The KK_ or “Estonian” ransomware now infects computers. Cyber-security experts report that the virus encrypts the files on the infected PC and demands 4 Bitcoins for their encryption. Encrypted files have the ??? extension at the end of their name.
The KK_ (Estonian) Ransomware Virus – General Information
The Estonian virus likely distributes using the usual methods of infection – email spam with malicious attachments.
The emails may look like they were sent from a retailer, a software company, the bank, PayPal, or another service that’s likely to send a notification through email. Users should be careful not to download any ZIP files, from shady looking emails, as they’re rarely legitimate.
Specifics of the KK_ (Estonian) Ransomware Virus – What Does it Do?
The ransomware encrypts the files of the computer, which locks them until they’re decrypted. The crooks running the virus scam hold the keys and won’t give them until the ransom is paid.
The virus creates files in the Windows’ folders that look like average system files. The virus also ads changes to the computer’s functions so that the ransomware will start along with the computer.
Files that are often targeted by ransomware viruses include:
- Videos, Clips
- Picture
- Documents
- Audio Files
The Estonian Virus also changes the desktop of the infected computer. This is done to display the ransomware note, which is named “KK_ IN YOUR DOCUMENTS.txt.” The note follows:
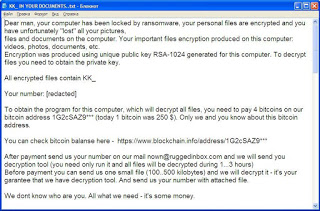
Dear man, your computer has been locked by ransomware, your personal files are encrypted and you have unfortunately “lost” all your pictures,
files and documents on the computer. Your important files encryption produced on this computer: videos, photos, documents, etc.
Encryption was produced using unique public key RSA-1024 generated for this computer. To decrypt files you need to obtain the private key.
All encrypted files contain KK_
Your number: ***
To obtain the program for this computer, which will decrypt all files, you need to pay 4 bitcoins on our bitcoin address 1G2cSAZ9*** (today 1 bitcoin was 250 $). Only we and you know about this bitcoin address.
You can check bitcoin balanse here – https://www.blockchain.info/address/1G2cSAZ9***
After payment send us your number on our mail [email protected] and we will send you decryption tool (you need only run it and all files will be decrypted during 1…3 hours)
Before payment you can send us one small file (100..500 kilobytes) and we will decrypt it – it’s your garantee that we have decryption tool. And send us your number with attached file.
We dont know who are you. All what we need – it’s some money.
Don’t panic if we don’t answer you during 24 hours. It means that we didn’t received your letter (for example if you use hotmail.com or outlook.com
it can block letter, SO DON’T USE HOTMAIL.COM AND OUTLOOK.COM. You need register your mail account in www.ruggedinbox.com (it will takes 1..2 minutes) and write us again)
You can use one of that bitcoin exchangers for transfering bitcoin.
decrypto.ee
https://localbitcoins.com/country/EE
https://www.clevercoin.com
coinera.eu
https://bitx.co
https://www.kraken.com
You dont need install bitcoin programs – you need only use one of this exchangers or other exchanger that you can find in www.google.com for your country.
Please use english language in your letters. If you don’t speak english then use https://translate.google.com to translate your letter on english language.
It’s ironic that the crooks demand from victims to write in English when their own ransomware note demonstrates such a weak grasp of the language. A similarly awful note was distributed with theDomino virus. It’s possible that the note was translated with the help of Google.
Here’s a Screenshot of the Ransomware Note:
KK_ or Estonian Ransomware Virus – Conclusion
The Estonian ransomware is a serious cyber-security threat. If you have it one your computer, we would not encourage you to pay the ransom before a decryption tool comes out, or you try another way of removal.



