While making a password, you must have encountered the password safety meter, a tool that lots of mainstream sites employ to score the security of your imputed passwords. Recent studies, however, report that these tools may be ineffective.
How does password scoring work?
The password scoring meters work by measuring the length of the password and how many letters, number, uppercase letters, symbols. Including them is helpful and does make the password stronger. However, the meters have a lot of holes in their assessment. The methods that the meters warn against are the dictionary brute force attacks, which are rare. Brute force attacks try every possible combination, starting with the most widely used options, like 123456789, qwerty, zxcvbnm, etc. and continuing with dictionary words and other simple combinations.
The problem is that brute force hacking of passwords is neither the best nor the most widely used method of breaking into computers. Swapping letters with numbers (i with 1, e with 3, s with 5, b with 8, etc.) makes your password much stronger according to the security meters, but that’s not actually the case. Hackers know full well about this trick, and their password hacking algorithms are prepared for it.
Passwords and Security
A test conducted by Naked Security tried the efficiency of 5 popular passwords; abc123, trustno1, ncc1701, iloveyou! and primetime21. They were all considered weak by most password strength meters, though iloveyou! and primetime21 scored “Good” and “Mediocre” scores. Since the passwords were taken from the “10,000 Top Passwords list” they’re very unsecure, and users shouldn’t use them under any circumstances. The Naked Security test used the open source password cracker John the Ripper and cracked all password in about a second.
The Table of Passwords Provided in the Survey:
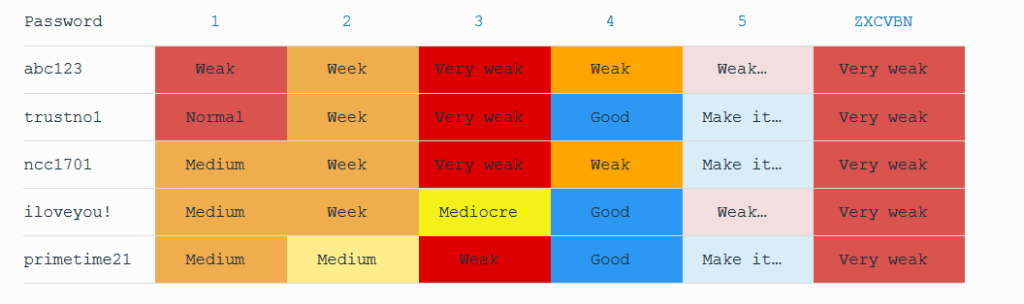
The article suggests that password scoring meters should outright forbid the usage of generic passwords like 123456789 and qwerty. The article further criticizes the meters by saying that “the meters also muddy the waters with misleading or ambiguous terminology and colors – what is a medium or mediocre password?”
Alternative Password Assessment
Since the strength meters aren’t that good at scoring passwords, users do it by themselves. The guidelines to a good password are the:
- Don’t use information related to you, like your name, birthdate, nicknames, pets.
- Don’t just add digits at the end, like password123 or abc123
- Make your passwords long. Most sites demand at least eight characters into your password, but that’s not enough. Make it as long as you can.
- Make up a random system that only you are familiar with. A crude example would be to swap numbers on the numpad by jumping the five key diagonally and switching 5 with 0. Fans of the tv series The Wire would be familiar with this approach.
Why Do Hackers Need Your Password?
You might think that hackers wouldn’t be interested in you particularly, but you would be wrong. Even average Joes and plain Janes are threatened with hacking. Most hacks are carried out in massive attacks on sites. The target millions of users, and you might be among them. 200 million Yahoo accounts were compromised in a huge hack, and 15 million phone numbers were stolen in a hack of Telegram last month. The massive amount of stolen information is them stored in database dumps that are often sold for large sums of money. The risk of hacking only goes up if you don’t choose a secure password.
The information in these data dumps can be used to connect accounts across sites belonging to the same user. If that user has used the same password, then the crooks can kill two birds with one stone (a.i get into two accounts by hacking only one.)



