In this article we give a brief overview of the potent Radium keylogger that is written in the Python programming language, learn more about its capabilities and the consequences it can provoke.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
About The Radium Python Keylogger
Keylogging is the malicious action of spying on the keyboard input of a target user. This is done in secret by malware applications that steal account credentials and passwords from the victims.
The Radium keylogger is a recent example of a potent solution that can be used by hackers to steal passwords and other sensitive information that is typed by the user. The program is written in the Python programming language which is popular among computer criminals.
Radium can spy on both applications and keystrokes. In addition it can produce screenshots of the user’s action like the CloudFanta malware. Radium uses a drive tree structure and can send the logs by email when configured by the hackers. In addition it can steal the stored passwords of the following programs and services – Chrome, Mozilla, Filezilla, Core FTP, CyberDuck, FTPNavigator, WinSCP, Outlook, Putty, Skype and Generic network access.
Radium can also steal cookies and gather specific system information – Internal and External IP, the output of ipconfig and the platform (system architecture).
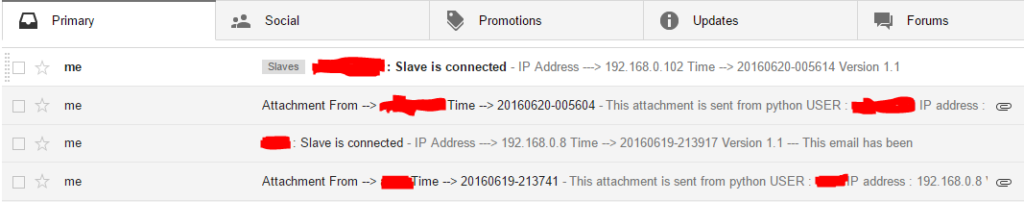
Radium Keylogger Mechanism of Action
The default configuration and behavior of the Radium keylogger is executed as its mechanism of action.
To begin execution of Radium the user needs to download the required dependencies:
- PyHook
- PyWin32
- Microsoft Visual C++ Compiler for Python
- PyInstaller
The next step is to set up the Gmail username and password and check the allowed connections. The user also needs to create a FTP server with a folder Radium where the binary file is stored, this includes the IP address, username and password. The passwords needs to be encoded in base64.
The originalfilename variable in the copytostartup() has to be set to the new version of the binary file.
The keylogs are mailed after 300 key strokes to the target email address and the screenshots after every 500 key strokes. These two settings cannot be changed.
The developers are currently working on the following features:
- Persistance
- Taking screenshots after a specific time. Making it keystrokes independent
- Webcam logging
- Skype chat history stealer
- Steam credential harvestor
What this means ultimately is that the Radium keylogger can be integrated in many different malware. You can protect yourself by using a quality anti-spyware solution.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



