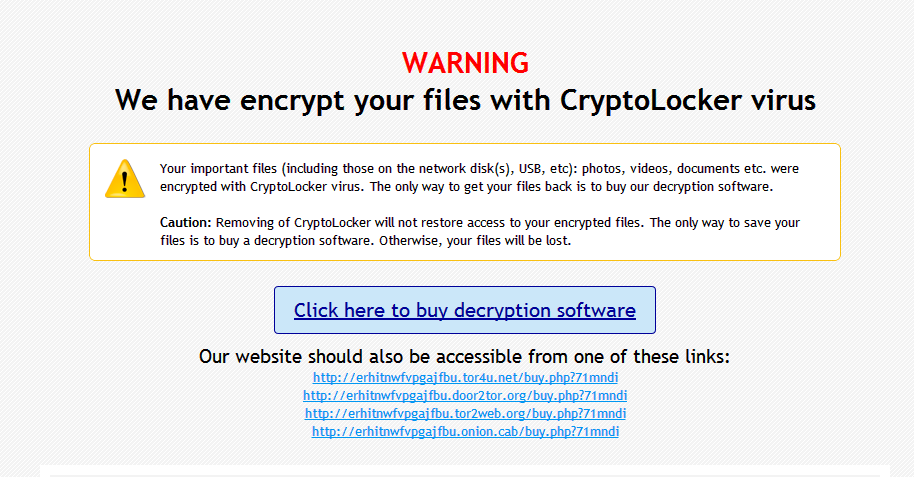
A new TorrentLocker ransomware computer virus has been discovered by security researchers. The updated iteration has been spotted in an ongoing attack campaign against computer networks and individual users located in Denmark. Continue reading our in-depth analysis and removal guide to learn how to remove active infections from your PC and protect yourself in the future.
New TorrentLocker Ransomware Description
Malware researchers have been able to identify two separate email spam campaigns that carry a dangerous threat – a new TorrentLocker ransomware strain. The virus is also known under the alias of CryptoLocker. Upon infection the virus immediately starts to execute its built-in commands. In comparison with the previous iteration the virus contains several new features:
- The virus engine has a new module which is able to actively scan, extract and transmit account credentials such as usernames and passwords. They are usually stored in browser settings, registry entries and other easily-accessible storage locations.
- TorrentLocker ransomware can now spread to other computers by infecting shared files and folders.
The former version of the TorrentLocker ransomware targeted computer users and businesses all over the world. The first campaigns focused on Italy and like other ransomware strains they encrypt target user data. TorrentLocker’s previous version used a similar infection to spread over the Internet (read more distribution below). The virus sends out a malicious ZIP file which contains a JS file. Upon interaction with it the virus activates itself and contacts the remote command and control server (C&C). The final payload is downloaded in the %TEMP% location. Depending on the issued virus it may drop other files (such as other viruses) to some of the following system folders:
- %AppData%
- %Windows%
- %Roaming%
- %SystemDrive%
- %Local%
- %User’s Profile%
Contemporary versions of TorrentLocker (both the old ones and the updated versions) have the ability to create registry entries to create a persistent environment. This severely limits the possibilities of a successful manual removal. The list of possible locations includes the following registry entries:
- HKEY_LOCAL_MACHINE\Software\Microsoft \Windows\ CurrentVersion\RunOnce
- HKEY_CURRENT_USER\ Software\Microsoft \Windows\CurrentVersion \RunOnce
- HKEY_LOCAL_MACHINE\Software \Microsoft\Windows\ CurrentVersion \Run
- HKEY_CURRENT_USER\ Software\Microsoft \Windows\ CurrentVersion\Run
After the final TorrentLocker payload is delivered onto the system the encryption process is initiated. Based on a built-in list of target file type extensions, the virus’s engine begins to encrypt the user data. In many cases the list includes the most popular documents, music, photos, videos, configuration files and etc. All affected data are renamed with the .enc extension or are assigned a randomly-named 6-character extension. A generic ransomware note is displayed to the victim user. It may appear differently according to the strain.
A partial list of some of the files that it affects includes the following:
*.wb2, *.psd, *.p7c, *.p7b, *.p12, *.pfx, *.pem, *.crt, *.cer, *.der, *.pl, *.py, *.lua, *.css, *.js,
*.asp, *.php, *.incpas, *.asm, *.hpp, *.h, *.cpp, *.c, *.7z, *.zip, *.rar, *.drf, *.blend, *.apj,
*.3ds, *.dwg, *.sda, *.ps, *.pat, *.fxg, *.fhd, *.fh, *.dxb, *.drw, *.design, *.ddrw, *.ddoc,
*.dcs, *.csl, *.csh, *.cpi, *.cgm, *.cdx, *.cdrw, *.cdr6, *.cdr5, *.cdr4, *.cdr3, *.cdr, *.awg,
*.ait, *.ai, *.agd1, *.ycbcra, *.x3f, *.stx, *.st8, *.st7, *.st6, *.st5, *.st4, *.srw, *.srf,
*.sr2, *.sd1, *.sd0, *.rwz, *.rwl, *.rw2, *.raw, *.raf, *.ra2, *.ptx, *.pef, *.pcd, *.orf,
*.nwb, *.nrw, *.nop, *.nef, *.ndd, *.mrw, *.mos, *.mfw, *.mef, *.mdc, *.kdc, *.kc2, *.iiq,
*.gry, *.grey, *.gray, *.fpx, *.fff, *.exf, *.erf, *.dng, *.dcr, *.dc2, *.crw, *.craw,
*.cr2, *.cmt, *.cib, *.ce2, *.ce1, *.arw, *.3pr, *.3fr, *.mpg, *.jpeg, *.jpg, *.mdb,
*.sqlitedb, *.sqlite3, *.sqlite, *.sql, *.sdf, *.sav, *.sas7bdat, *.s3db, *.rdb, *.psafe3,
*.nyf, *.nx2, *.nx1, *.nsh, *.nsg, *.nsf, *.nsd, *.ns4, *.ns3, *.ns2, *.myd, *.kpdx, *.kdbx,
*.idx, *.ibz, *.ibd, *.fdb, *.erbsql, *.db3, *.dbf, *.db-journal, *.db, *.cls, *.bdb, *.al,
*.adb, *.backupdb, *.bik, *.backup, *.bak, *.bkp, *.moneywell, *.mmw, *.ibank, *.hbk, *.ffd,
*.dgc, *.ddd, *.dac, *.cfp, *.cdf, *.bpw, *.bgt, *.acr, *.ac2, *.ab4, *.djvu, *.pdf, *.sxm,
*.odf, *.std, *.sxd, *.otg, *.sti, *.sxi, *.otp, *.odg, *.odp, *.stc, *.sxc, *.ots, *.ods,
*.sxg, *.stw, *.sxw, *.odm, *.oth, *.ott, *.odt, *.odb, *.csv, *.rtf, *.accdr, *.accdt,
*.accde, *.accdb, *.sldm, *.sldx, *.ppsm, *.ppsx, *.ppam, *.potm, *.potx, *.pptm, *.pptx,
*.pps, *.pot, *.ppt, *.xlw, *.xll, *.xlam, *.xla, *.xlsb, *.xltm, *.xltx, *.xlsm, *.xlsx,
*.xlm, *.xlt, *.xls, *.xml, *.dotm, *.dotx, *.docm, *.docx, *.dot, *.doc, *.txt
Its important to note that the New TorrentLocker ransomware can also encrypt data stored on network shares. Some of the versions only do that when the share is mapped as a drive letter. Such consequences can be prevented by disabling write access to users that are not administrators.
Depending on the strain the crafted ransom note may bear a different name, most of the analyzed samples create a file name DECRYPT_INSTRUCTIONS.html. The page shows the ransom fee which may vary and the content is dependent upon the location of the user. Like other similar threats the hackers extort the victims for a ransomware payment in the Bitcoin crypto currency.
During early investigation when the virus first emerged, the ransomware was discovered to assign “user codes” to the victim computers. The experts identified that they were made in sequence which made it easy to access the payment gateways and gain further insight about the threat. TorrentLocker contacts the remote C&C servers using random subdomains using the HTTPS protocols. Newer strains feature a small built-in TOR network module which is makes it possible to initiate C&C sessions via the hidden services of the anonymous network. All communication is done using the AES-256 cipher in CBC mode.
The New TorrentLocker ransomware like its previous versions still exhibits localized ransom notes. According to the language settings and location of the victim computer the virus displays different information and payment information. The default page is in English and the virus has been identified to even have a default currency value which is set to US Dollars. The full list of TorrentLocker localized gateways includes crafted pages for the following countries:
Australia, Austria, Belgium, Czech Republic, Denmark, France,
Germany, Italy, Japan, Martinique, Netherlands, Norway,
Poland, Portugal, Republic of Korea, Spain, Switzerland, Taiwan, Thailand,
Turkey, United Kingdom
New TorrentLocker Ransomware Distribution
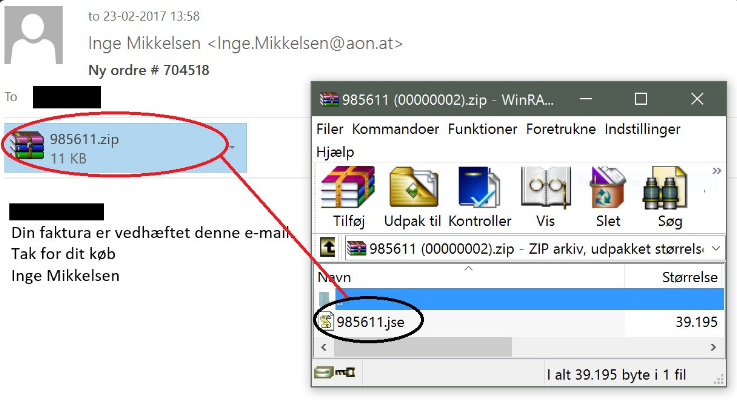
The virus is carried by two separate and large-scale spam email attacks which currently target computer users from Denmark. The hackers employ phishing tactics, a form of social engineering attacks in which the criminals design messages that resembles legitimate companies and institutions. The campaign in question sends out invoices that resemble as coming from a famous publisher of e-books located in the country. The hackers have bought a domain that closely resembles the company – the original site is e-boks.dk, while the counterfeit one is eboks.dk. The only difference is the dash in the name of the domain.
The message itself is very short and reads the following:
Din faktura er vedhæftet denne mail.
Tak for dit køb
Michael Andersen
This translates into English by reading this:
Your invoice is attached this mail.
Thanks for your purchase
Michael Andersen
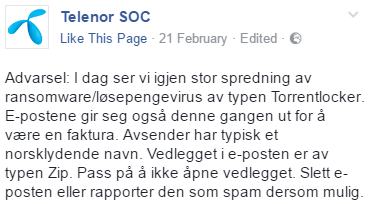
The mobile operator Telenor also issued a warning on February 21 about a dangerous spam campaign that distributes the New TorrentLocker ransomware. The criminals behind the attack send out e-mails that appear to be coming from the company. They contain a message in Danish:
Hallo
Vedlagt finner du betalingspaminnelse for faktura nr 751958
Nar det gjelder
Harald
Which translates to the following:
Hello
Enclosed you can find your payment reminder for invoice No. 751958
Harald
Telenor has warned that the senders part of the messages include random Scandinavian names to increase the infection ratio. The hackers have also utilized Dropbox links in some of the newly discovered messages.
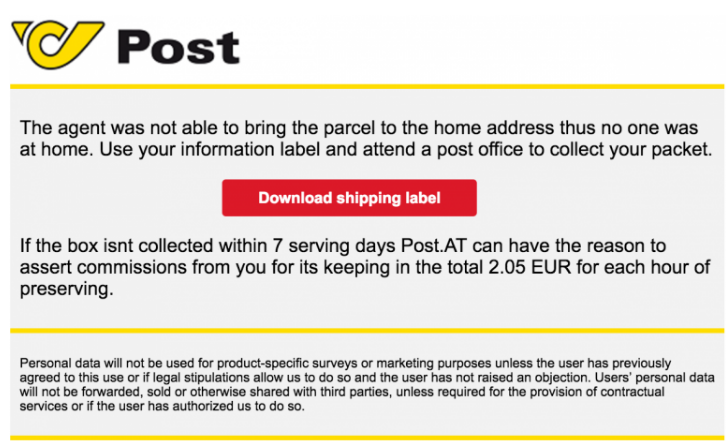
Impersonating well-known mobile operators is not something new. Between April and August 2016 the following companies were also used as a conduit in the spam messages to spread the ransomware:
A1 Telekom (Austria), AGL (Australia), Australia Post (Australia), Australian Federal Police (Australia),
British Gas (United Kingdom), Correos (Spain), Endesa (Spain), Enel (Italy), Österreichische Post (Austria),
New Zealand Post (New Zealand), PGE Polska (Poland), PostNord (Sweden), PostNL (Netherlands), Telia (Sweden),
Turkcell (Turkey), Verbund (Austria), Vodafone Italia (Italy).
Counterfeit shipment notifications and other related social engineering schemes have been employed by the criminals behind the virus.
A randomly-named Microsoft Word file is attached to the emails. Various numbers are used as file names which is the usual strategy for naming such documents. When the victims open the files they are presented with a “Protected View” prompt. If the user clicks on the “Enable Editing”, a PowerShell code is executed which downloads the dangerous payload. The virus itself is downloaded with a simple HTTP GET.
When redirects are caused by phishing links the following route of infections is employed:
- The spam messages and hyperlink are configured to point to a hacker-controlled redirection site.
- The redirection is triggered.
- A download prompt is initiated which downloads the dangerous payload to the local computer.
- If the user interacts with the file the virus infection follows.
The TorrentLocker ransomware injects itself into the running explorer.exe Windows process. This is the main user shell which draws the user interface and other graphics. It is also used to start other important applications and is a vital part of the operating system.
The spam campaigns have been noted as very aggressive and computer users should be extra cautious. The current iteration is hard to detect by most security solutions as its behavior patterns are rather complex. As the virus code has been updated significantly and the hackers have instituted various changes in the individual strains, this makes the malware a very serious threat.
However there are other infection methods that can be used as well which include:
- Infected Software Installers – Bundle malware are a very popular source of infection. Often freeware or trial versions of applications and games are modified to include TorrentLocker’s code. Other forms include patches, updates and system utilities.
- Email Spam Messages – Other email spam campaigns are also a popular source of infections.
- Download Sites and P2P Networks – The virus strains and associated files are often found on hacked or malicious download portals and sites, as well as popular BitTorrent trackers.
- Dangerous Scripts – Browser hijackers and malicious ads are a primary source of redirects which cause virus infections. Browser hijackers are dangerous extensions that are downloaded by the computer user which modify the installed browser’s settings: default new tabs page, search engine and home page. All queries and user information is harvested which seriously endangers the privacy of the victims. The entered queries, browser history and stored data is also endangered. Malicious ads include redirection scripts which can deliver the virus payload via a download site.
- The malware can extract address book contacts and SMTP settings from the victim computer and use the data to spread to them.
Summary of the New TorrentLocker Ransomware
| Name |
New TorrentLocker |
| File Extensions |
.enc or a randomly-generated 6-character extension |
| Ransom |
Varies |
| Easy Solution |
You can skip all steps and remove New TorrentLocker ransomware with the help of an anti-malware tool. |
|
Manual Solution |
New TorrentLocker ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
New TorrentLocker Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely New TorrentLocker Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
-
1) Use present backups
2) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



