The FileFrozr Ransomware is a dangerous new RaaS threat which can be removed by following our in-depth guide.
FileFrozr Ransomware Description
Security specialists discovered the FileFrozr ransomware which is a new RaaS (Ransomware as a service) solution. This is a newly devised tool which can be used to both create new malware strains and launch coordinated attacks against predefined targets.
The threat was discovered on a well-known underground hacker forum where it is being advertised. The following text has been posted by its creator (a hacker under the alias frozr):
FILE FROZR is a great security tool that encrypts most of your files in several minutes.
Fast, stable, and affordable crypto-locker.
Auto-buy, low price, undetectable load while working, TOR support, 250+ extensions, unmatched support, multithreaded, online builder, server side obfuscation. Bypass BitDefender and Malwarebytes Anti-Ransomware.
Encrypts user data using safe implemented AES-256 and RSA-4096, each file encrypts with it own unique key.
50$ Discount on sales start!
The criminal has even created a site which is used to advertise the RaaS on the anonymous TOR network. From it we can learn more about the virus. According to the creator it is written in the C# programming language from scratch which means that no prior code snippets from other malware families are used. Such tactics make it more difficult for security software to spot the infection if the engines do not possess adequate heuristic algorithms which can perform in-depth analysis of the running applications and processes.
Based on the configuration done by the operators of the virus the built-in encryption engine can use the AES-256 or RSA-4096 ciphers to target a predefined list of target file extensions. They usually include the most commonly used user data – archives, music, photos, videos, databases and etc. The RaaS generates unique private keys which are obfuscated and stored in the private C&C malicious servers.
When the hackers purchase access to the FileFrozr Ransomware they are also automatically are subscribed to future updates of the builder. The hacker has posted a roadmap of upcoming features which include the following:
- Clean Space Wiping – This feature makes changes to the hard disk by taking up space on the hard drives which can render performance and make some applications stop working.
- Speech Synthesis – The addition of a speech synthesizer makes the virus infection appear more dangerous as the generated computer voice can can have a psychological impact on the victims.
- The addition of other ciphers – The hacker behind the RaaS will provide new ciphers which will be available to the criminal operators.
- Offline Version – A future version of the FileFrozr ransomware will being an offline version which can impact the systems without an active Internet connection.
- ASP.NET-based panel – A revamped administrative panel based on the ASP.NET technology is promised.
- UAC Bypass – In the upcoming version of the ransomware a UAC Bypass feature is going to be included which will be able to achieve privileged access to the system without any user interaction post-infection.
- Updated Obfuscator – The roadmap includes an updated obfuscator code.
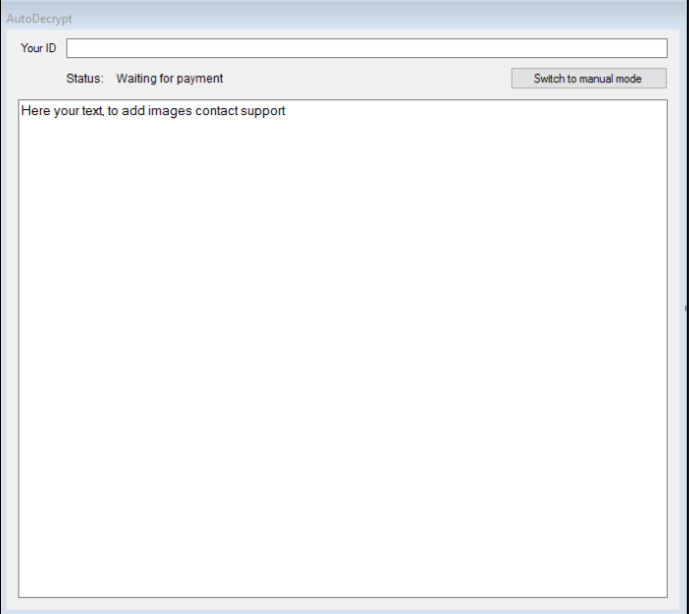
When the payment to the RaaS builder has been complete the operators get access to a web panel which is used to view the status of the infected machines – their unique key ID, ransomware payments and other information. The hackers also receive access to the decryption application which is delivered in two versions – a manual and an automatic one which can be customized to represent the crafted ransomware strain.
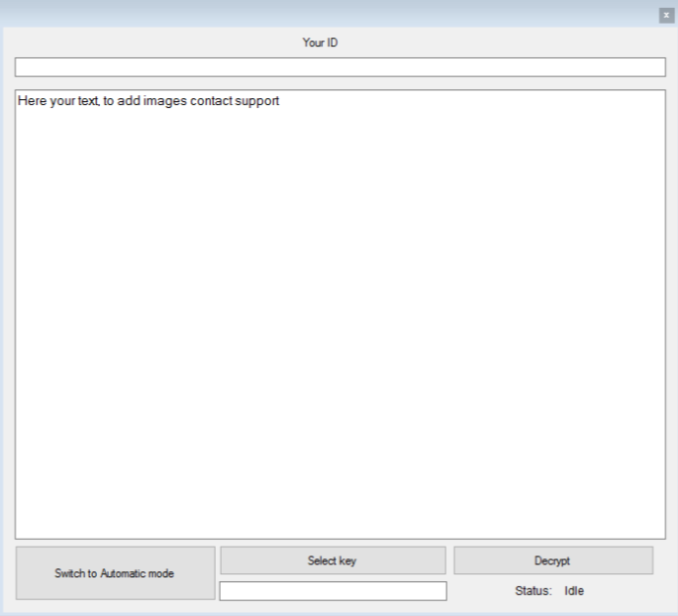
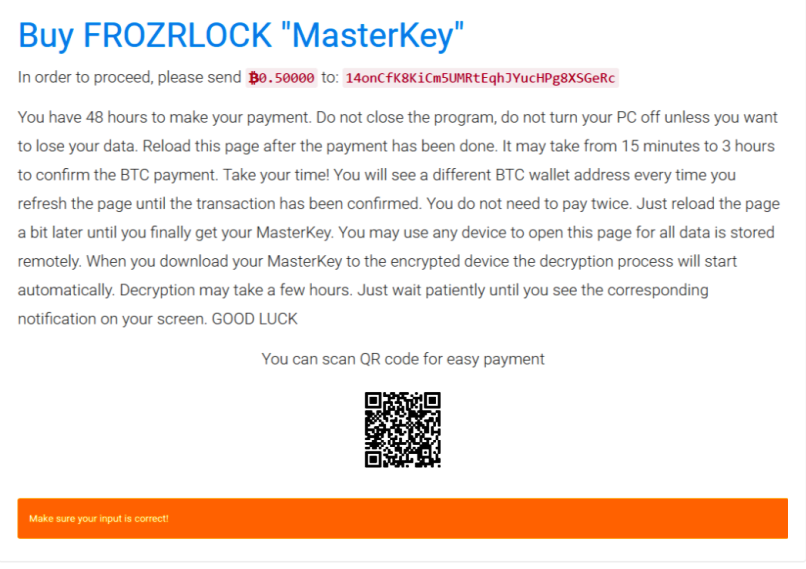
When the user comes in contact with the virus they are immediately affected by the built-in encryption engine. The default configuration includes a list of 250 file type extensions which feature the most commonly used data – archives, photos, videos, music, configuration files, backups and etc. A sample ransomware note reads the following:
Buy FROZRLOCK “MasterKey”
In order to proceed, please send B0.50000 to: XXXXXXXXXXXXXXXXXXXXXX
You have 48 hours to make your payment. Do not close the program, do not turn your PC off unless you want
to lose your data. Reload this page after the payment has been done. It may take from 15 minutes to 3 hours
to confirm the BTC payment. Take your time! You will see a different BTC wallet address every time you
refresh the page until the transaction has been confirmed. You do not need to pay twice. Just reload the page
a bit later until you finally get your MasterKey. You may use any device to open this page for all data is stored remotely.
When you download your MasterKey to the encrypted device the decryption process will start automatically. Decryption may take a few hours.
Just wait patiently until you see the corresponding notification on your screen. GOOD LUCKYou can scan QR code for easy payment
From this information we can conclude that the following characteristics are associated with the customized strains:
- Customizable Ransomware Fee – The hacker operators can choose a custom ransomware fee depending on the attack campaign.
- Rich Text Formatting – The ransomware notes can be customized to display rich text formatting, videos and photos.
- Variable Ransomware Fee – The ransomware fee can be customized according to the infected host or can be dynamically set depending on the quantity or quality of the affected data.
FileFrozr Ransomware Distribution
The FileFrozr Ransomware strains can be distributed via various strategies. One of the most popular ones is the use of phishing email messages via hacked or hacker-controlled servers and accounts. The operators of this scheme use familiar looking messages that pose as being sent by a famous company or government institution. Usually in the body of the messages there are hyperlinks that lead to the virus. Other cases include direct file attachments of the payload or the use of infected documents that deliver the FileFrozr ransomware strains upon interaction with them via dangerous scripts (macros).
Malicious ad networks, browser hijackers and hacker-controlled sites can also lead to an infection. Usually they are encountered when a victim computer has been infiltrated by a browser hijacker – a dangerous web browser extension (most of them work with the most popular applications such as Mozilla Firefox, Google Chrome, Internet Explorer and Microsoft Edge). They change the settings of the browsers and modify them to point to a hacker-controlled site. The default homepage, new tabs page and search engine may be modified, as well as any history ,stored account credentials or cookies are stolen by the hackers.
Infected software installers are found often on such download portals which are either hacker-controlled or hacked. BitTorrent trackers where pirate content is usually distributed is the other culprit.
Depending on the chosen target list the hackers in posession of the strain can use other strategies at will.
Summary of the FileFrozr Ransomware
| Name |
FileFrozr Ransomware |
| File Extensions |
|
| Ransom |
Varies |
| Easy Solution |
You can skip all steps and remove FileFrozr Ransomware ransomware with the help of an anti-malware tool. |
|
Manual Solution |
FileFrozr Ransomware ransomware can be removed manually, though it can be very hard for most home users. See the detailed tutorial below. |
| Distribution |
Spam Email Campaigns, malicious ads & etc. |
FileFrozr Ransomware Ransomware Removal
STEP I: Start the PC in Safe Mode with Network
This will isolate all files and objects created by the ransomware so they will be removed efficiently.
-
1) Hit WIN Key + R

- 2) A Run window will appear. In it, write “msconfig” and then press Enter
3) A Configuration box shall appear. In it Choose the tab named “Boot”
4) Mark “Safe Boot” option and then go to “Network” under it to tick it too
5) Apply -> OK
Or check our video guide – “How to start PC in Safe Mode with Networking”
STEP II: Show Hidden Files
-
1) Open My Computer/This PC
2) Windows 7
-
– Click on “Organize” button
– Select “Folder and search options”
– Select the “View” tab
– Go under “Hidden files and folders” and mark “Show hidden files and folders” option
3) Windows 8/ 10
-
– Open “View” tab
– Mark “Hidden items” option

4) Click “Apply” and then “OK” button
STEP III: Enter Windows Task Manager and Stop Malicious Processes
-
1) Hit the following key combination: CTRL+SHIFT+ESC
2) Get over to “Processes”
3) When you find suspicious process right click on it and select “Open File Location”
4) Go back to Task Manager and end the malicious process. Right click on it again and choose “End Process”
5) Next you should go folder where the malicious file is located and delete it
STEP IV: Remove Completely FileFrozr Ransomware Ransomware Using SpyHunter Anti-Malware Tool
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
STEP V: Repair Windows Registry
-
1) Again type simultaneously the Windows Button + R key combination
2) In the box, write “regedit”(without the inverted commas) and hit Enter
3) Type the CTRL+F and then write the malicious name in the search type field to locate the malicious executable
4) In case you have discovered registry keys and values related to the name, you should delete them, but be careful not to delete legitimate keys
Further help for Windows Registry repair
STEP VI: Recover FileFrozr Files
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter
How To Restore FileFrozr Files
- 1) Use present backups
- 2) Use professional data recovery software
-
– Stellar Phoenix Data Recovery – a specialist tool that can restore partitions, data, documents, photos, and 300 more file types lost during various types of incidents and corruption.
- 3) Using System Restore Point
-
– Hit WIN Key
– Select “Open System Restore” and follow the steps

- 4) Restore your personal files using File History
-
– Hit WIN Key
– Type “restore your files” in the search box
– Select “Restore your files with File History”
– Choose a folder or type the name of the file in the search bar

- – Hit the “Restore” button
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunter



