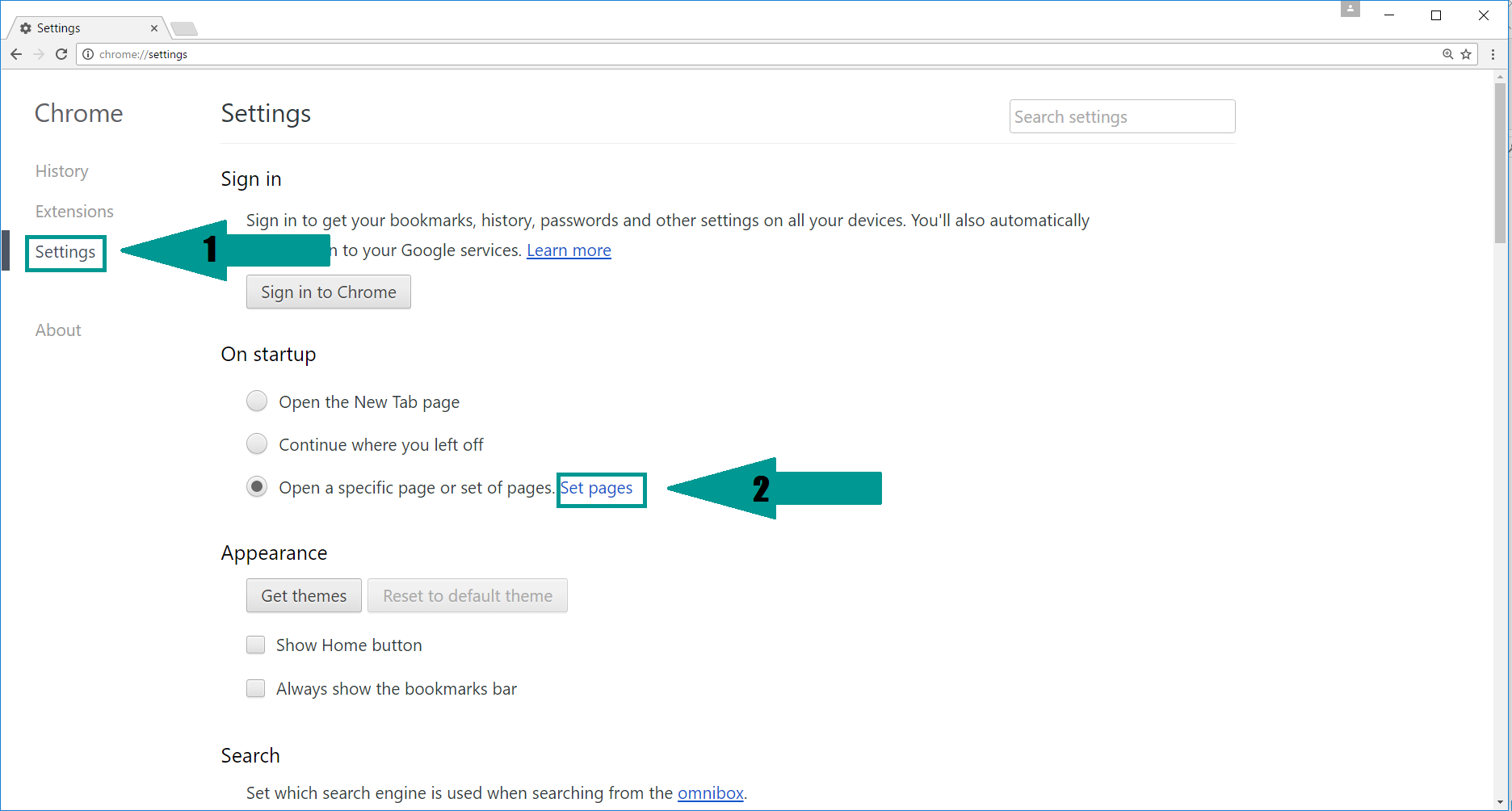
4. Afterward, scroll down to “Search“, click on “Manage search engines“.
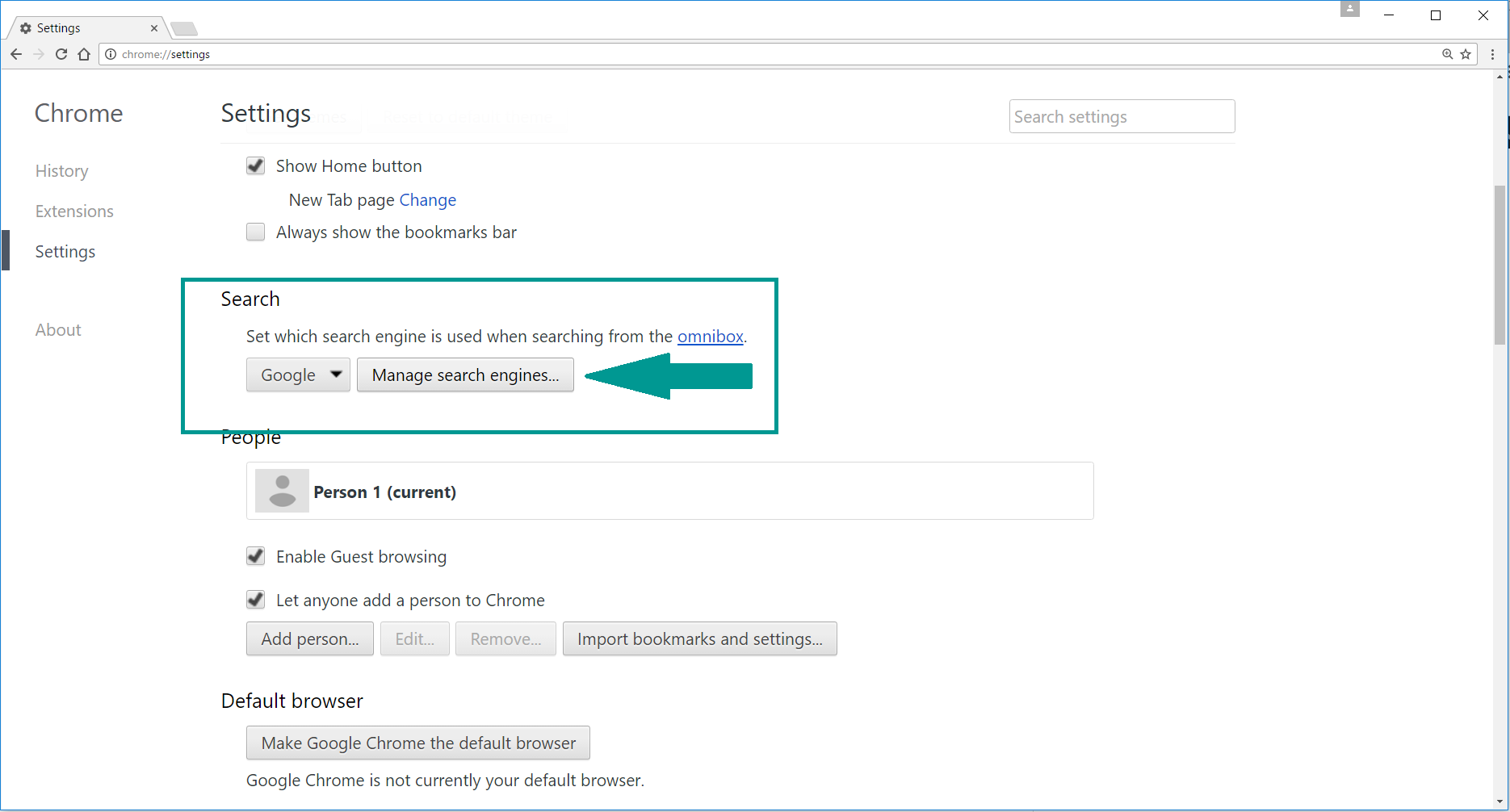
5. In the default search settings list, find the unknown search engine and click on “X“. Then select your search engine of choice and click “Make default“. When you are ready click “Done” button in the right bottom corner.
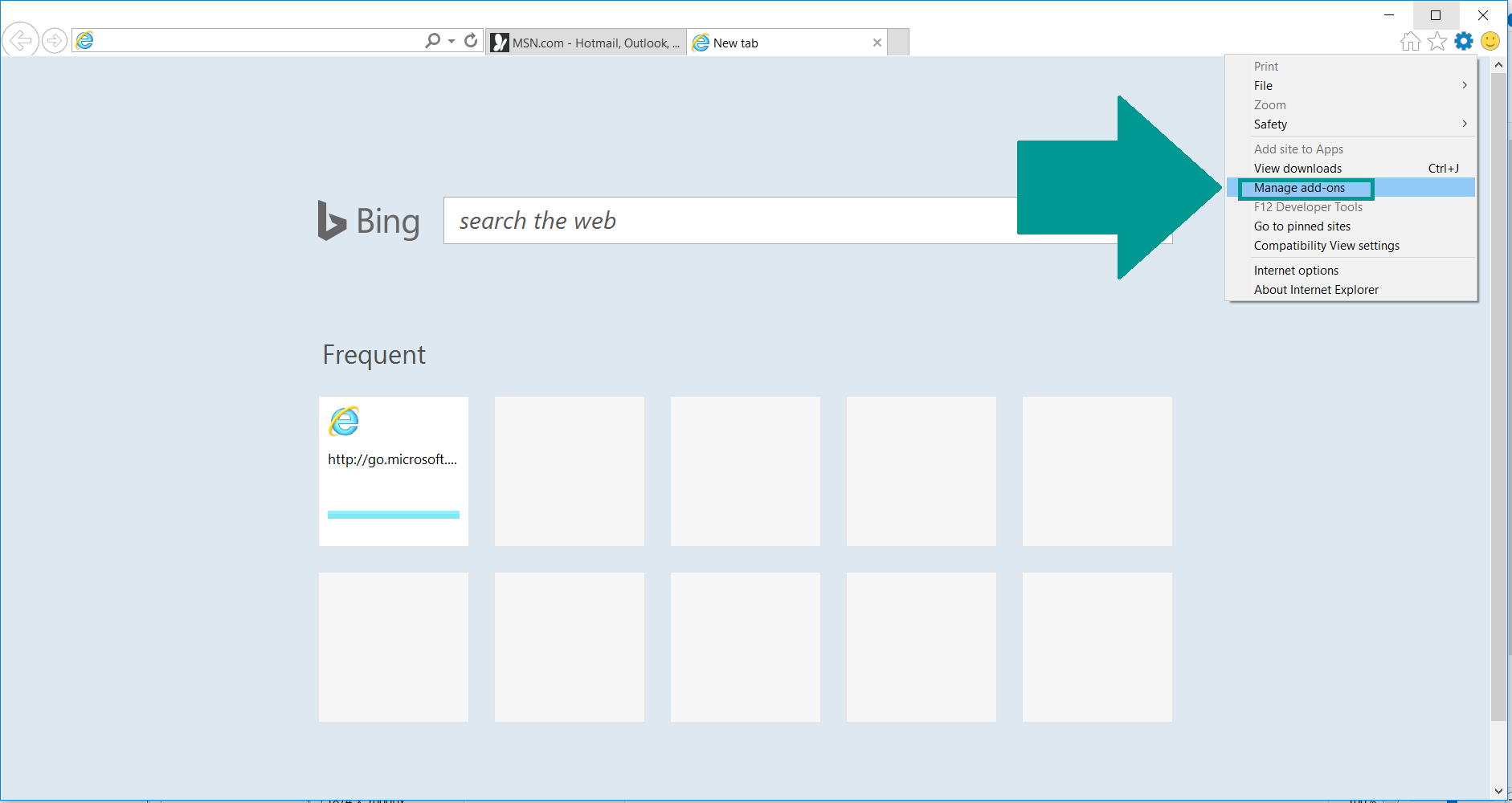
2. In the “Manage add-ons” window, bellow “Add-on Types“, select “Toolbars and Extensions“. If you see a suspicious toolbar, select it and click “Remove“.
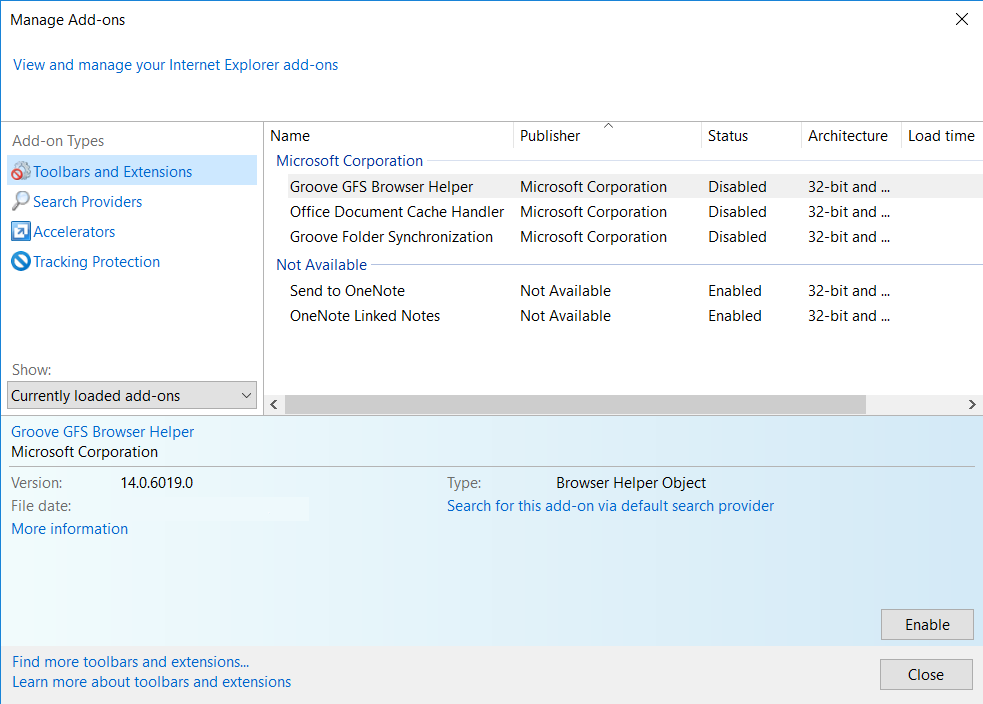
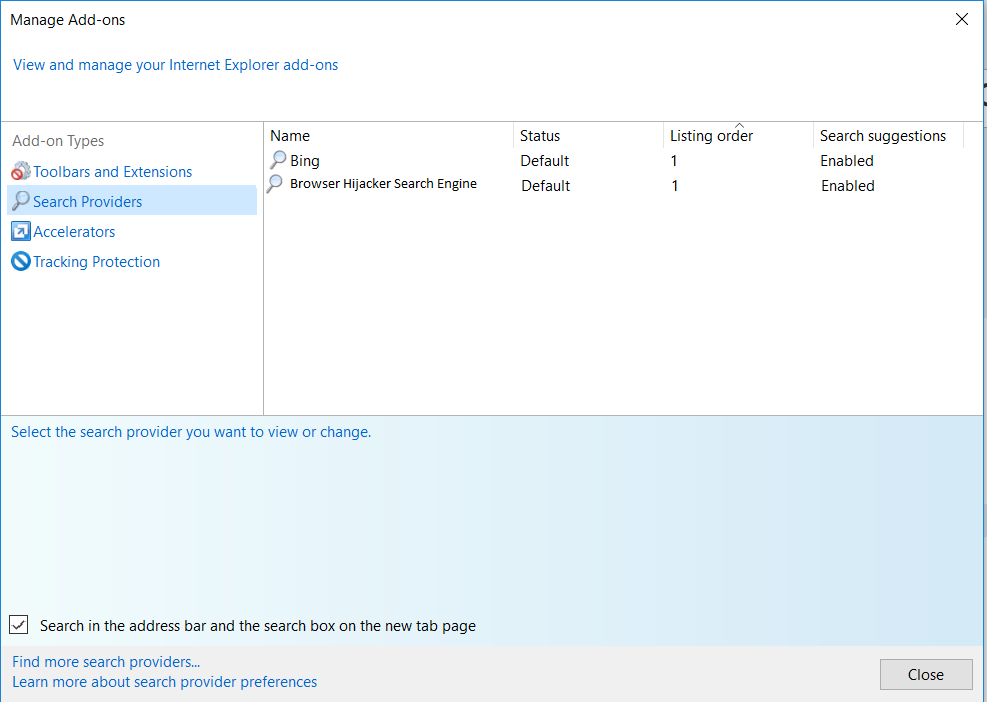
3. Then again in the “Manage Add-ons” window, in “Add-on Types“, Select “Search Providers“. Chose a search engine and click “Set as default“. Select the unknown search engine and click “Remove and Close”.
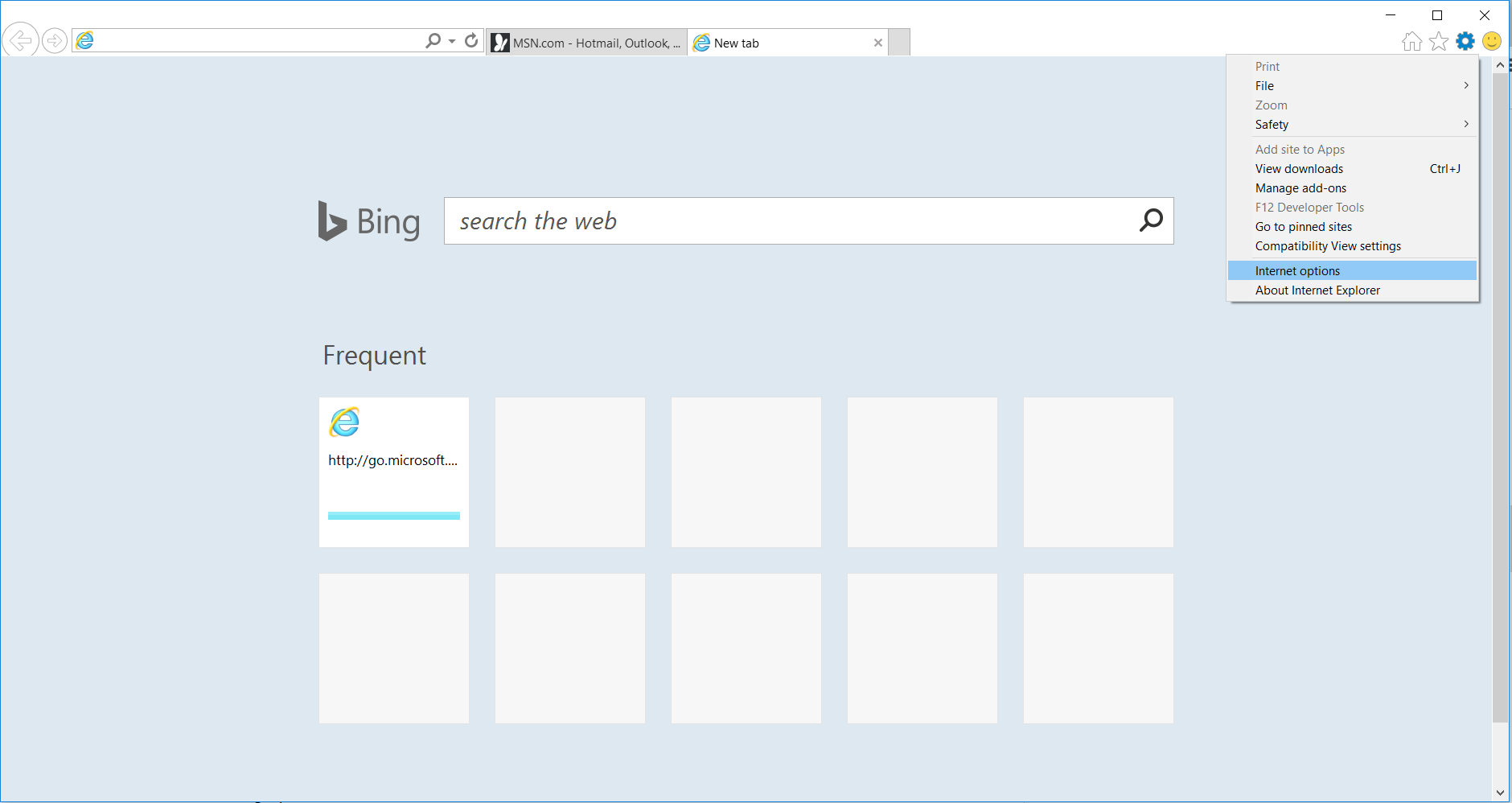
4. Open the Tools menu, select “Internet Options”.
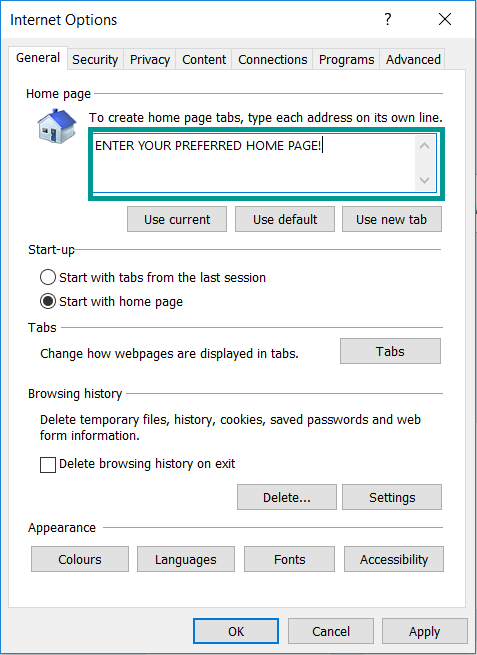
5. In the “General” tab, in “Home page”, enter your preferred page. Click “Apply” and “OK”.
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help



