Kryptonite virus encrypts valuable data and blackmails victims into paying a $500 ransom to cyber criminals. Kryptonite belongs to the ransomware family which makes it one of the nastiest malware infections. When Kryptonite’s malicious payload is started, a crafted game of Snake appears and distracts victim’s attention while the ransomware performs various malicious activities on the infected host. PC security experts report crashes of Kryptonite samples during the reverse engineering process, so it is supposed to be a threat in development. Victims of Kryptonite ransomware virus are advised not to rush to pay the ransom and remove the threat from infected hosts safely. The information in our Kryptonite virus removal guide provides all essential steps that will help victims to restore infected PCs and encrypted data.
Manual Removal Guide
Recover Files Encrypted by Kryptonite Ransomware Virus
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Kryptonite Ransomware Virus Distribution
The malicious payload may be crafted in the source code of a corrupted webpage which URL address is spread across the Internet via personal messages, shares and posts on social media channels, online advertising campaigns, and spam emails.
Kryptonite is also likely to be hidden in malicious email attachments. The email may mislead users to be sent by their bank, internet provider, colleague, or even governmental institution. Spam emails distributors of ransomware infections like Kryptonite are usually written in a way to provoke a feeling of urgency and trick you into opening the attachment. It may be a document with malicious macros embedded in it, PDF file with an embedded Word document or another file that contains the malicious Kryptonite virus code.
Another attack vector for Kryptonite ransomware distribution may be freeware programs that use installation sets with bundled ransomware payload.
Detailed Look at Kryptonite Ransomware Virus
Kryptonite virus is a data locker ransomware, and its primary goal is to modify the original code of sensitive files with the help of RSA encryption algorithm. Thus they become inaccessible by victims, and cyber criminals can extort a ransom payment from them. Remember that cyber criminals often act dishonestly in order to gain the demanded $500 without providing working decryption solution.
The infection process begins once Kryptonite payload is running on the system. Тhe malicious executable files cad.exe, snake-game.exe, and snake_game.exe are associated with Kryptonite ransomware attack so far. They are developed in a way to terminate processes, read particular data, use their functionalities and create new malicious files. All these specifics set in Kryptonite malicious code allow it to perform various activities rendering the system extremely vulnerable at the end of the infection.
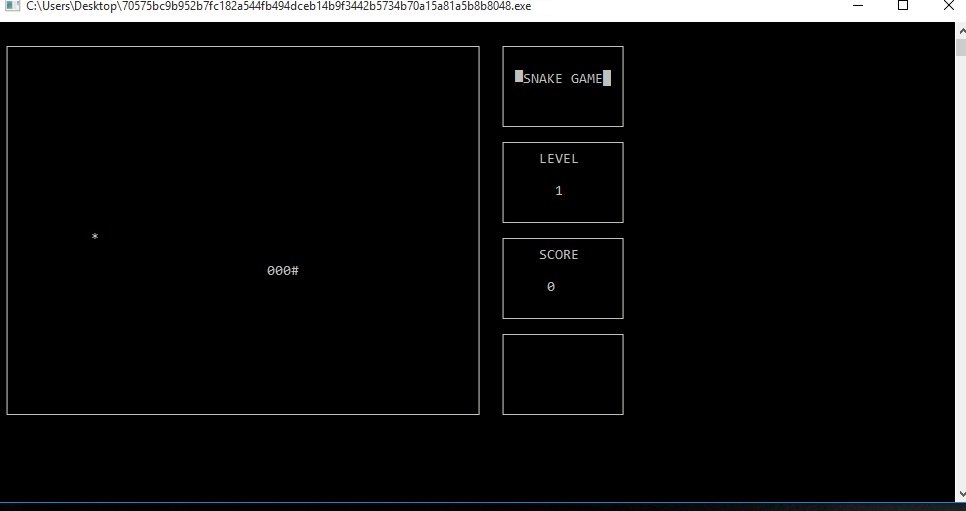
Kryptonite virus is disguised as a game of Snake which starts when the malicious executable is opened. Even though the ransomware is believed to be in development the game is running good and can be played. What some users may miss while playing the fascinating game is the nasty Kryptonite infection that is also running and corrupts particular files in the background. All files touched by Kryptonite virus remain inaccessible by any software except the decryption tool as they are encrypted via strong cipher algorithm. Currently, a particular file extension associated with Kryptonite ransomware is missing so corrupted files may be recognized by their icon (usually white sheet in Windows). Their file type may be changed, and a double click on a corrupted file won’t result in file opening. Usually, Kryptonite and other similar data locker ransomware like PSCrypt, affect files that contain valuable information like images, photos, videos, music, documents, text files, archives, and all MS Office documents.
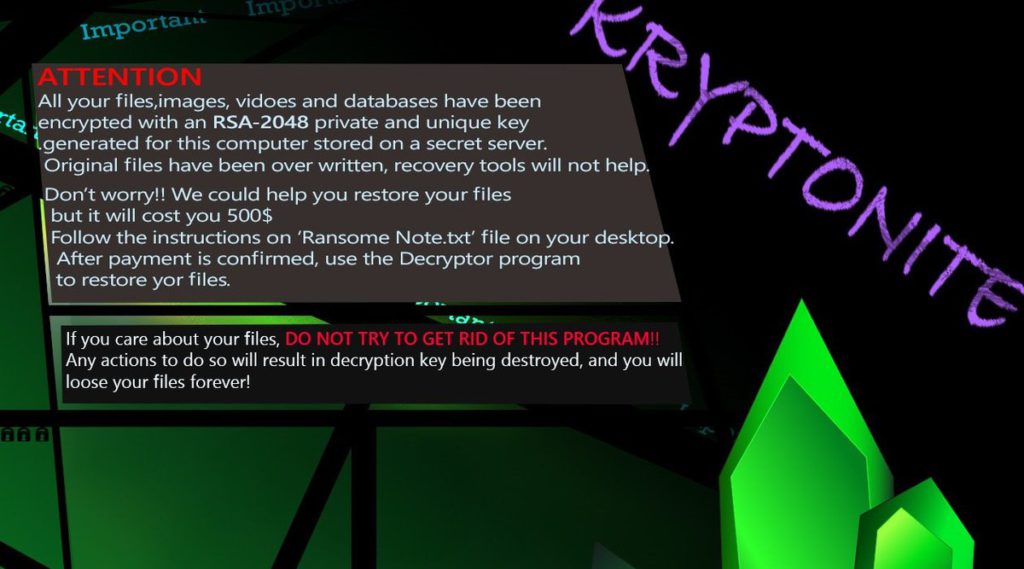
Of course, Kryptonite virus doesn’t remain hidden all the time. It is designed to replace the desktop wallpaper with an image called 1.jpeg and drop a ransom note file Ransom Note.txt on the Desktop. The 1.jpeg image depicts informative message about the infection and directs to the instructions included in Ransom Note.txt file. Here is the whole illustrated text:
“ATTENTION
All your files, images, vidoes and databases have been encrypted with an RSA-2048 private and unique key generated for this computer stored on a secret server.
Original files have been over written, recovery tools will not help.
Don’t worry!! We could help you restore your files but it will cost you 500$
Follow the instructions on ‘Ransome Note.txt’ file on your desktop.
After payment is confirmed, use the Decryptor program to restore yor files.
If you care about your files, DO NOT TRY TO GET RID OF THIS PROGRAM!!
Any actions to do so will result in decryption key being destroyed, and you will loose your files forever!”
The ransom message itself contains the following instructions:
“Kryptonite RANSOMWARE
All your important files are encrypted
Your files has been encrypted using RSA2048 algorithm with unique public – key stored on your PC.
There is only one way to restore your files : Contact with us, Pay 500$ and get your files back.
To pay us go to http://adsgoogle.eastus2.cloudapp.azure.com:27030/
This is a secured web-site for monetary transactions.
In order to make the transactions you will need the below ID.
After a successful transaction, disable your Anti-Virus and Firewall and run decryptMyFiles.exe as administrator.
Your ID:”
The URL address lands on a particular page with several fields where the ID, name on card, card number, CVV, and expiration date should be entered to pay the $500 ransom.
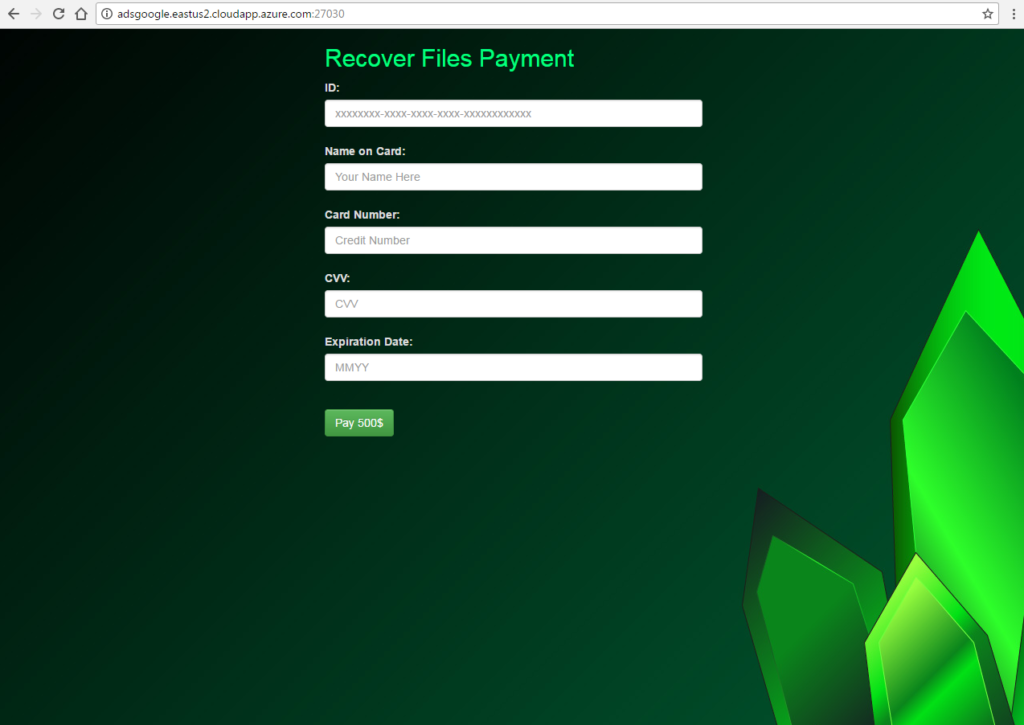
Attention! All of you who are Kryptonite victims are strongly advised to avoid entering any information; otherwise, you risk to grant access to all credit card details to the criminals and lost all your money. Don’t forget that the web page is likely to be completely controlled by them so they can extort all details.
Your encrypted files are not completely lost. Security specialists have cracked the malicious code of many ransomware threats, and eventually, they will succeed with Kryptonite too. Meanwhile, the guide below provides alternative data recovery solutions that may restore some important files efficiently.
Remove Kryptonite Ransomware and Restore Data
WARNING! Manual removal of Kryptonite Ransomware virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Kryptonite Ransomware – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
-
– Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
-
– Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover Files Encrypted by Kryptonite Ransomware Virus
WARNING! All files and objects associated with Kryptonite Ransomware virus should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD Kryptonite Ransomware Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
-
– Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



