The OnyonLock virus is a new version of the BTCWare family of threats. It encrypts sensitive data and marks it with the .onyon file type extension. Victims can remove OnyonLock ransomware virus via:
DOWNLOAD ONYONLOCK Virus Removal Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Once the OnyonLock ransomware virus is removed successfully, you can try to restore your files following our instructions below.
The OnyonLock Ransomware Virus Impact on an Infected PC
The OnyonLock virus is a new malware threat based on the BTCWare family. In its current iteration it includes an encryption module that targets user data based on a predefined list of target file types. This can be customized based on the targets and we presume that it processes the most popular extensions: archives documents, photos, videos, music, databases, configuration files and etc.
All affected data is marked with the .onyon file type extension. A ransomware note is crafted in a !#_DECRYPT_#!.inf file that contains the following message:
All your files have been encrypted due to a security problem with your PC.
If you want to restore them, write us to the e-mail: [email protected]
You have to pay for decryption in Bitcoins. The price depends on now fast you write to us.
After payment we will send you the decryption tool that will decrypt all your files.
FREE DECRYPTION AS GUARANTEE
Before paying you can send to us up to 3 files for free decryption.
Please note that files must NOT contain valuable information and their total size must be less than 10Mb
How to obtain Bitcoins
The easiest way to buy bitcoin is LocalBitcoins site.
You have to register, click Buy bitcoins and select the seller by payment method and price https://localbitcoins.com/buy_bitcoins
Attention!
Do not rename encrypted files
Do not try to decrypt your data using third party software, it may cause permanent data loss
If you not write on e-mail in 3 days – your key nas been deleted and you cant decrypt your files
Your ID: 3WPn3rQFa*****
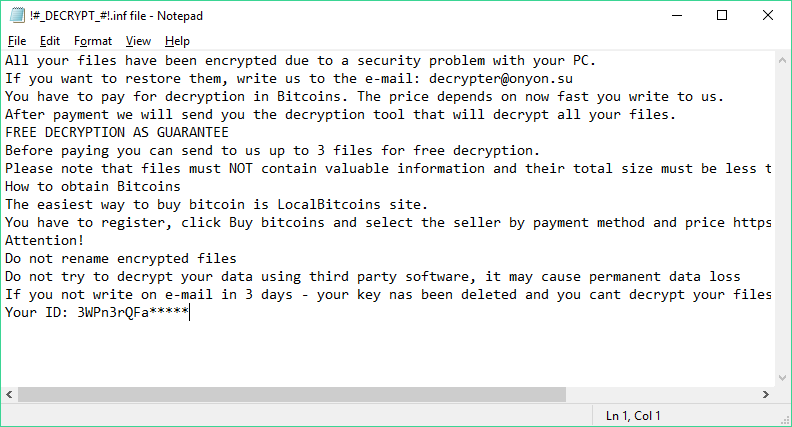
The OnyonLock ransomware note is placed in the users Application data and desktop locations. Like other similar threats it appends a unique infection ID that is based on collected system data. In addition it performs several other malicious system modifications:
- Data Deletion – The OnyonLock virus completely erases all shadow volume copies of the affected data. This makes file recovery impossible without the use of a quality data recovery solution.
- System Modification – OnyonLock virus modifies key Windows settings that set up a persistent state of execution. This means that the virus engine prevents the user from manually removing the threat as registry and boot settings are dynamically modified.
- Stealth Detection – The analysts discovered that there is a file associated with the OnyonLock virus that deletes the malware when a security software or another incident is detected. A quality anti-malware tool can effectively delete the OnyonLock virus.
The hackers behind the OnyonLock virus use two emails email accounts to provide “support” to the victims – [email protected] and [email protected]. Depending on the individual strain the ransomware note may contain either one of them. Victims can delete the OnyonLock virus by first deleting the malware engine itself and then restoring their data.
Similar Viruses: CryptoByte Virus
OnyonLock Ransomware Virus Distribution Methods
The OnyonLock ransomware virus can be contacted via different sources. The collected samples so far are relatively low in number and the experts cannot judge the primary method of distribution. Some of the include the following:
- Email Spam Message – Hackers coordinate emails that use social engineering tricks that attempt to make the targets infect themselves with the OnyonLock ransomware. The malware files are either attached directly to the messages or linked in the body.
- Infected Documents – The OnyonLock virus can be used with infected documents. The criminals bundle the threat in files (usually rich text documents or spreadsheets) that may be of user interest – invoices, letters and etc. When the users open them a notification appears that asks for their permission to execute the built-in scripts. If this is done the OnyonLock virus is downloaded from a remote server and executed on the local machine.
Remove OnyonLock Ransomware Virus and Restore .onyon Encrypted Files
WARNING! Manual removal of the SecretSystem ransomware virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
OnyonLock Virus – Manual Removal Steps
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely OnyonLock Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



