.Gryphon Virus is new ransomware strain descendant from the BTCWare malware family that uses the .Gryphon extension. Learn how to protect yourself and remove active infections from your PC by following our in-depth removal guide.
Manual Removal Guide
Recover .Gryphon Virus Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How Does .Gryphon Virus Infiltrate the System?
The .Gryphon virus can be distributed to targets using the different delivery methods. One of the primary ones is the coordination of mass email spam messages. They can be of several different types:
- Attachments ‒ The .Gryphon virus can be distributed as an attachment to the messages. The body content can contain social engineering tricks that can make the targets download and execute the strains.
- Malicious Hyperlinks ‒ Links that lead the users to infected binaries can be inserted in the body contents of the message.
- Combination ‒ Many email templates rely on using both methods to increase the infection ratio.
Usually the hacker operators aim to create messages that pose as being by a legitimate service or institution. Different social engineering tricks are used to make the victims infect themselves with the virus. Other .Gryphon virus distribution methods include the use of infected software installers. They are usually legitimate installers that have been downloaded from their official sources and modified by the hackers to include the .Gryphon virus code. They are then distributed on hacker-controlled portals and P2P networks. In most cases the malicious sites may use graphics and text to confuse the users into believing that they are downloading the real software.
Another source of .Gryphon virus instances can be a browser hijacker campaign. This is when malicious browser extensions lead to malware infections. Upon installation these plugins change important settings: the default home page, search engine and new tabs page to point to a hacker-provided URL. During the infection phase the malware can be delivered. As a consequence of the redirect the victims can have their security and privacy seriously affected as tracking cookies and web scripts are employed. They can be used to harvest sensitive user data: bookmarks, history, cookies, settings, form data and passwords.
Related: .725 Virus, .Cryptobyte Ransomware
Infection Flow of .Gryphon Virus
The .Gryphon virus is an advanced ransomware strain that has just been detected in an ongoing hacker attack. The security experts who reported it state that it contains code sourced from the BTCWare malware family. This means that the hackers behind it are probably either connected with the criminals behind prior attacks or have obtained the source code from the hacker underground markets.
The .Gryphon ransomware attacks follow the behavior patterns set by other related strains. When the infection has been initiated one of the first steps is to modify important system settings. This includes the Windows registry, the virus has been found to modify essential entries. Depending on the strains it may even institute a persistent state of execution. This means that the .Gryphon virus engine will monitor all user actions and system commands to effectively block manual removal attempts.
The ransomware starts its virus engine as soon as the initial infection is confirmed. Depending on the acquired strain the .Gryphon virus targets different file types. A sample file list affects the following data:
1c, .3fr, .accdb, .ai, .arw, .bac, .bay, .bmp, .cdr, .cer, .cfg, .config, .cr2, .crt, .crw,
.css, .csv, .db, .dbf, .dcr, .der, .dng, .doc, .docm, .docx, .dwg, .dxf, .dxg, .eps, .erf,
.gif, .htm, .html, .indd, .iso, .jpe, .jpeg, .jpg, .kdc, .lnk, .mdb, .mdf, .mef, .mk, .mp3,
.mp4, .mrw, .nef, .nrw, .odb, .ode, .odm, .odp, .ods, .odt, .orf, .p12, .p7b, .p7c, .pdd,
.pdf, .pef, .pem, .pfx, .php, .png, .ppt, .pptm, .pptx, .psd, .pst, .ptx, .r3d, .rar, .raw,
Artf, .rw2, .rwl, .sql, .sr2, .srf, .srw, .tif, .wb2, .wma, .wpd, .wps, .x3f, .xlk, .xls,
.xlsb, .xlsm, .xlsx, .zip
All affected data receive a .gryphon extension. Depending on the case different email address may be inserted, examples include [[email protected]].gryphon or .[[email protected]].gryphon. They are the hacker-provided contact addresses that the victims can use to write to the hacker operators.
A ransomware note is crafted in a HELP.inf or HELP.txt file. The collected samples show that the files contain the following message:
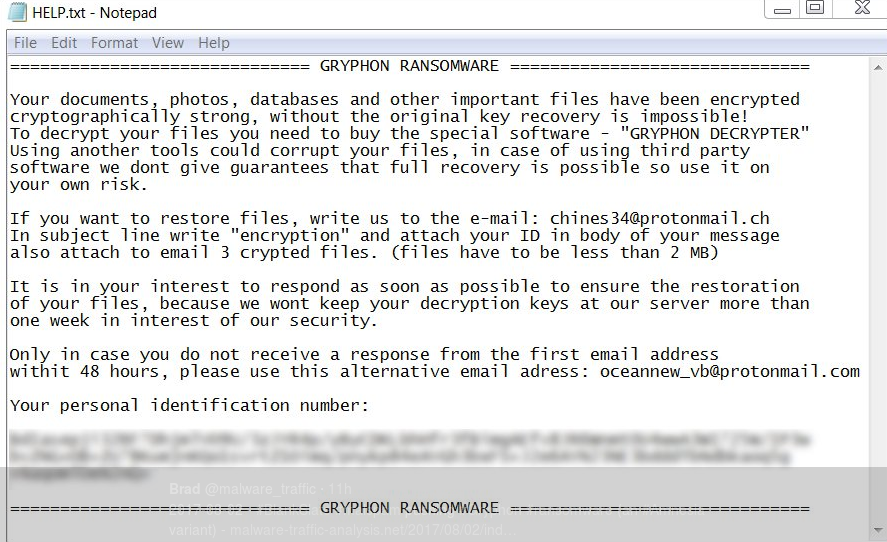
GRYPHON RANSOMWARE
Your documents, photos, databases and other important files have been encrypted
cryptographically strong, without the original key recovery is impossible!
To decrypt your files you need to buy the special software – “GRYPHON DECRYPTER”
Using another tools could corrupt your files, in case of using third party
software we dont give guarantees that full recovery is possible so use it on
your own risk.If you want to restore files, write us to the e-mail: [email protected]
In subject line write “encryption” and attach your ID in body of your message
also attach to email 3 crypted files. (files have to be less than 2 MB)It is in your interest to respond as soon as possible to ensure the restoration
of your files, because we wont keep your decryption keys at our server more than
one week in interest of our security.Only in case you do not receive a response from the first email address
withit 48 hours, please use this alternative email adress: [email protected]Your personal identification number:
The hackers extort the victims for a ransomware payment by promising that they can recover the affected files if the requested sum is paid. As no information is provided about a fixed sum we presume that the criminals are going to negotiate on the price depending on the quantity and quality of the affected files.
The victims should not contact the hackers and resort to follow our instructions to safely remove the .Gryphon virus and recover their data.
Remove .Gryphon Virus and Restore Data
WARNING! Manual removal of .Gryphon Virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
.Gryphon Virus – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps bellow are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
-
– Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
-
– Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover .Gryphon Virus Files
WARNING! All files and objects associated with .Gryphon Virus should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
DOWNLOAD .Gryphon Virus Removal ToolSpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
-
– Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



