A new Petya imitator virus has appeared that processes sensitive data, infections can be eliminated by following our removal guide.
Manual Removal Guide
Recover Petya Imitator Virus Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How Does Petya Imitator Virus Infiltrate the System?
Petya Imitator Virus is distributed as a single binary file (Petya+.exe) using different strategies.
A primary method of spreading malware such as this one is the use of email spam campaigns. The hackers send out template messages that usually contain social engineering tricks. The aim of the criminals is to confuse the targets into infecting themselves, either by downloading attached files or clicking on hyperlinks found in the body contents.
The Petya Imitator Virus samples can be hosted on download sites under different names, as well as P2P networks like BitTorrent where pirate content is usually found.
Web scripts, browser hijackers and redirects can also lead to a succesful infection.
Direct intrusion attempts are also possible. Hacker attacks are carried against computers and networks that use default settings or outdated software. One of the most popular applications that are suscepible to intrusions are remote control servers and Microsoft Windows built-in functions.
Related: Oops, your important files are encrypted (Petya) Ransomware Virus Removal, Restore Your Computer From a PetrWrap Ransomware Infection (Complete Removal Guide)
Infection Flow of Petya Imitator Virus
The Petya Imitator virus is a newly discovered malware that has just been reported by security researchers. The hacker or criminal collective behind it is unknown at this moment and there is no actual Petya code used. The imitator is custom made and is probably an original design done by its creators as the signatures do not match any of the famous malware families.
During the infection the Petya imitator virus has copied some of the behavior patterns associated with the legitimate virus. This includes the familiar looking check disk that is launched after the infection has been complete.
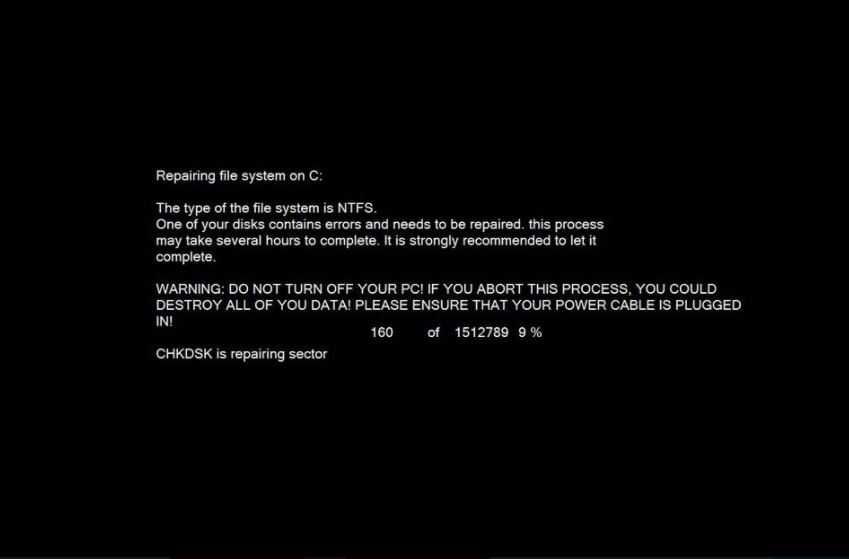
Fortunately the shown process is an emulation rather than a real system files check. After this process a skull logo drawn using ASCII characters is shown in an image. The lockscreen is initiated next. It aims to confuse the victims of the Petya imitator virus into believing that they are infected with the legitimate malware. The message reads the following:
You became a victim of the PETYA RANSOMWARE!
—
The harddisks of your computer have been encrypted with an military grade encryption algorithm. There is no way to restore your data without a special key. You can purchase this key on the darknet page shown in step 2.
To purchase your key and restore your data, please follow these three easy
steps:
1. Download the Tor Browser at “https://www.torproject.org/”. If you need help, please google for “access onion page”.
2. Visit one of the following pages with the Tor Browser:
xxxx://petya37h5tbhyvki.onion/n19fvE
xxxx://petya5koahtsf7sv.onion/n19fvE
3. Enter your personal decryption code there:
4827h91vo8724vz81972v4t12987v4z21h74vz210v49821
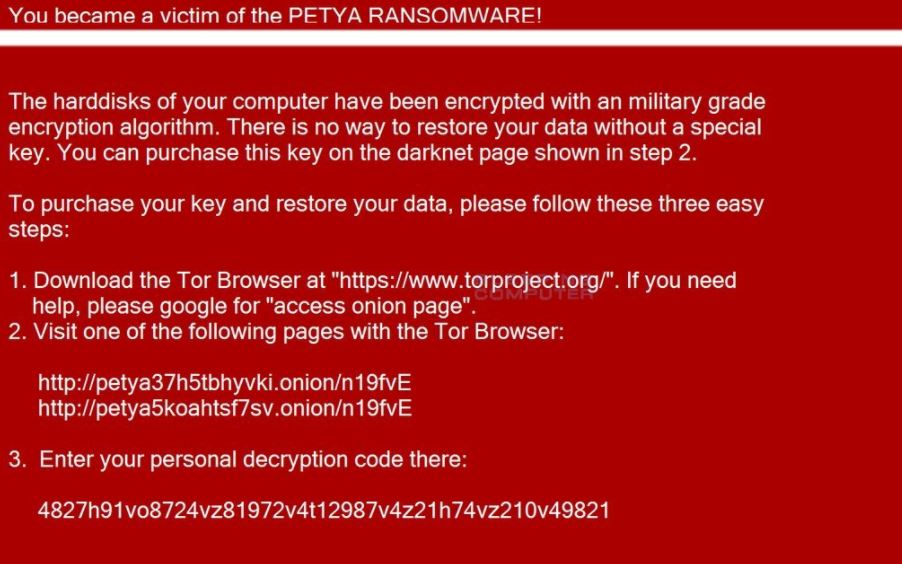
The victims are persuaded to download a browser capable of accessing the TOR Hidden network and visiting a payment gateway page to pay the hackers to restore their computers. We found out that the given addresses do not work.
The collected samples so far do not encrypt user or system files with a cipher. We suspect that future iterations might include a ransomware component. Even though in its current state the file names remain intact, the Petya imitator virus might include small strings or other modifications.
The lockscreen instance prevents any ordinary computer interaction until the Petya imitator virus is completely removed. It also displays an unique victim id (personal decryption code) that is calculated based on several input values. In most cases this includes harvested system information – user configuration, operating system version, regional settings, usernames, computer name and others.
Effective removal of the Petya Imitator virus can be achieved by scanning the computer with a quality anti-malware solution. Once the infections is identified it can easily restore your computer. Processed files can be recovered using a specialised application. Read our instructions below to learn more.
Remove Petya Imitator Virus and Restore Data
WARNING! Manual removal of Petya Imitator Virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Petya Virus Imitator – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
-
– Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
-
– Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Petya Imitator Virus Files
WARNING! All files and objects associated with Petya Imitator Virus should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD Petya Imitator Virus Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
-
– Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



