A recently detected sample of the infamous Fantom ransomware uncover that the bad guys have made some modifications to its source code and now the threat has а new ransom note. Fantom ransomware is known to use the malicious file extension .fantom. The threat is based on the EDA2 open source code and is still unable to be freely decrypted. The crooks invoke victims to contact them to fantomd12@yandex(.)ru sending the ID_KEY displayed in the ransom note so they can send them back a decryption key in return of a ransom payment.
| Name |
Fantom Ransomware |
| File Extensions |
.fantom | Ransom |
Varies |
| Solution #1 |
Use the help of an anti-malware tool to remove Fantom ransomware and any additional cyber-security threats. |
|
Solution #2 |
Fantom ransomware can be removed manually. See the detailed tutorial below. This solution requires good computer skills. |
| Distribution |
Spam emails, malicious URLs, malicious attacments, exploit kits, freeware. |
The Fantom Ransomware Infection Progress
Once the malicious payloads of Fantom ransomware are running on your computer, you may witness a window that locks your screen informing you that critical Microsoft Windows updates are configuring.
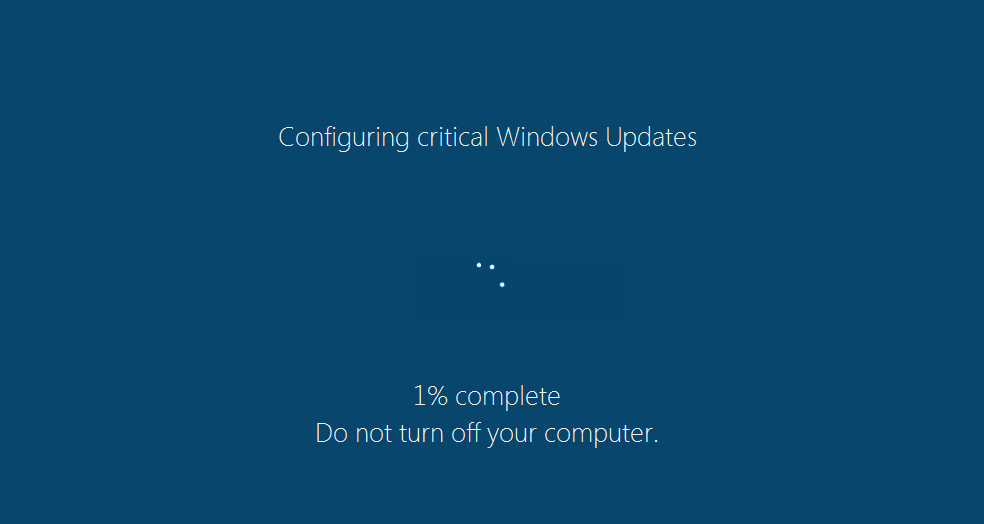
Meanwhile, your files are silently being locked in the background. If you suspect that this process is malicious, you could close the screen using the Ctrl + F4 key combination. However, the Fantom ransomware is still running in the background and is encrypting your files. Fantom ransomware is programmed to use combination of two strong encipher algorithms – RSA-4096 and AES-265 while encrypting particular data. The list of Fantom’s target file types is pretty long as it scans for and encrypts all files that have one of the following extensions:
All affected files are unable to be opened by any program, and you could know that a file is encrypted by Fantom ransomware when you see the file extension .fantom appended to the original filename. Even if you try to change it by writing the proper one, the file is still unusable.
However, the threat has been first detected back in August, and since then it has been subjected to several changes. So except the extension .fantom as a sure sign of Fantom ransomware infection the extensions .locked and .locked4 are also hints of the same crypto virus.
A part of Fantom infection process is also the replacement of your desktop wallpaper with an image that looks like this:
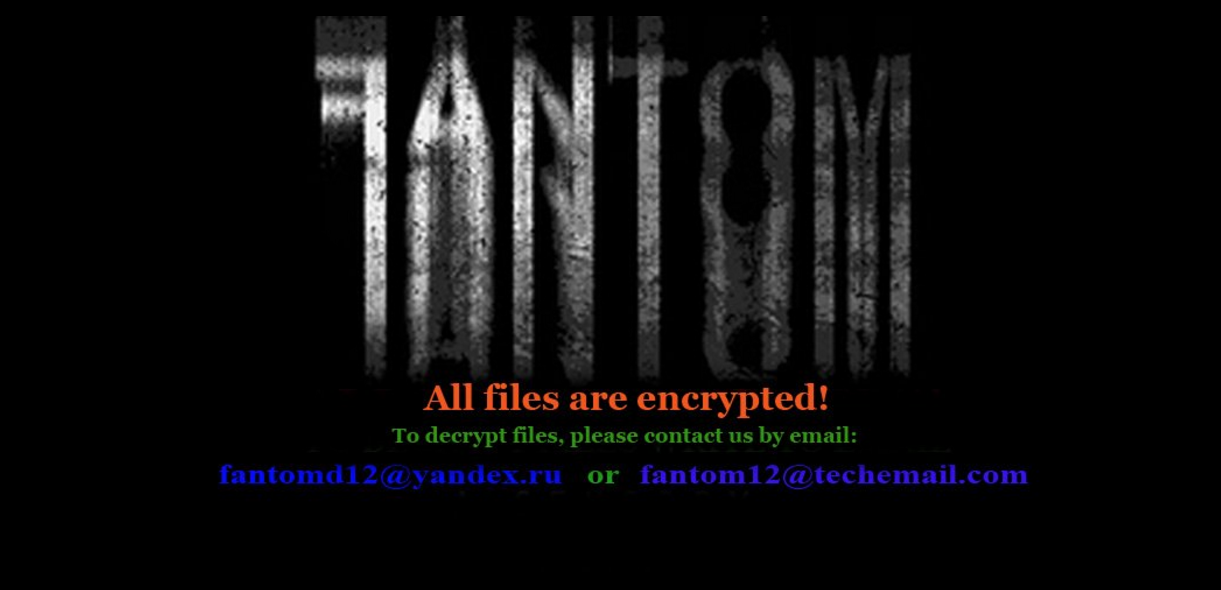
The file is probably saved into %UserProfile% folder, and the depicted text reads:
“All files are encrypted!
To decrypt files, please contact us by email:
[email protected] or [email protected] ”
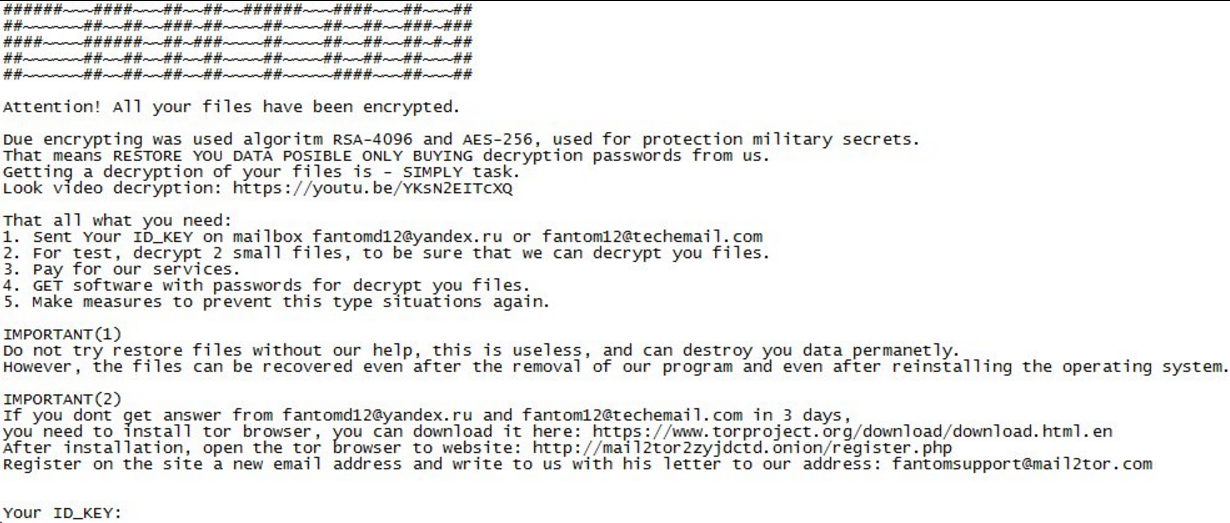
Next, the threat drops a file named “README.txt” that serves as its ransom note. The file itself contains the following text:
“Attention! All your files have been encrypted.
Due encrypting was used algorithm RSA-4096 and AES-265, used for protection military secrets.
That means RESTORE YOU DATA POSIBLE ONLY BUYING decryption passwords from us.
Getting a decryption of your files is – SIMPLY task.
Look video decryption: https://youtu.be/YKsN2EITcXQ
That all what you need:
1. Send Your ID_KEY on mailbox [email protected] or [email protected]
2. For test, decrypt 2 small files, to be sure that we can decrypt you files.
3. Pay for our services.
4. GET software with passwords for decrypt you files.
5. Make measures to prevent this type situations again.
IMPORTANT(1)
Do not try restore files without our help, this is useless, and can destroy you data permanently.
However, the files can be recovered even after the removal of our program and even after reinstalling the operating system.
IMPORTANT(2)
If you dont get answer form [email protected] and [email protected] in 3 days, you need to install tor browser, you can download it here: https://www.torproject.org/download/download
After installation, open the tor browser to website: http://mail2tor2zyjdctd.onion/register.php
Register on the site a new email address and write to us with his letter to our address: [email protected]
Your ID_KEY: ____________________________”
The new thing in the ransom note is a link that leads to a YouTube video called “Fantom decryptor”. It represents a demonstration of how the restore process of .fantom locked files goes.
There is no information about the expected ransom amount but only instructions how to contact the crooks in order to proceed further.
As becomes clear from the text in the “README.txt” ransom note the files are still decryptable even when Fantom ransomware is completely removed from the system. So we think that it’s worth getting rid of all malicious files and objects associated with Fantom ransomware and then experiment with alternative data recovery solutions like Recuva, Shadow Explorer, any professional data recovery software instead of paying the ransom to the cyber criminals.
Removal of Fantom Ransomware
If you somehow are trapped by the malicious Fantom ransomware infection now, it is time to remove it completely from your computer. The guide below will take you through a consistent step-by-step removal process that will help you to cope with infection in the best way.
In case that you choose to attempt the manual approach, you can check our article about the previous versions of Fantom ransomware and find out more specific malicious files and objects linked to the virus.
However, the automatic approach will surely avoid system breaking and notably, reduce removal time and effort.
Fantom Ransomware Removal
For a faster solution, you can run a scan with an advanced malware removal tool and delete Fantom completely with a few mouse clicks.
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely Fantom Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover Encrypted Files
-
1) Use present backups
2) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

STEP VII: Preventive Security Measures
-
1) Enable and properly configure your Firewall.
2) Install and maintain reliable anti-malware software.
3) Secure your web browser.
4) Check regularly for available software updates and apply them.
5) Disable macros in Office documents.
6) Use strong passwords.
7) Don’t open attachments or click on links unless you’re certain they’re safe.
8) Backup regularly your data.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



