The file extension .imsorry is associated with a newly discovered ransomware virus. It uses strong cipher algorithm that encrypts files and renders them inaccessible. Cyber criminals expect a ransom fee of $500 from victims in exchange for the unique decryption key. This article contains information about the threat and provides .imsorry file virus removal guide. Victims are better to refrain from ransom payment as, in addition, the instructions below suggest alternative .imsorry data recovery ways.
Manual Removal Guide
Recover .imsorry Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How Does .Imsorry File Virus Infiltrate the System?
Various attack vectors may be used for the malicious ImSorry.exe that triggers the ransomware infection. The most preferred way of ransomware payloads distribution is spam email campaigns. Such spam emails usually pose as legitimate services like banking or governmental institutions, internet providers, and well-known shopping websites. The email attributes that carry out malware infections are file attachments which contain the malicious code and corrupted website links. The attachments most often contain word document with malicious macros or PDF file with embedded malicious script. The links land users on websites with injected script that may exploit system or browser vulnerabilities via exploit kit or perform unnoticed drive-by download attack. Such links may also be spread via social media messages, posts, shares, file sharing services, instant messages and online advertisements (pop-ups, banners, thumbnails, videos, buttons). The malicious executable file may infect the system with ransomware during the installation of freeware or download of pirated content. Sometimes hackers bundle malicious code with other software installation setups, and that’s how .imsorry file virus may land on the PC.
Infection Flow of .Imsorry File Virus
It all starts when the file ImSorry.exe is running on the machine. Then the malicious ransomware code initiates scanning process for all file types predefined in its target data list. ImSorry ransomware virus has a built-in encryption module that is set to transform target data with the AES algorithm. Files that are formatted like documents, photos, images, music, videos, archives, and projects are likely to be renamed with the malicious file extension .imsorry upon the encryption process. The access of .imsorry files is restricted as their original code is entirely changed.
Furthermore, ImSorry ransomware has the functionality to perform the command line vssadmin.exe delete shadows /all /Quiet in Command Prompt which automatically removes all Shadow Volume Copies stored on the infected host and eliminates the chance to restore some .imsorry files via Shadow Explorer method.
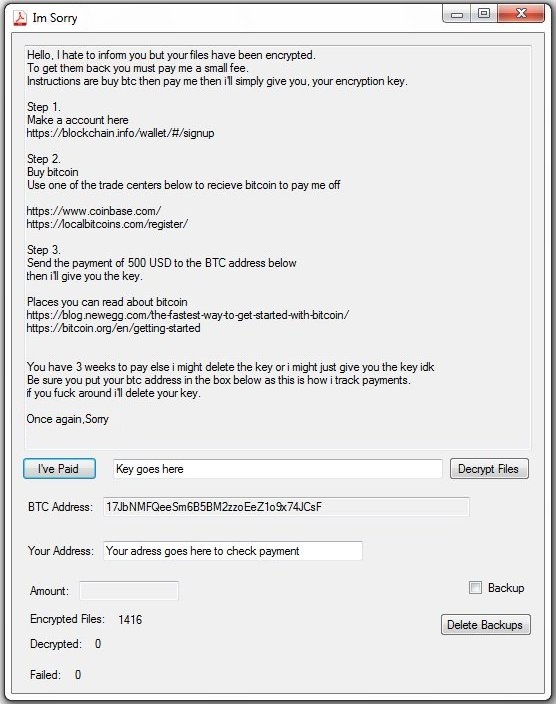
In a file called Read me for help thanks.txt hackers have left a ransom message to all victims of .imsorry file virus. The file contains payment instructions and details about their bitcoin address. There is also a counter of the encrypted, decrypted and failed to decrypt data. The ransom message is also depicted in a window that is believed to block access to the operating system. This is possible by Windows registry modifications of Run and RunOnce keys. The window is called Im Sorry and displays the following text and elements:
Im Sorry
Hello, I hate to inform you but your files have been encrypted.
To get them back you must pay me a small fee.
Instructions are buy btc then pay me then ill simply give you. your encryption key.
Step 1.
Make a account here
https://blockchain.info/wallet/#/signup
Step 2.
Buy bitcoin
Use one of the trade centers below to recieve bitcoin to pay me off
https://www.coinbase.com/
https://1ocalbitcoins.com/register/
Step 3.
Send the payment of 500 USD to the BTC address below
then i’ll give you the key.
Places you can read about bitcoin
https://blog.newegg.comAhe-fastest-way-to-get-started-with-bitcoin/
https://bitcoin.ong/en/getting-started
You have 3 weeks to pay else i might delete the key or i might just give you the key idk
Be sure you put your btc address in the box below as this is how i track payments,
if you fuck around ill delete your key.
Once again,Sorry
button [I’ve Paid] field [Key goes here] button [Decrypt Files] BTC Address: 17JbNMFQeeSm6B5BM2zzoEeZ1o9x74JCsF
Your Address: Your adress goes here to check payment
button [Delete Backups]
Even though cyber criminals claim that the only way to decrypt .imsorry files is to purchase their decryption key for the amount of $500 in BTC, this usually turns out to be not true. There are many reports from ransomware victims that inform about decryption keys that don’t work and even missing ones. It’s recommendable to remove .imsorry file virus completely from the computer and try alternative data recovery tools.
Remove .Imsorry File Virus and Restore Data
WARNING! Manual removal of .imsorry file virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
.Imsorry File Virus – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
-
– Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
-
– Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover .imsorry Files
WARNING! All files and objects associated with .imsorry file virus should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD ImSorry Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
-
– Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



