An updated version of CryptoRoger ransomware has been discovered. The threat still using AES encryption and appends the extension .crptrgr to encrypted filenames. Cyber criminals standing behind CryptoRoger changed the way they contact the victims of the threat. They are now using Telegram instead of the uTox messenger.
This article provides information about the CryptoRoger ransomware infection, removal help, and decryption guidelines.
| Name |
CryptoRoger |
| File extension |
.crptrgr |
| Ransom |
0.5 BTC |
| Solution #1 |
CryptoRoger ransomware can be removed easily with the help of an anti-malware tool.It will clean your computer from the crypto-virus and protect you in the future. |
|
Solution #2 |
CryptoRoger ransomware can be removed manually. See the detailed tutorial below. |
| Distribution |
exploit kits, spam emails, malicious links. | </tr
Let’s Reveal Some Details of CryptoRoger Ransomware
The previous version of the threat was first detected by the security researcher S!Ri in June this year. The updated CryptoRoger version seems to have almost the same features as its predecessor. The significant modification is in the chat platform used for contact between the attackers and the victims. The malicious intenders have ditched uTox messenger and replaced it with Telegram.
Upon installation CryptoRoger scans all drives connected to the affected computer, searching for files that match its list of target file extensions. Once it finds matches with the data included in its configuration settings it utilizes strong AES-256 encryption algorithm to encode the file. At the end of this process it appends the extension .crptrgr to the original filename. If you are a victim of this crypto virus your file might look like similar to this one:
Common file types being target of ransomware viruses like CryptoRoger are:
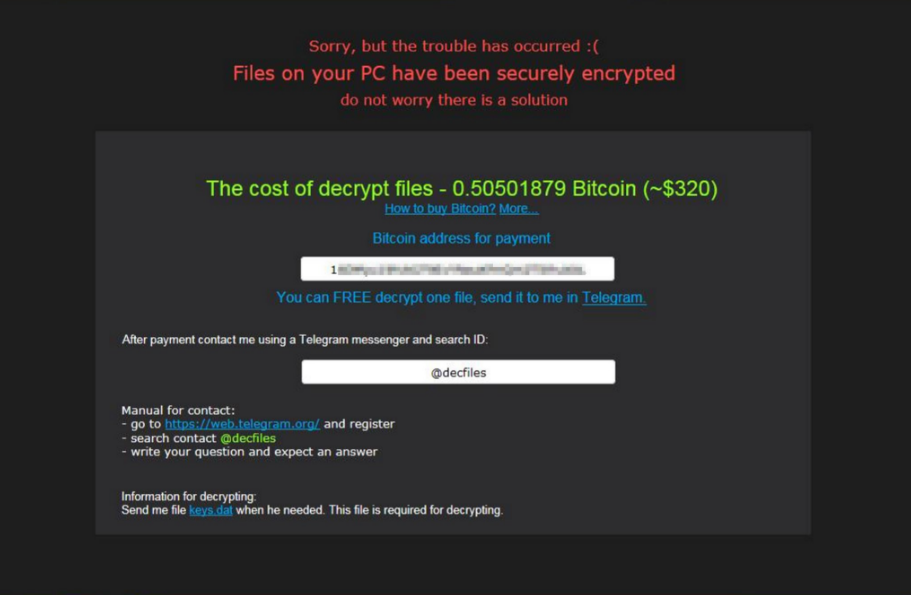
The next stage of CryptoRoger ransomware infection is to drop a ransom note which might be contained in an HTML file named ‘! Where_are_my_files!.html’. It is automatically displayed and aims to inform victims what has just happened with their computer and their stored data. Additionally it provides instructions on how to contact the attackers in order to pay the ransom for the decryption key. The ransom is nearly 0,5 BTC which is estimated at approximately $320. According to the renewed instructions victims should register in Telegram messaging app and then search the contact @decfiles.
Here is what the exact text of CryptoRotor’s ransom note reads:
“Sorry, but the trouble has occurred
Files on your PC have been securely encrypted
do not worry there is a solutionThe cost of decrypt files – 0.50501879 Bitcoin (~$320)
How to buy Bitcoin? More….
Bitcoin address for payment
You can FREE decrypt one file, send it to me in Telegram
After payment contact me using Telegram messenger and search ID:
@decfiles
Manual for contact:
– Go to https://web.telegram.org and register
– Search contact @decfiles
– Write your question and expect an answer
Information for decrypting:
Send me file keys.dat when he needed. This file is required for decrypting.”
Regarding your safety we recommend the restriction of any contact with the malicious intenders.
Other malicious files dropped by CryptoRoger ransomware could be:
- %AppData%\Microsoft\Windows\Start Menu\Programs\Startup\x.vbs
- %AppData%\files.txt
- %AppData%\keys.dat
- %AppData%\bg.jpeg
- %UserProfile%\CryptoRoger\{CryptoRoger’s primary executive}.exe
Another impact of the infection includes several modifications in Windows Registry Editor. The ransomware creates a key “CryptoRoger”. It adds several different values in it:
- HKCU\Software\CryptoRoger\
- HKCU\Software\CryptoRoger\AESFORUPRIVATE
- HKCU\Software\CryptoRoger\UPRIV
Furthermore, CryptoRoger may create a .vbs file in the Windows Startup folder in order to load its malicious files every time the Windows OS is started. Thus enables the encryption of all new files created during the last login.
Distribution Techniques
Distribution of CryptoRoger is most likely to be realized via spam emails that contain links to malicious websites. The links may be embedded in a button or hidden in a catchy word or phrase in order to provoke a click on it. Cyber criminals may try to obscure the malicious files of CryptoRoger ransomware by providing infected email attachments. They aim to make you curious of what the email is referring to and thus click on the link or open the attached file. The emails pretend to be sent by legitimate sources to mislead you.
The malicious links that cause CryptoRotor infection may be presented on social media posts and messages as well. Sometimes the malicious files may land on your computer through pop-up notifications for software updates.
One more way of distribution may be bundling. In some cases downloading freeware software may result in ransomware or other malware infection.
Remove CryptoRoger Ransomware Virus and Save Your .Crptrgr Files
CryptoRoger is developed to deal massive impact on the computer. Its malicious files on the system cause changes that don’t allow you to use the computer regularly. That’s why if you are a victim of CryptoRoger you should instantly remove all files and objects associated with it. With the instructions below we aim to help you with CryptoRoger’s removal and provide some preventive security measures.
Unfortunately, there is no free decrypter for CryptoRoger yet. However, make backup copies of all .crptrgr encrypted files and keep them until a decryption solution is available. Meanwhile, data recovery software may help you to recover some .crptrgr data.
CryptoRoger Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely CryptoRoger Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
-
1) Use present backups
2) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.



