The Netskope Research Labs published a detailed report on the CloudFanta malware campaign that is a sophisticated banking Trojan.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
About The CloudFanta Malware Danger
The Netskope Security Labs published a report about the CloudFanta malware campaigns that have actively targeted computer users since the summer season. This malware is used to steal banking account credentials from the victim users. What is more interesting about it is that it benefits from the SugarSync program. This is a cloud-storage application that is used to distribute CloudFanta and store the harvested data.
The attacks are made through malicious links placed in phishing emails that use social engineering tricks to lure the users into clicking them. In some of the captured samples dangerous attached files that carry the threat have also been used. According to the Netskope researchers the following URL is one of the main distribution sources:
- “https://www[.]sugarsync[.]com/pf/D3202366_07280196_66523?directDownload=true.
A downloaded ZIP compressed file with the name “NF-9944132-br.zip” contains the payload downloader (with the JAR extension) “NF-9944132-br.PDF.jar”. This ten downloads the malware files which are detected as the following virus threats:
- Backdoor.Generckd.3549404
- Backdoor.Generckd.3540808
- Backdoor.Generckd.18673650
- Backdoor.Generckd.3542220
- Gen:Variant.Symm.60013
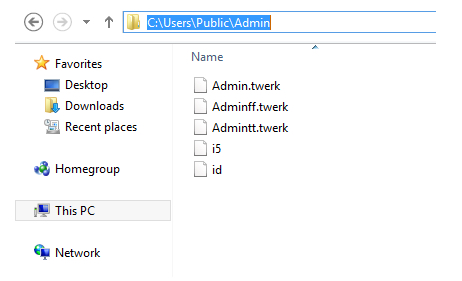
The Jar file downloads the DLL malware in the background and places it in the C:\users\public location. This propagation scenario is dangerous because the payload downloader utility downloads the DLL file with the counterfeit extension PNG and uses a secure connection using the SSL/HTTPS protocols. This means that several security measures can be bypassed such as firewalls and intrusion detection systems. The downloaded DLL files are renamed with the hostname name and the downloader appends the TWERK extension.
According to the security analysts the malware can target specific users and looks for string combinations that feature email addresses and account credentials (usernames and passwords) for various banking sites.
CloudFanta Malware Capabilities
This particular threat can be used against specific targets, the active campaigns right now actually target Brazil. CloudFanta works by using phishing pages that are installed via browser redirects. The virus detects when the user is about to enter a secured account and places the redirect link. The hackers include advanced infection measures, as this malware can bypass the virtual keyboards that are often used by banks.
The C&C servers have the ability to serve various commands including the following:
- View – displays the access list
- Clean – empties the access list
- Amount – Shows the number of unique hits
- All – An extra command that serves to include repeated access
Two registry entries are also added during infection:
- HKU\S-1-5-21-1960408961-1425521274-839522115-1003SoftwareMicrosoftWindowsCurrentVersionRunWin7
- HKU\S-1-5-21-1960408961-1425521274-839522115-1003SoftwareMicrosoftWindowsCurrentVersionRunWin
The banking Trojan also disables the User Account Control (UAC) and terminates the following processeses if they are found running on the compromised systems – taskmgr.exe, Taskmgr.exe, TASKMGR.exe, chrome.exe, Firefox.exe, msconfig.exe, regedit.exe, itauaplicativo.exe, ccleaner.exe and ccleaner64.exe.
The account information is harvested via screenshots that the virus makes of every single user click. The information is then saved to a text file that contains the log file of the user’s behavior.
The malware abuses cloud applications like SugarSync and Dropbox to host its malicious files. The code features an automation capability which automatically spreads the user to new targets.
CloudFanta Malware Damage & Remedy
The security researchers have already identified multiple strains of the CloudFanta malware that contact similar C&C server host. Apparently the virus is self-replicating itself thanks to the numerous infections. According to the reports thousands of compromised machines are suspected to be caused by the malware.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



