
Computer security experts are now engaged in a worldwide battle to prevent further damage and restore the computers and networks affected by the dangerous WannaCry ransomware iteration. The malware took its toll on thousands of victims thanks to a large-scale distribution campaign. To learn the reasons behind success of WannaCry virus we need to take a deep look into its origins, technical characteristics and infection tactics.
Origins Of The WannaCry Virus Threat
The latest iteration of the WannaCry virus is merely an evolved version of the core malware threat. It follows the typical malware behavior associated with most viruses of this type. Upon infection the virus starts to encrypt commonly used data: documents, photos, videos, configuration files, archives and etc. A strong cipher based on the AES standard is used to process the files, they are also renamed using the .wcry extension. To prevent data recovery the criminals also delete all found Shadow Volume Copies. This prevents file recovery without the use of a professional-grade solution.
One of the updated versions also institutes a lockscreen that prevents normal user interaction with the infected computer until the virus is completely removed. The hackers link and distribute a “decryptor” application which contains detailed instructions on restoring the computers by paying the ransomware fee. The criminal operators demand the initial sum of 300 US Dollars payable in the Bitcoin digital currency. Two social engineering tricks are also employed:
-
The hackers pressure the users by employing a short time limit. If the payment is not received until then the amount is doubled.
-
The hackers employ a final time limit. It is usually a week, if the money is not sent until then then the private decryption key is deleted from the remote servers.
The primary distribution method of the WannaCry ransomware is the use of phishing email spam messages. The hackers coordinate large-scale campaigns that attempt to trick the victims into infecting themselves with the virus.
The WannaCrypt0r 2.0 Virus In The Spotlight
The WannaCrypt0r 2.0 ransomware which is the perpetrator behind the mass attacks in the last few days is the newest version of the malware family. Similar to its parent it seeks to encrypt user data and extort the victims for a ransomware payment. There are some new additions that set it apart from previous versions:
-
The Virus Sets a Persistent Environment – The virus engine modifies key Windows settings and registry values that monitors the system for changes by the user or system applications. This effectively prevents manual removal options and the victims can only remove the infection with an automated anti-malware solution.
-
Backup Ransomware Note – In case the the main lockscreen application is removed from the computer the virus displays a backup ransomware note that supplies the necessary information about the infection to the victims. The hackers use the same social engineering tricks to extort the victims to make the dangerous payment.
-
Information Harvesting – The new version is capable of harvesting sensitive information from the victim machines. The virus engine can modify essential Microsoft Windows settings that can disable functionality or make certain applications and services stop working altogether.
-
System Modification – In the majority of cases, complex malware such as the WannaCrypt0r 2.0 ransomware virus also lead to significant performance issues. Threats like this one can also be used to deliver additional viruses to the infected hosts.
-
Multi-language support – The fact that the virus supports more than 28 languages and has provided a fully-translated version of the ransomware note to include the majority of targets adds to the success of the malware.
-
The TOR Anonymous Network Is Used for Communication – The criminal operators of the malware use the TOR anonymous network as the medium of communication. All support messages are relayed through a hacker-controlled gateway.
Unlike previous versions a large part of the infections were made due to a vulnerability exploit. The hackers took advantage of thousands of computers that were not patched properly and ran older versions of the Microsoft Windows operating system. The company issued patches back in March. The criminals used the MS17-010 vulnerability with automated testing frameworks. This is the reason why we recommend that all users constantly update all of their software to the latest available version.
Fake WannaCry Viruses Start To Spread
Soon after the WannaCry ransomware virus started to infiltrate computer networks on a worldwide scale the criminals started to create imitations of it. Its important to note that the impostors can use the same infection patterns or alternative methods to spread the malicious files. The fake WannaCry ransomware may be categorized in several types:
-
Total Copies – They imitate the original WannaCry virus to a maximum extent. The subtle differences can only be detected by performing a detailed security analysis.
-
Design Derivatives – This category applies to unrelated viruses that use the design of the ransomware note.
-
Name Impostors – Such malware use names that resemble the WannaCry ransomware family. However they are not part of them and attempt to fool the victims by extorting them using the same pressure tactics used by the popular virus.
WannaCry Ransomware Infections Prevention
Computer users can prevent an active infection by following some of the basic security tips:
-
Employ Protection – Users should use a quality anti-spyware solution to protect their computers from incoming infections. The advanced products feature both a signature and behavior based engine which can guard against all sorts of viruses.
-
Don’t Interact With Untrusted Mail and Files – One of the main infection strategies associated with the threat is its distribution through phishing emails. The hackers distribute template-based messages that appear as being sent by a legitimate company or government institution. The emails may contain the payload directly as an attachment or linked somewhere in the body content. Hackers can also distribute it using a medium – infected office documents masquerading as data of user interest or malicious software installer bundles.
-
Disable Vulnerable Services – In cases where the necessary patch cannot be installed the system administrators can disable the Samba Sharing service.
-
Stay Updated – Like other famous malware families once a particular threat has gained popularity the computer hackers will create follow-up derivatives. You can subscribe to our newsletter to receive alerts on all the latest computer viruses and security news.
-
Microsoft Guidance – Microsoft published an extensive blog post detailing the dangers associated with the WannaCry virus. In their advisory the company states that the impact of the threat is so large that they have even released a patch for Windows XP – a version of their operating system which is no longer supported.
Ongoing WannaCry 2.0 Virus Infections
One of the characteristics about the new WannaCry 2.0 virus is that it contains a serious flaw. Security experts discovered that even though the ransomware has used a dangerous exploit technique the developers behind it have left a vulnerability in the engine itself. The discovered flaw allowed malware specialists to create a kill-switch that effectively lowered the infection ratio. MalwareTech discovered that the programmers behind that the virus devised a special strategy for emergency shut down of the main strains. The security community quickly reacted and transferred the domain to the specialist. Soon after the infections were significantly lowered by volume.
There are two problems that are associated with this approach:
-
It Provides Only a Temporary Solution – One of the theories when it comes to the kill-switch is that it has been placed to intentionally stop the virus from spreading when anti-analysis targets are presumed. The core WannaCry 2.0 virus does not feature such a module built-in rather it depends on the kill-switch to prevent it from being analyzed. If the domain goes down for any reason then the infections will start once again.
-
Derivatives Are Not Affected – The kill-switch is not apparent in derivatives and further modifications of the WannaCry 2.0 virus.
Further WannaCry 2.0 Attacks Are Expected
Even though the large-scale email campaign was partly halted by the kill-switch issued by the security experts the researchers suspect that a new wave is coming soon. Note that the kill-switch does not prevent attacks in cases where the virus is being distributed from a hacker-controlled site, P2P network or a direct download. If the domain is blocked by a firewall or the Internet service provider or the traffic is routed through a proxy, then the correct network communication is not properly established. The criminals can also take down the kill-switch domain by using a DDOS attack, a well-organized botnet attack can cause the issue.
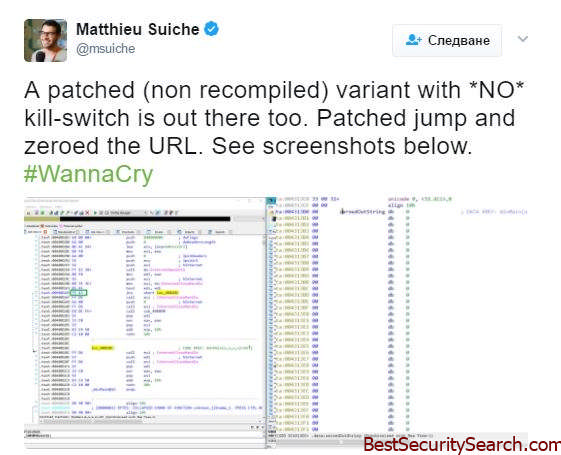
The security expert Matthieu Suiche confirmed that a new iteration of WannaCry 2.0 has been released in the wild that does not contain the kill-switch domain feature. It uses the SMB exploit that Microsoft warned about (see above). In addition they believe that the new incarnation is not related to the original developer team.
The WannaCry family has proved to be very successful and this is a major reason for developing new iterations of the threat. We suspect that the new versions of the family are going to include dangerous new modules such as information harvesting and remote control of the affected machines. If the hackers switch infection tactics into using advanced worms and other similar malware then an evolved version of WannaCry can be very hard to resist.
SpyHunter anti-malware tool will diagnose all current threats on the computer. By purchasing the full version, you will be able to remove all malware threats instantly. Additional information about SpyHunter / Help to uninstall SpyHunterh



