An infection with the dangerous FRS virus leads to serious security issues. Victims can restore and protect their computers by following our complete removal guide.
Manual Removal Guide
Recover FRS Virus – Files
Skip all steps and download anti-malware tool that will safely scan and clean your PC.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
Distribution of FRS Virus
The FRS virus is being distributed against computer users using the most popular tactics. As only a small subset of samples have been identified at the moment it is not known which is the primary method. We presume that the hackers behind it are going to utilize different tactics in order to judge which is going to be the most succesful one.
A widely used approach is to insert the virus threat in email messages. These tactics allow for a wide range of scenarios, usually the data is either attached to the messages directly or linked in the body contents. The attackers utilize various strategies in order to coerce the victims into falling for the malware. Usually the messages pose as being sent by famous companies — in the case of hyperlinks the FRS virus can pose as a redirect to a counterfeit download sites. Direct downloads can pose as malware updates for the operating system or user-installed software.
The criminals can also upload the files to hacker-controlled pages and web scripts. A very wide range of different types can be observed: fake download pages, Internet portals, banners, pop-ups and etc.
The hackers may integrate the FRS virus into malware browser plugins also known as browser hjackers. Their primary aim is to redirect the victims to a hacker-controlled download page. This is done by modifying default configuration values such as the home page, search engine and new tabs page. The majority of cases are made compatible with most of the popular web browsers: Mozilla Firefox, Microsoft Edge, Google Chrome, Internet Explorer, Safari and Opera. The actual FRS virus is done in the first stages of infection.
Another popular strategy relies on the creation of malware software installers. They are made by taking the legitimate setup files and modifying it to include the FRS virus code. Usually the targets are popular software (creative apps, system utilities and games) both in their trial and free versions.

FRSV2 Virus – Technical Data
The FRS virus does not contain any signatures of any of the well-known malware families. It contains a built-in string called FIFCOM Corp. which may be the alias of the hacker group behind it. We assume that they are the ones responsible for it. No source code from open-source projects has been identified at this point.
The security analysis reveals that in a similar way to other recent viruses the FRS malware follows a several step delivery process. The first module that is launched is the information gathering one. Usually such components are configured to extract two different types of data — anonymous information gathered about the system and personal data about the victim users themselves:
- Anonymous Data — This type of information consists of information related to the installed hardware components and certain operating system configuration values.
- Personal Data — This type of information can directly expose the victim’s identity. The FRS virus is configured to look out for strings related to their name, address, phone number, interests, passwords and account credentials.
Another dangerous instance following its infection is the fact that it uses a built-in security bypass function. It can be used to counter the real-time engine of applications such as anti-virus products, sandbox and debugging environments and virtual machine hosts.
Impact of FRS Virus
The FRS virus does not contain any signatures of any of the well-known malware families. It contains a built-in string called FIFCOM Corp. which may be the alias of the hacker group behind it. We assume that they are the ones responsible for it. No source code from open-source projects has been identified at this point.
The infection module associated with the FRS virus infection has been found to spawn a lot of proceesses which have the ability to hook up to various system and user-installed applications. The virus module has the ability to load additional modules as well. The analysis also reveals that the harvested information can be relayed to the hacker controllers via a network connection. Further updates can embed a Trojan that can take over control of the victim machines. Such actions can also lead to the deployment of additional malware to the victim machines.
The FRS virus is able to cause dangerous system configuration changes such as access to system and user data. The virus module has also been found to read the terminal service related keys — if they are obtained the hackers can control the victim machine remotely without the use of any additional components.
Once all malware components have completed their the ransomware module is launched. It starts to encrypt target files using a powerful cipher. At the moment the captured samples affect the following file type extensions:
.avi, .bmp, .exe, .flv, .gif, .lnk, .m4a, .mkv, .mp4, .odp, .ods, .pdf, .png, .ppt, .rtf, .swf, .wav
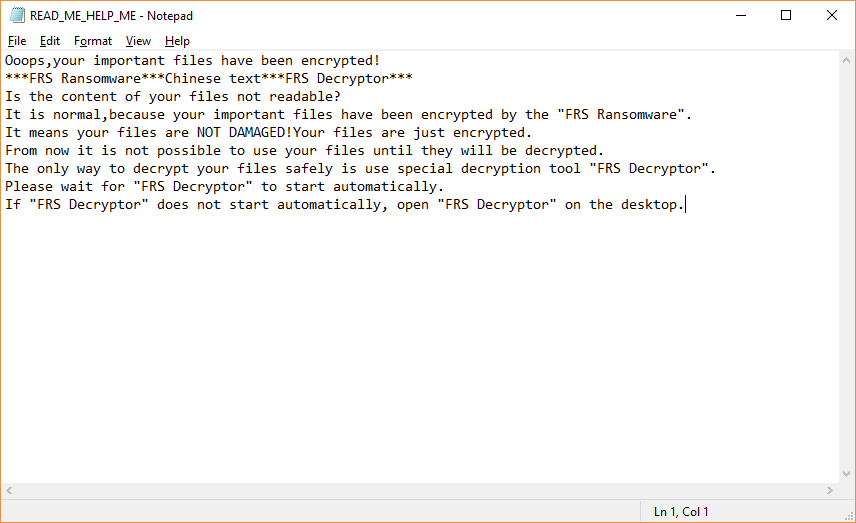
As a consequence all data is renamed with the .FRS extension. A ransomware note is created in several formats: an image (READ_ME_HELP_ME.png) and a text file (READ_ME_HELP_ME.txt) containing a similar message:
Ooops,your important files have been encrypted!
***FRS Ransomware***Chinese text***FRS Decryptor***
Is the content of your files not readable?
It is normal,because your important files have been encrypted by the “FRS Ransomware”.
It means your files are NOT DAMAGED!Your files are just encrypted.
From now it is not possible to use your files until they will be decrypted.
The only way to decrypt your files safely is use special decryption tool “FRS Decryptor”.
Please wait for “FRS Decryptor” to start automatically.
If “FRS Decryptor” does not start automatically, open “FRS Decryptor” on the desktop.
Remove FRS Virus and Restore PC
Please note that paying the requested ransom fee to cyber criminals does not really solve your problem with FRS Virus crypto virus. In fact, you only encourage hackers to continue spreading ransomware of this kind. Instead, you must remove the threat immediately, and only then look for optional ways to recover your data.
WARNING! Manual removal of FRS Virus ransomware virus requires being familiar with system files and registries. Removing important data accidentally can lead to permanent system damage. If you don’t feel comfortable with manual instructions, download a powerful anti-malware tool that will scan your system for malware and clean it safely for you.
DOWNLOAD Anti-Malware ToolFRS Virus – Manual Removal Steps
Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently. The steps below are applicable to all Windows versions.
1. Hit the WIN Key + R
2. A Run window will appear. In it, write msconfig and then press Enter
3. A Configuration box shall appear. In it Choose the tab named Boot
4. Mark Safe Boot option and then go to Network under it to tick it too
5. Apply -> OK
Show Hidden Files
Some ransomware threats are designed to hide their malicious files in the Windows so all files stored on the system should be visible.
1. Open My Computer/This PC
2. Windows 7
-
– Click on Organize button
– Select Folder and search options
– Select the View tab
– Go under Hidden files and folders and mark Show hidden files and folders option
3. Windows 8/ 10
-
– Open View tab
– Mark Hidden items option

4. Click Apply and then OK button
Enter Windows Task Manager and Stop Malicious Processes
1. Hit the following key combination: CTRL+SHIFT+ESC
2. Get over to Processes
3. When you find suspicious process right click on it and select Open File Location
4. Go back to Task Manager and end the malicious process. Right click on it again and choose End Process
5. Next, you should go folder where the malicious file is located and delete it
Repair Windows Registry
1. Again type simultaneously the WIN Key + R key combination
2. In the box, write regedit and hit Enter
3. Type the CTRL+ F and then write the malicious name in the search type field to locate the malicious executable
4. In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Click for more information about Windows Registry and further repair help
Recover FRS Virus- Files
WARNING! All files and objects associated with FRS Virus ransomware virus should be removed from the infected PC before any data recovery attempts. Otherwise the virus may encrypt restored files. Furthermore, a backup of all encrypted files stored on external media is highly recommendable.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
1. Use present backups
2. Use professional data recovery software
Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
3. Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

4. Restore your personal files using File History
-
– Hit WIN Key
– Type restore your files in the search box
– Select Restore your files with File History
– Choose a folder or type the name of the file in the search bar
– Hit the “Restore” button



