LockLock ransomware is a new virus that uses the ever popular EDA2 open-source ransomware code. The files encrypted by the virus have the “.lockedlocked” file extension. The ransomware gets its name from there. Most infected users are reportedly from China, even though the virus is in English.
LockLock Ransomware – More About the Virus
LockLock isn’t that prevalent right now. However, it’s still a dangerous virus. It likely works in the usual way – the crooks spam emails containing malicious files, archives, URLs, and other connections that infect users who click on them. The emails are likely written in English and made to looks like regular emails sent by a company bot.
LockLock ransomware Virus – Further Analysis
The virus uses AES-256, a strong encryption algorithm. AES was also utilized by the NSA (National Security Agency), which further shows its strength. The virus gets into the system, scans it and encrypts files that it deems important. Files like:
- Videos
- Projects
- Documents
The targeted file types may be more numerous.
Once LockLock encrypts the files, it’ll add a ransom note with instructions for payment.
The Ransom Note’s Content in Text:
HELLO! YOUR COMPUTER HAS BEEN HACKED!
All files in your computer has been encrypted by RSA key You can not OPEN and READ content in file
HOW TO RESTORE ALL FILES?
Yes. I can help you and ONLY me can do it!
To UNLOCK your files you must:
1. Download tool “Decrypter LockLock virus”
2. Visit http://locklock.net and read information.
3. Enter Your Computer ID: (Open “READ_ME.TXT” on Desktop)
4. Run tools and enter Your Key then Click “Decrypt” button. DONE. ALL FILE RESTORED!
If you can not access website above, you can contact me:
– Email: [email protected]
– Skype Chat: locklockrs
The note is written in broken English, which is common for ransomware notes. Many scammers aren’t native English speakers. Domino ransomware also had an appallingly written ransom note. The scammer behind LockLock has provided email and Skype for contact. Skype isn’t a common way for cybercriminals to communicate with their victims, most prefer to communicate through email only.
The txt. document LockLock drops:
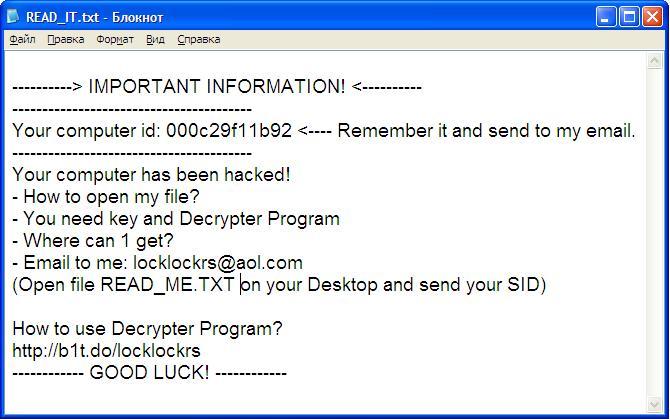
Victims can contact the LockLock scammer and try to bargain for a ransom price. There’s aren’t any decryption rates in the note. However, most scammers demand 1 BitCoint for the decryption key. Users aren’t advised to pay anything, as the crooks aren’t obliged to send the decryption keys after payment. Often victims pay hundreds of dollars only to be ignored by the scammers.
Another interesting thing that’s worthy of note is that the crooks have set up a YouTube channel that provides “assistance” in decrypting the files. It’s not very common for ransomware scammers to upload this type of videos.
LockLock Ransomware Virus – Summary and Conclusion
On one hand, LockLock is a typical ransomware virus. It uses a very common EDA2 code as its base, but on the other, the virus developer has chosen some unorthodox methods of communication with his victims. The YouTube channel is especially interesting, as it also shows an alternative version of the virus. The note is also very polite, wishing users “Good Luck” in the “READ_IT.txt” file of the virus.
It’s just interesting to note. This politeness is a far cry from the Noob ransomware’s taunts and insults. That doesn’t make the scammer any better, though. If your computer was encrypted by LockLock, you should search for a way to decrypt it. You may start by looking an anti-malware tool. There’s a lot of information on how to deal with malware, including ransomware on this very website.



