PetrWrap ransomware is a new Petya-based malware which uses a very dangerous MBR infection technique, read our removal guide to learn more about it.
PetrWrap Ransomware Description
Security experts discovered a dangerous new virus which has been ranked as very dangerous. The PetrWrap ransomware is a new threat which uses code from the infamous Petya ransomware and can cause serious damage to the infected computers.
This particular strain like its predecessors is used as part of a RaaS (Ransomware-as-a-service). This means that the virus is purchased as part of a complex infection scheme by experienced hacker collectives.
There are several unique characteristics that can be attributed to this particular strain:
- Mass Infection – Once the virus has infected a single computer it can use the PsExec utility to infect other hosts on the internal networks. This is a lightweigh telnet replacement which allows the execution of processes on other systems.
- The Petya Ransomware Encryption Engine Is Used – The computer criminals utilize the encryption engine of Petya to affect target user data.
- The Ransomware Features Its Own Custom Cryptographic Routine – When encrypting the PetrWrap implements its own routine to control the ciphers.
- PetrWrap Ransomware Identified With A Non-Traditional Behaviour – The virus follows a non-standard behaviour when infecting the target computers. This feature prevents detection by most anti-virus products which do not have the virus’s unique signature in their updated definitions list.
The technical analysis shows that the virus has been programmed in the C language and compiled using the Microsoft Visual Studio integrated development environment (IDE). The fact that the virus has been made using this language means that it is both small in size and that it can be ported to different environments (architectures and operating systems).
Upon infection the ransomware delays its execution with 1.5 hours. This is done in order to circumvent some of the basic heuristic scans which usually assume that when a virus infects a computer it begins instantly to cause damage to the host. The following routine is observed:
- The virus decrypts the mail DLL of Petya and gets ready to call the relevant export function.
- PetrWrap hooks several functions which prepares the host system for further damage.
- The virus engine computers the necesary cryptographic processes and starts to overwrite the Master Boot Record (MBR).
- After this phase is complete the virus hands over control to the Petya ransomware code.
The virus is rated as extremely dangerous as it compromises the Master Boot Record of the infected computer which prevents the normal boot-up of the operating system. Such operations are usually made by the most advanced viruses as recovery is very difficult. We remind our readers that the MBR is the first area of a physical disk which holds the information about the boot loader and available partitions. Specialized tools and trained specialists can recover the computers and remove the infections, manual methods may cause further damage.
In addition the Master File Table of all NTFS partitions is also encrypted. This contains the files and directory structure and all associated data – file names, creation date, access permissions and size. This means that effectively all accessible data is affected by the dangerous encryption engine.
To be able to provide a decryption route the hackers have replaced the encryption engine implementation with their own customized version whic allows the use of specially crafted public and private key pairs. The encryption-decryption process follows a detailed routine:
- The Trojan module contains an embedded public key master_pub which is different from the one used by the Petya ransomware module.
- During each infection the main encryption engine generates a new pair of session keys.
- SHA-512 is used to compute the shared digest
- The generated keys from the Petya module are intercepted and encrypted using the shared digest.
- A unique victim ID is generated for each infected host.
- The victim ID is passed on to the Petya encryption module.
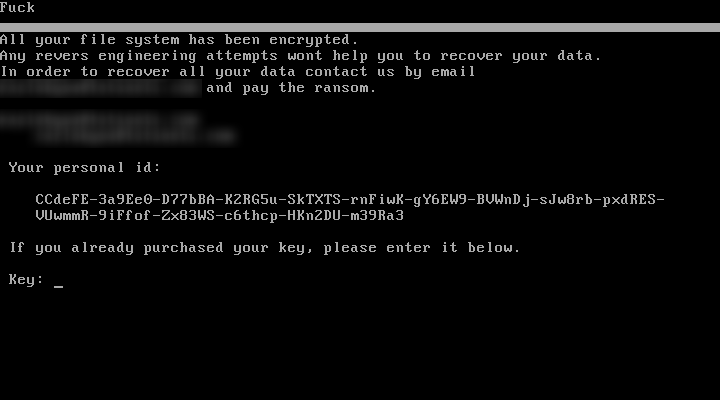
Once the encryption is complete the victim’s machine is locked. A lockscreen is then displayed which prohibits any user interaction at a very low level. The following text is displayed:
Fuck
All your file system has been encrypted.
Any reverse engineering attempts wont help you to recover your data.
In order to recover all your data contact us by email
XXXXXXXXXXXXXXXXX and pay the ransom.Your personal id:
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXX
XXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXXIf you already purchased your key, please enter it below.
Key: ….
PetrWrap Ransomware Distribution
The file is being distributed as executable binary files. At the moment there is no clear preferred infection method however we assume that the hackers employ the following strategies:
- Download Sites – Various hacker-controlled download portals and sites are a popular source of infections. They present the virus download by making it appear as legitimate software like games, applications, utilities and etc.
- Infected Installers – The virus is often bundled together with legitimate software installers of popular freeware and trial versions of applications, games and utilities. Depending on the configuration the user may be able to untick a checkbox and disable the virus.
- Ad Networks & Scripts – Malicious hacker-controlled ad networks can redirect to the virus payloads and also generate revenue for the operators. Scripts such as redirects and banners can also lead to a dangerous download site. Browser hijackers are another infection source which can infect the computers with the PetrWrap Ransomware. These extensions are primarily created for the most popular web browsers (Mozilla Firefox, Google Chrome and Internet Explorer) modify the user settings to point to hacker-controlled sites. The default home page, new tabs page and default search engine are modified accordingly. In addition most browser hijackers seriously invade the privacy of the victims by extracting the stored history, cookies and stored accounts.
- Exploit Kits and Automated Attacks – Vulnerability testing and intrusion attempts are popular with exploit kits and other related attack frameworks.
Summary of the PetrWrap Ransomware
| Name |
PetrWrap Ransomware |
| File Extensions |
N/A |
| Ransom |
Unknown |
| Easy Solution |
You can skip all steps and remove PetrWrap Ransomware ransomware with the help of an anti-malware tool. |
|
Manual Solution |
PetrWrap Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
PetrWrap Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely PetrWrap Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover PetrWrap Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore PetrWrap Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



