New malware has been detected to infect users. Its name is Alcatraz Locker and is a very serious crypto-virus from the ransomware group. It encrypts files using the AES-256 algorithm and then appends the extension .alcatraz to the locked files. The ransom note demands a ransom of 0.5 bitcoins which amounts to an estimated value of over $350. There is given time for realizing the payment, and after that, the decryption key will be deleted.
Alcatraz Locker is an infection that is hard to deal with. This article is focused on the harmful crypto virus and aims to help you remove the threat and recover .alcatraz encrypted files.
| Name |
Alcatraz Locker |
| File extension |
.alcatraz |
| Ransom |
0.5 BTC |
| Solution #1 |
Alcatraz Locker ransomware can be removed easily with the help of an anti-malware tool.It will clean your computer from the crypto-virus and protect you in the future. |
|
Solution #2 |
Alcatraz Locker ransomware can be removed manually. See the detailed tutorial below. |
| Distribution |
Rig exploit kit, spam emails, malicious links. | </tr
Alcatraz Locker Ransomware in Detail
Once Alcatraz Locker successfully executes its malicious files, the encryption of the files begins. At the end of this process, all encoded files cannot be properly opened by any program. At the end of their names is appended the extension .alcatraz. When this happens, the files become “prisoners” of Alcatraz. The ransomware is likely to target the most frequently used file types like documents, video files, pictures or audio files.
Upon the installation, Alcatraz also drops a file Ransomed.html which is its ransom note. After the encryption, the ransom note is displayed on the screen. It begins with “ALL YOUR DATA ARE ENCRYPTED” and provides victim’s personal ID.
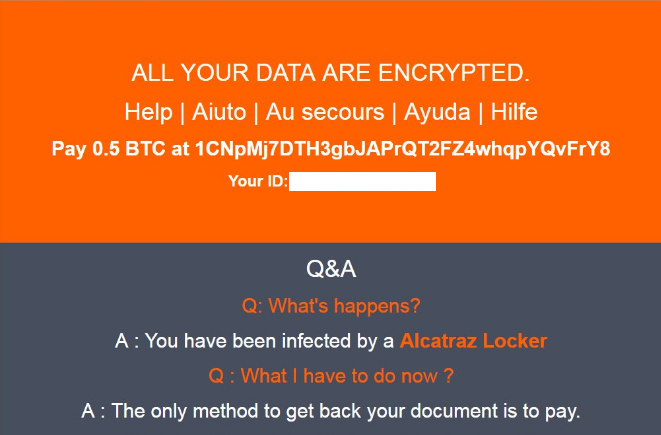
The malicious intenders demand 0.5 BTC from victims in order to deliver them the private key which is needed for .alcatraz data decryption. Hackers give a deadline for making the ransom transaction. After this period the decryption key is deleted. However, it’s better not to pay the ransom to the cyber criminals as the ransomware may be in development, so there is no guarantee that they will send a key. If they send the key anyway, it might not be working at all. Read further and learn how to deal safely with Alcatraz Locker ransomware.
Alcatraz Ransomware Distribution
According to Trend Micro researchers, Alcatraz ransomware is being pushed by Rig exploit kit. However, the infection can infiltrate the system using different cunning approaches. One popular way for ransomware distribution is via spam emails. The email may pretend to be sent from legitimate and well-known sources like PayPal, Windows, and your bank. The threat could be hidden in the body of the message, in provided malicious link or in a vicious attachment. If you can’t determine if the link is malicious or the attachment hides malware files that will compromise your system you could upload them to VirusTotal or any other online malware scanning service. The results may help you avoid being a victim of ransomware. In some cases, landing on a compromised website may lead to concealed installation of the malicious Alcatraz Locker’s files. Be careful and think wisely before clicking on suspicious advertisements and links. Pay attention when the next software update notification pops up, sometimes the malicious intenders may mask successfully Alcatraz Locker ransomware as well as other malware in fake software notifications.
How to Deal with Alcatraz Locker Ransomware Infection
Alcatraz Locker is a difficult crypto-virus to deal with. However, if you check the instructions below, you can learn how to remove all files and objects associated with Alcatraz Locker. Furthermore, the researchers are currently analyzing the source code of this nasty ransomware for weaknesses. So we advise you to avoid ransom payment and wait for a free decryption solution. It is good to ensure that your computer is malware-free. Then make backup copies of the encrypted data and store them on external devices until a solution is found. Meanwhile, data recovery software could help for the file decryption.
Avast security experts have released free decryption tool for Alcatraz Locker ransomware. Once you complete the removal of all Alcatraz Locker malicious files you can download the decryptor, follow the steps and decrypt all your .alcatraz files.
In order to prevent Alcatraz Locker ransomware infection and strengthen your computer security be sure to have installed anti-malware software which is up to date. Additionally, installing anti-ransomware software is a step further for better computer security.
Alcatraz Locker Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Alcatraz Locker Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
-
1) Use present backups
2) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.



