SecureDrop is an open source platform for communicating in a secure manner which was originally designed by Aaron Swartz and Kevin Poulsen as DeadDrop.
SecureDrop Continues DeadDrop’s Legacy
SecureDrop is the open source platform which was originally created by Aaron Swartz and Kevin Poulsen and was known as DeadDrop. This is a secure method for transferring files which involves placing removable storage devices (most often USB flash drives) in covert locations.
After the death of Aaron Swartz a new version of the platform was devised under the name of DeadDrop.
The project aims to help journalists and media organizations to communicate in a secure manner and institute anonymous and safe file transfers when it comes to sensitive material. The newest version (labeled as 0.3) includes a redesigned user interface which is easier to use for both sides – the source informers and the journalists and reports.
The installation procedure has also been made significantly simplified. Every version of SecureDrop is also bundled with grsecurity which is a well-known and trustworthy operating system enhancement which attempts to prevent exploit attacks. Security updates are also automatically sent out to all installation instances with a simple mechanism.
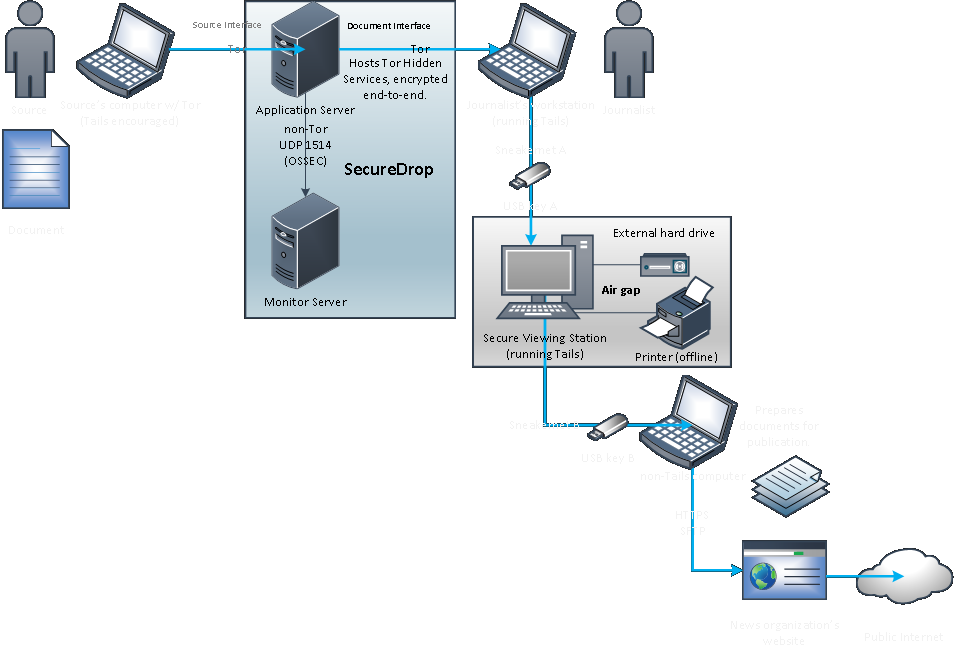
SecureDrop uses the anonymous network Tor to create a secure communications channel between the whistleblowers (sources), journalists and media organizations. The project instances are only accessible as hidden services on the Tor network. After a user visits an active SecureDrop site they are presented with a randomly generated code name. This alias is used to send the information to a particular author or editor via a file upload. The journalists and interested media can use the integrated messaging function to contact the source.
A typical scenario is the following:
The journalists use two USB flash drives and two separate computers to access the SecureDrop data. The first computer accesses the SecureDrop node via TOR and downloads the data in encrypted form from the Web. The second computer is connected physically to the Internet and its memory is wiped clear during each reboot. A second flash drive containing the decryption code is used alongside the downloaded data. Only then the source materials can be accessed by the journalists.
As such the environment requires several separate components:
- Secure Viewing Station – This is an airgapped laptop computer running the Tails Gnu/Linux distribution from a removable USB flash device. This computer is used to decrypt and view the source documents.
- Application Server – This instance is powered by an Ubuntu server which runs two segmented TOR hidden services. The source connects to the public-facing node to send the messages and documents to the journalists. The journalist connects to the second authenticated TOR node to download the encrypted documents and respond to source communications.
- Monitor Server – An Ubuntu Server which monitors the Application Server and sends relevant email alerts.
- Journalist Workstation – The laptop that the journalists use for every day use. This computer is used to connect to the Application Server and the download of the encrypted documents which are then transferred to the Secure Viewing Station. This is also used to respond to the sources.
For more information on the project visit its official site.